Distant Accessibility Trojans (RATs) have taken the third top position in ANY. RUN’s Q1 2023 report on the most common malware varieties, earning it really probable that your business may well experience this threat.
While LimeRAT may well not be the most properly-recognised RAT household, its flexibility is what sets it apart. Capable of carrying out a broad spectrum of malicious actions, it excels not only in information exfiltration, but also in generating DDoS botnets and facilitating crypto mining. Its compact footprint enables it to elude endpoint detection techniques, generating it a stealthy adversary. Curiously, LimeRAT shares similarities with njRAT, which ANY.Run ranks as the 3rd most well-liked malware relatives in terms of uploads all through Q1 2023.
ANY.Operate scientists have lately executed an in-depth assessment of a LimeRAT sample and productively extracted its configuration. In this write-up, we are going to deliver a quick overview of that analysis.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Collected artifacts
SHA1
14836dd608efb4a0c552a4f370e5aafb340e2a5d
SHA256
6d08ed6acac230f41d9d6fe2a26245eeaf08c84bc7a66fddc764d82d6786d334
MD5
d36f15bef276fd447e91af6ee9e38b28
SSDEEP
3072:DDiv2GSyn88sH888wQ2wmVgMk/211h36vEcIyNTY4WZd/w1UwIwEoTqPMinXHx+i:XOayy
IPv4:
IOC
Description
20[.]199.13.167:8080
LimeRAT’s Command and Command server
Domains:
IOC
Description
https://pastebin[.]com/uncooked/sxNJt2ek
PasteBin used by LimeRAT to cover its original Command and Command server
MITRE ATT&CK®
Tactic
Method
Description
TA0005: Defense Evasion
T1027: Obfuscated Information or Information and facts
Malware is utilizing obfuscator to strip its system names, class names, etcetera.
TA0005: Protection Evasion
T1027: Obfuscated Information or Details
Malware employs Foundation64 algorithm to encode and decode info
TA0005: Protection Evasion
T1027: Obfuscated Data files or Information
Malware works by using AES algorithm to encrypt and decrypt information
ANY.Operate is jogging a confined-time provide, celebrating the 7th Cyberbirthdsay
ANY.Run is an interactive cloud malware sandbox that can extract malware configs instantly for numerous family members, saving researchers several hours of effort and hard work.
The services is celebrating its 7th anniversary and inviting all researchers to test out innovative assessment functions ordinarily reserved for pro plans, fully cost-free right until Might 5th. This involves configuring the execution natural environment with Windows 8, 10, or 11.
If you find that ANY.Run improves your malware analysis workflow, they are also providing a restricted promotion, out there right up until May well 5th: acquire 6 or 12 months of totally free use when you indicator up for a yearly or two-12 months membership, respectively.
Breaking down LimeRAT’s decryption algorithm
We are going to share a condensed variation of the article below. For a finish walkthrough and the extended examination, head over to ANY. RUN’s web site if you might be fascinated in discovering a lot more about the workflow they used.
Considering that the sample below overview was created in .NET, scientists used DnSpy to study the code. Instantly, it was apparent that obfuscation tactics were being remaining used:
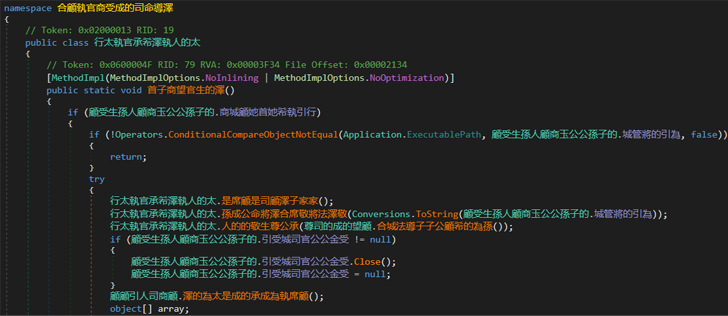 Sample overview in DnSpy note that use of obfuscation tactics
Sample overview in DnSpy note that use of obfuscation tactics
Nearer examination of the code revealed a course resembling the malware configuration. In this class, was a subject made up of a string that was both equally base64 encoded and encrypted.
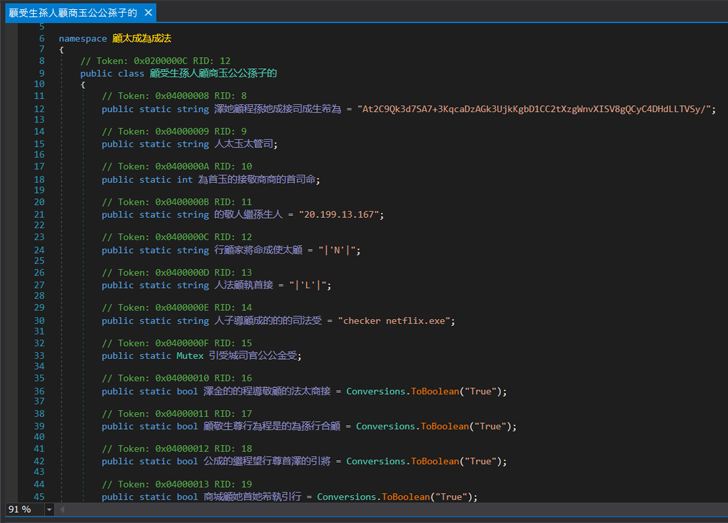 Probably, malware configuration course
Probably, malware configuration course
Continuing the code inspection, ANY.Operate researchers pinpointed a operate dependable for decrypting the string. By employing the “Read through by” filter in DnSpy, they tracked down procedures wherever the string was currently being study, which led to a complete of two methods. The to start with strategy proved unfruitful, but the second one particular looked attention-grabbing:
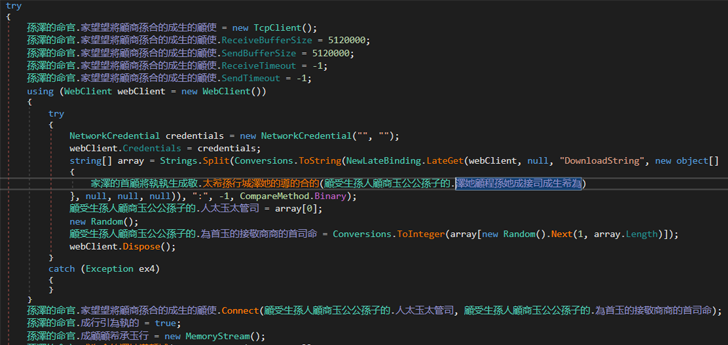 The second x-ref is a lot more attention-grabbing. It would seem that it utilizes our string in WebClient.DownloadString strategy
The second x-ref is a lot more attention-grabbing. It would seem that it utilizes our string in WebClient.DownloadString strategy
This strategy turned out to be accountable for decryption. By intently examining it, it was attainable to reconstruct the system by which LimeRAT decrypts its configuration:
Decrypting the string unveiled a link to a PasteBin note: https://pastebin[.]com/uncooked/sxNJt2ek. Inside this note, was LimeRAT’s Command and Management (C2) server:
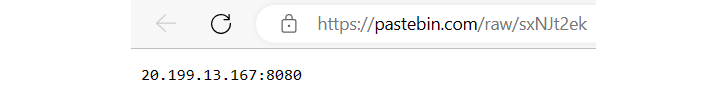 LimeRATs C2 discovered with decrypted info
LimeRATs C2 discovered with decrypted info
To wrap up
We hope you identified this quick overview of our LimeRAT configuration decryption process insightful. For a extra detailed examination, head more than to the total write-up on ANY.RUN’s blog site, to get extra context on the ways and check out the decryption course of action making use of CyberChef.
Also, keep in mind that ANY. RUN’s presently presenting confined-time discounts, showcasing discounts on subscriptions and an expanded element established for free of charge plans, like the ability to configure execution environments with Windows 8, 10, and 11 running techniques. This provide expires on Might 5th.
This is an best prospect to exam out ANY.Operate and establish if it streamlines your workflow, or to protected a membership at an unbeatable price tag and reap the rewards of major time personal savings by static and behavioral investigation.
To discover additional about this supply, visit ANY.Operate/plans.
Observed this post attention-grabbing? Adhere to us on Twitter and LinkedIn to read through much more exclusive information we put up.
Some areas of this posting are sourced from:
thehackernews.com


 RTM Locker’s First Linux Ransomware Strain Targeting NAS and ESXi Hosts
RTM Locker’s First Linux Ransomware Strain Targeting NAS and ESXi Hosts