A earlier acknowledged Windows distant access Trojan (RAT) with credential-stealing abilities has now expanded its scope to set its sights on consumers of Android devices to additional the attacker’s espionage motives.
“The developers of LodaRAT have included Android as a targeted platform,” Cisco Talos researchers stated in a Tuesday assessment. “A new iteration of LodaRAT for Windows has been identified with improved audio recording capabilities.”
Kasablanca, the group at the rear of the malware, is explained to have deployed the new RAT in an ongoing hybrid marketing campaign concentrating on Bangladeshi people, the scientists observed.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The purpose why Bangladesh-based businesses have been especially singled out for this marketing campaign stays unclear, as is the identification of the risk actor.

Initially documented in May perhaps 2017 by Proofpoint, Loda is an AutoIt malware ordinarily delivered by way of phishing lures that’s geared up to run a extensive assortment of instructions intended to file audio, video clip, and capture other sensitive information, with recent variants aimed at stealing passwords and cookies from browsers.
The most up-to-date versions — dubbed Loda4Android and Loda4Windows — are a whole lot alike in that they arrive with a total set of knowledge-collecting functions that constitute a stalker application. On the other hand, the Android malware is also distinct, as it specially avoids procedures generally made use of by banking Trojans, like abusing Accessibility APIs to record on-display actions.
Besides sharing the similar command-and-regulate (C2) infrastructure for both equally Android and Windows, the attacks, which originated in October 2020, have focused banking companies and carrier-quality voice-in excess of-IP software program distributors, with clues pointing to the malware writer being primarily based in Morocco.
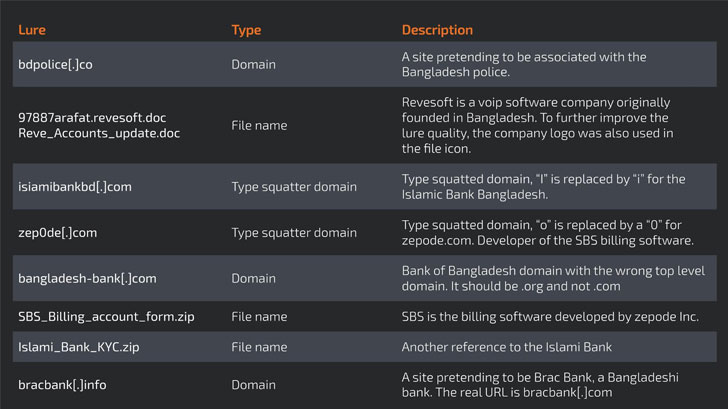
The attackers also created of a myriad variety of social engineering methods, ranging from typo squatted domains to destructive RTF documents embedded in e-mail, that, when opened, activated an an infection chain that leverages a memory corruption vulnerability in Microsoft Business office (CVE-2017-11882) to download the last payload.
Whilst the Android model of the malware can get shots and screenshots, examine SMS and simply call logs, mail SMS and accomplish calls to specific figures, and intercept SMS messages or phone calls, its most recent Windows counterpart comes with new instructions that empower distant entry to the focus on equipment by means of Remote Desktop Protocol (RDP) and “Audio” command that would make use of BASS audio library to capture audio from a linked microphone.
“The actuality that the threat team has developed into hybrid strategies focusing on Windows and Android demonstrates a team that is flourishing and evolving,” reported researchers with Cisco Talos.
“Alongside with these advancements, the menace actor has now centered on particular targets, indicating extra experienced operational abilities. As is the situation with previously versions of Loda, both of those versions of this new iteration pose a really serious danger, as they can guide to a important data breach or major money loss.”
Discovered this report fascinating? Abide by THN on Facebook, Twitter and LinkedIn to go through extra exceptional content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Microsft patches actively exploited Windows zero-day flaw
Microsft patches actively exploited Windows zero-day flaw