As a lot of as 5 security vulnerabilities have been resolved in Aethon Tug clinic robots that could permit remote attackers to seize management of the devices and interfere with the well timed distribution of medicine and lab samples.
“Profitable exploitation of these vulnerabilities could trigger a denial-of-service affliction, allow for complete control of robot features, or expose sensitive information and facts,” the U.S. Cybersecurity and Infrastructure Security Company (CISA) said in an advisory posted this week.
Aethon TUG good autonomous cell robots are applied in hospitals all-around the earth to supply medicine, transport clinical supplies, and independently navigate around to conduct distinctive jobs such as cleaning floors and amassing meal trays.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Collectively dubbed “JekyllBot:5” by Cynerio, the flaws reside in the TUG Homebase Server ingredient, efficiently allowing for attackers to impede the shipping and delivery of medicines, surveil patients, team, and hospital interiors by its integrated digicam, and acquire accessibility to confidential details.
Even even worse, an adversary could weaponize the weaknesses to hijack authentic administrative person sessions in the robots’ on the net portal and inject malware to propagate further more attacks at health care services.
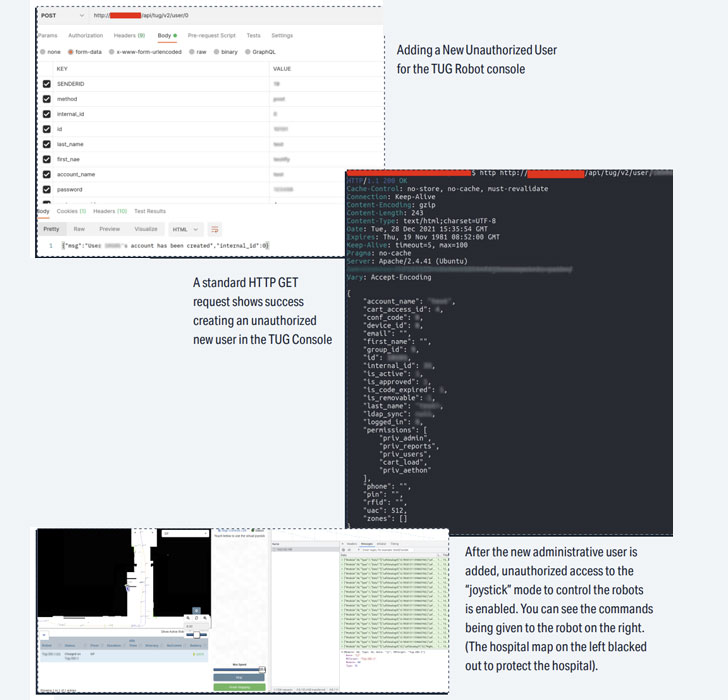
The exploitation of the flaws could have presented “attackers an entry stage to laterally shift by way of medical center networks, conduct reconnaissance, and inevitably carry out ransomware attacks, breaches, and other threats,” the health care IoT security agency explained.
The checklist of shortcomings, which were being learned late last 12 months in the course of an audit on behalf of a healthcare supplier consumer, is under –
- CVE-2022-1070 (CVSS rating: 9.8) – An unauthenticated attacker can hook up to the TUG House Base Server websocket to acquire manage of TUG robots.
- CVE-2022-1066 (CVSS score: 8.2) – An unauthenticated attacker can arbitrarily increase new buyers with administrative privileges and delete or modify current customers.
- CVE-2022-26423 (CVSS score: 8.2) – An unauthenticated attacker can freely access hashed consumer credentials.
- CVE-2022-27494 (CVSS rating: 7.6) – The “Stories” tab of the Fleet Administration Console is susceptible to stored cross-web-site scripting attacks when new reports are made or edited.
- CVE-2022-1059 (CVSS rating: 7.6) – The “Load” tab of the Fleet Management Console is vulnerable to mirrored cross-internet site scripting attacks.

“These zero-working day vulnerabilities essential a quite very low ability established for exploitation, no special privileges, and no user interaction to be productively leveraged in an attack,” Cynerio’s Asher Brass claimed.
“If attackers have been capable to exploit JekyllBot:5, they could have wholly taken about method manage, gained obtain to actual-time camera feeds and device facts, and wreaked havoc and destruction at hospitals using the robots.”
Identified this article intriguing? Abide by THN on Facebook, Twitter and LinkedIn to examine much more distinctive information we post.
Some areas of this posting are sourced from:
thehackernews.com



 Haskers Gang Gives Away ZingoStealer Malware to Other Cybercriminals for Free
Haskers Gang Gives Away ZingoStealer Malware to Other Cybercriminals for Free