Linus Torvalds, the creator of Linux and Git, has his very own regulation in software package improvement, and it goes like this: “presented more than enough eyeballs, all bugs are shallow.” This phrase places the finger on the extremely theory of open up resource: the more, the merrier – if the code is quickly obtainable for any individual and absolutely everyone to resolve bugs, it truly is pretty risk-free. But is it? Or is the indicating “all bugs are shallow” only genuine for shallow bugs and not ones that lie deeper? It turns out that security flaws in open up source can be harder to obtain than we believed. Emil Wåreus, Head of R&D at Debricked, took it upon himself to search further into the community’s performance. As the information scientist he is, he, of study course, requested the knowledge: how superior is the open supply community at acquiring vulnerabilities in a well timed fashion?
The thrill of the (vulnerability) hunt
Locating open up supply vulnerabilities is generally done by the maintainers of the open up resource venture, people, auditors, or external security scientists. But regardless of these excellent code-archaeologists encouraging secure our earth, the group continue to struggles to uncover security flaws.
On normal, it requires in excess of 800 times to learn a security flaw in open up supply projects. For instance, the notorious Log4shell (CVE-2021-44228) vulnerability was undiscovered for a whopping 2649 days.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
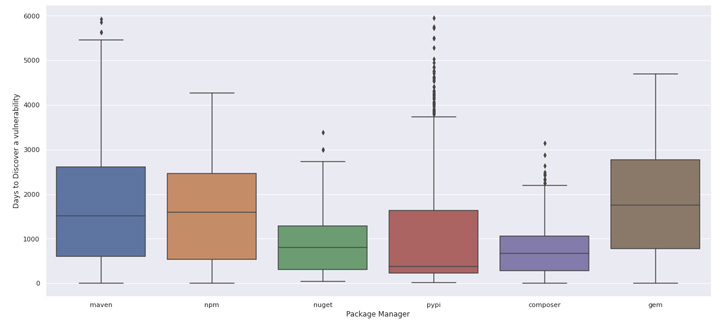
The analysis reveals that 74% of security flaws are really undiscovered for at least one particular year! Java and Ruby appear to have the most problems right here, as it will take the neighborhood much more than 1000 days to uncover and disclose vulnerabilities. Our [white] hats go off to the PHP/Composer neighborhood, which marginally outperforms the other individuals.
The needle in a techstack
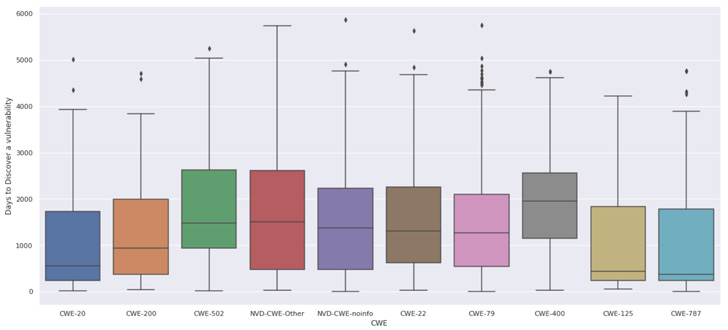
Other interesting elements are that some of the distinct weak point forms (CWE) seem to be to be harder to obtain and disclose, which really contradicts Linus’s regulation. The weak spot forms CWE-400 (Uncontrolled Resource Usage) and CWE-502 (Deserialization of Untrusted Facts) commonly usually are not localized to a one function or may perhaps look as meant logic in the application. In other phrases, it are unable to be thought of “a shallow bug.”
It also looks that the developer group is a bit improved at obtaining CWE-20 (Poor Input Validation), where by the flaw most of the time is just a few strains of code in a single perform.
Clear up vulnerabilities with effective remediation
Why does this subject? As individuals of open up supply, and that is about every single enterprise in the complete entire world, the challenge of vulnerabilities in open up supply is an essential one. The info tells us that we won’t be able to completely belief Linus’ Law – not mainly because open source is fewer safe than other computer software, but since not all bugs are shallow.
The good thing is, there are strong instruments to accomplish at-scale investigation of a whole lot of open up resource initiatives at as soon as. There have been [white knight hackers disclose 1000’s] of vulnerabilities at at the time utilizing these techniques. It would be naive to not presume that unwell-minded corporations and individuals do the identical. As an ecosystem that lays the basis for our program-centric globe, the group will have to increase its means to locate, disclose, and resolve security flaws in open up supply noticeably.
Past year, Google committed $10 billion to an open up resource fund to assistance protected open up source with a certain curator purpose to function along with the maintainers with unique security endeavours.
Moreover, Debricked aids businesses make these vulnerabilities actionable by scanning all your application, each individual branch, each individual push, and every single commit, for new (open supply) vulnerabilities. Debricked even continually scans all your previous commits for just about every new vulnerability, to make sure they provide up-to-day, correct, and actionable intelligence on the open source you eat. Debricked even helps developers resolve your security flaws with automatic pull requests that won’t trigger dependency hell quite neat!
The fact lies in the data
So, figuring out all this, what is the very best way to shield your undertaking or organization from open source vulnerabilities? As we have seen in the situation of Log4j and Spring4shell as well as the numbers, we can never really belief that the group will uncover and fix all hazards. There’s a great opportunity that there are tons and plenty of undiscovered and undisclosed vulnerabilities in your code today, and you will find not a great deal you can do about it.
According to Debricked, the very best way to mitigate this is by employing ongoing vulnerability scanning to your SDLC. By automatically scanning at each individual force of code, in mixture with the equipment discovering-driven vulnerability databases. This will make sure you are updated in authentic-time, you may know about new vulnerabilities right before everyone else does. As quickly as there is a take care of, you can generate a Repair Pull Ask for mechanically or clear up it manually with Debricked’s assist. At this time, Debricked gives remediation for JavaScript and Go, with a lot more language help is to appear shortly.
Discovered this short article appealing? Follow THN on Facebook, Twitter and LinkedIn to read through much more exclusive information we publish.
Some areas of this post are sourced from:
thehackernews.com


 Yanluowang ransomware leaks suggest pseudo Chinese persona, REvil links
Yanluowang ransomware leaks suggest pseudo Chinese persona, REvil links