Numerous strategies that distributed trojanized and typosquatted deals on the NPM open source repository have been discovered as the do the job of a single threat actor dubbed LofyGang.
Checkmarx claimed it learned 199 rogue offers totaling hundreds of installations, with the team functioning for in excess of a calendar year with the intention of thieving credit card data as very well as user accounts linked with Discord Nitro, gaming, and streaming services.
“LofyGang operators are viewed endorsing their hacking instruments in hacking forums, although some of the resources are shipped with a concealed backdoor,” the software security business reported in a report shared with The Hacker News prior to its publication.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Many pieces of the attack puzzle have now been noted by JFrog, Sonatype, and Kaspersky (which called it LofyLife), but the latest examination pulls the various operations collectively beneath a single organizational umbrella that Checkmarx is referring to as LofyGang.
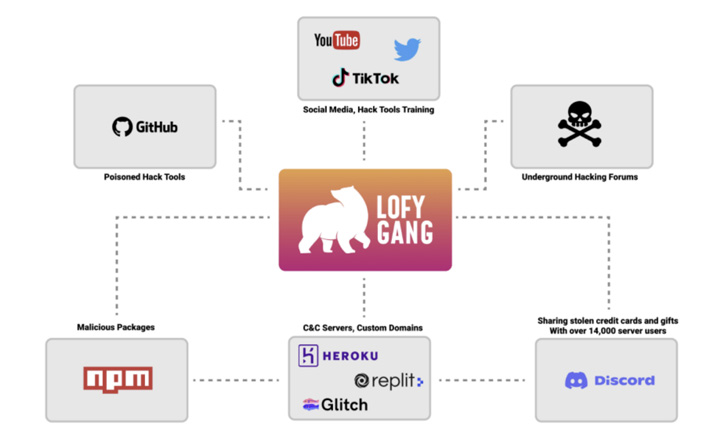
Thought to be an arranged crime group of Brazilian origin, the attackers have a monitor file of employing sock puppet accounts to market their tools and expert services on GitHub, YouTube, and leaking hundreds of Disney+ and Minecraft accounts on underground hacking boards.
It really is also known to employ a Discord server made nearly a 12 months ago on October 31, 2021, to offer specialized support and talk with their members. A person of its principal offerings is a services that sells phony Instagram followers.
“Discord, Repl.it, glitch, GitHub, and Heroku are just a couple of services LofyGang is employing as [command-and-control] servers for their operation,” the researchers famous.
What is more, the fraudulent packages traced back to the team have been discovered to embed password stealers and Discord-specific malware, some of which are made to steal credit score playing cards.
To conceal the scale of the supply chain attack, the deals are deliberately published through various user accounts so that other weaponized libraries keep on being unaffected on the repositories even if just one of them is spotted and removed by the maintainers.

Furthermore, the adversary has been identified utilizing a sneaky technique wherein the top-stage package deal is kept no cost of malware but have it rely on a different package that introduces the destructive capabilities.
Which is not all. Even the hacking tools shared by LofyGang on GitHub depend on destructive offers, correctly acting as a conduit to deploy persistent backdoors on the operator’s machines.
The conclusions are nevertheless one more indication that menace actors are progressively placing their sights on the open up source ecosystem as a stepping place to widen the scope and usefulness of the attacks.
“Communities are staying formed about making use of open up-resource computer software for malicious needs,” the scientists concluded. “We feel this is the start of a pattern that will raise in the coming months.”
Located this short article interesting? Stick to THN on Facebook, Twitter and LinkedIn to read much more exceptional material we post.
Some areas of this short article are sourced from:
thehackernews.com


 Papa John’s faces class-action lawsuit for alleged misuse of session tracking scripts
Papa John’s faces class-action lawsuit for alleged misuse of session tracking scripts