A malware campaign focusing on South Korean entities that arrived to light earlier this 12 months has been attributed to a North Korean country-point out hacking team referred to as Andariel, the moment once more indicating that Lazarus attackers are pursuing the tendencies and their arsenal is in regular development.
“The way Windows instructions and their alternatives were applied in this marketing campaign is practically similar to earlier Andariel action,” Russian cybersecurity organization Kaspersky explained in a deep-dive released Tuesday. Victims of the attack are in the manufacturing, house network company, media, and construction sectors.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Selected as aspect of the Lazarus constellation, Andariel is identified for unleashing attacks on South Korean companies and firms using specially personalized approaches developed for utmost effectivity. In September 2019, the sub-group, alongside with Lazarus and Bluenoroff, was sanctioned by the U.S. Treasury Section for their malicious cyber activity on critical infrastructure.
Andariel is believed to have been lively considering the fact that at the very least Could 2016.
North Korea has been driving an significantly orchestrated effort and hard work aimed at infiltrating computers of fiscal establishments in South Korea and close to the entire world as perfectly as staging cryptocurrency heists to fund the money-strapped region in an endeavor to circumvent the stranglehold of economic sanctions imposed to stop the advancement of its nuclear weapons system.
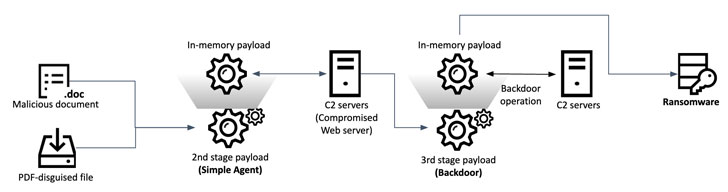
The results from Kaspersky construct upon a preceding report from Malwarebytes in April 2021, which documented a novel an infection chain that distributed phishing e-mail weaponized with a macro embedded in a Word file which is executed upon opening in order to deploy destructive code hid in the type of a bitmap (.BMP) image file to fall a distant obtain trojan (RAT) on focused methods.
In accordance to the newest assessment, the danger actor, moreover setting up a backdoor, is also said to have sent file-encrypting ransomware to one particular of its victims, implying a fiscal motive to the attacks. It truly is really worth noting that Andariel has a monitor history of making an attempt to steal financial institution card details by hacking into ATMs to withdraw money or market buyer data on the black market place.

“This ransomware sample is custom built and specifically designed by the risk actor guiding this attack,” Kaspersky Senior Security Researcher Seongsu Park reported. “This ransomware is managed by command line parameters and can either retrieve an encryption crucial from the C2 [server] or, alternatively, as an argument at start time.”
The ransomware is created to encrypt all information in the device with the exception of method-critical “.exe,” “.dll,” “.sys,” “.msiins,” and “.drv” extensions in return for shelling out a bitcoin ransom to get accessibility to a decrypt device and distinctive essential to unlock the scrambled files.
Kaspersky’s attribution to Andariel stems from overlaps in the XOR-based mostly decryption schedule that have been integrated into the group’s ways as early as 2018 and in the article-exploitation instructions executed on sufferer devices.
“The Andariel team has continued to concentrate on targets in South Korea, but their resources and tactics have progressed significantly,” Park claimed. “The Andariel group supposed to spread ransomware through this attack and, by undertaking so, they have underlined their location as a financially enthusiastic state-sponsored actor.”
Located this report appealing? Follow THN on Facebook, Twitter and LinkedIn to go through a lot more special material we post.
Some pieces of this write-up are sourced from:
thehackernews.com


 Football Fever Puts Password Security at Risk
Football Fever Puts Password Security at Risk