Scientists have specific what they connect with the “first effective try” at decrypting details contaminated with Hive ransomware without relying on the personal crucial utilized to lock obtain to the information.
“We have been capable to get well the learn crucial for producing the file encryption vital without the attacker’s personal key, by making use of a cryptographic vulnerability recognized by means of examination,” a team of lecturers from South Korea’s Kookmin College stated in a new paper analyzing its encryption course of action.
Hive, like other cybercriminals groups, operates a ransomware-as-a-services that uses various mechanisms to compromise business networks, exfiltrate knowledge, and encrypt info on the networks, and attempt to gather a ransom in exchange for obtain to the decryption program.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

It was initial noticed in June 2021, when it struck a company named Altus Team. Hive leverages a range of preliminary compromise solutions, like vulnerable RDP servers, compromised VPN qualifications, as perfectly as phishing email messages with destructive attachments.
The group also tactics the increasingly valuable plan of double extortion, whereby the actors go further than just encryption by also exfiltrating delicate target details and threatening to leak the info on their Tor web site, “HiveLeaks.”
As of October 16, 2021, the Hive RaaS method has victimized at least 355 firms, with the group securing the eighth spot between the top 10 ransomware strains by earnings in 2021, in accordance to blockchain analytics organization Chainalysis.
The malicious things to do connected with the team have also prompted the U.S. Federal Bureau of Investigation (FBI) to release a Flash report detailing the attacks’ modus operandi, noting how the ransomware terminates processes similar to backups, anti-virus, and file copying to aid encryption.
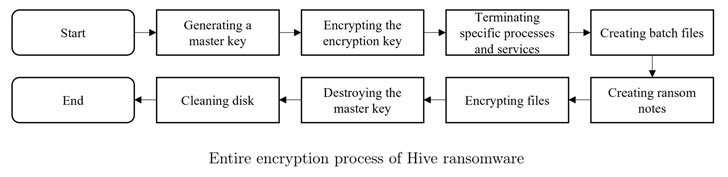
The cryptographic vulnerability determined by the scientists problems the system by which the learn keys are produced and saved, with the ransomware pressure only encrypting find portions of the file as opposed to the entire contents using two keystreams derived from the grasp essential.
“For every single file encryption procedure, two keystreams from the learn critical are desired,” the scientists stated. “Two keystreams are designed by choosing two random offsets from the learn important and extracting 0x100000 bytes (1MiB) and 0x400 bytes (1KiB) from the selected offset, respectively.”
The encryption keystream, which is developed from an XOR procedure of the two keystreams, is then XORed with the information in alternate blocks to generate the encrypted file. But this technique also tends to make it possible to guess the keystreams and restore the grasp essential, in convert enabling the decode of encrypted data files sans the attacker’s private crucial.
The scientists said that they have been in a position to weaponize the flaw to devise a process to reliably get better extra than 95% of the keys used during encryption.
“The grasp vital recovered 92% succeeded in decrypting about 72% of the data files, the learn important restored 96% succeeded in decrypting close to 82% of the files, and the master vital restored 98% succeeded in decrypting roughly 98% of the documents,” the scientists reported.
Identified this article exciting? Comply with THN on Fb, Twitter and LinkedIn to examine additional exclusive content we submit.
Some sections of this report are sourced from:
thehackernews.com



 Justice Department Appoints First Director of National Cryptocurrency Enforcement Team
Justice Department Appoints First Director of National Cryptocurrency Enforcement Team