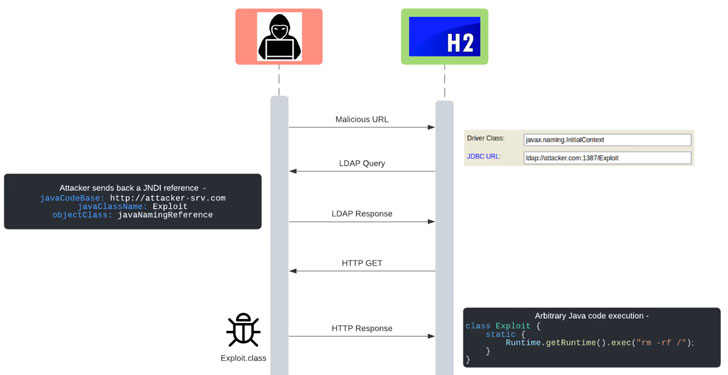
Scientists have disclosed a security flaw influencing H2 database consoles that could outcome in remote code execution in a manner that echoes the Log4j “Log4Shell” vulnerability that came to mild previous month.
The issue, tracked as CVE-2021-42392, is the ” first critical issue printed given that Log4Shell, on a component other than Log4j, that exploits the exact root trigger of the Log4Shell vulnerability, namely JNDI distant class loading,” JFrog scientists Andrey Polkovnychenko and Shachar Menashe reported.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

H2 is an open-source relational database administration program composed in Java that can be embedded inside of applications or run in a client-server manner. In accordance to the Maven Repository, the H2 databases engine is made use of by 6,807 artifacts.
JNDI, short for Java Naming and Listing Interface, refers to an API that supplies naming and listing operation for Java applications, which can use the API in conjunction with LDAP to identify a certain resource that it may well have to have.
In the circumstance of Log4Shell, this feature enables runtime lookups to servers, each inside and outside the house the network, which, in flip, can be weaponized to enable unauthenticated remote code execution and implant malware on the server by crafting a malicious JNDI lookup as input to any Java application that makes use of vulnerable variations of the Log4j library to log it.
“Very similar to the Log4Shell vulnerability uncovered in early December, attacker-controlled URLs that propagate into JNDI lookups can permit unauthenticated remote code execution, giving attackers sole manage in excess of the operation of one more particular person or organization’s programs,” Menashe, senior director of JFrog security research, defined.
The flaw impacts H2 databases versions 1.1.100 to 2..204 and has been addressed in version 2..206 shipped on January 5, 2022.
“The H2 databases is utilized by numerous 3rd-party frameworks, together with Spring Boot, Enjoy Framework and JHipster,” Menashe added. “Whilst this vulnerability is not as common as Log4Shell, it can still have a dramatic impact on builders and manufacturing devices if not resolved accordingly.”
Uncovered this posting interesting? Stick to THN on Fb, Twitter and LinkedIn to browse additional exceptional content material we post.
Some elements of this posting are sourced from:
thehackernews.com