Two distinctive Android banking Trojans, FluBot and Medusa, are relying on the identical delivery automobile as part of a simultaneous attack campaign, in accordance to new investigate published by ThreatFabric.
The ongoing facet-by-aspect infections, facilitated through the very same smishing (SMS phishing) infrastructure, associated the overlapping use of “application names, offer names, and comparable icons,” the Dutch mobile security organization mentioned.
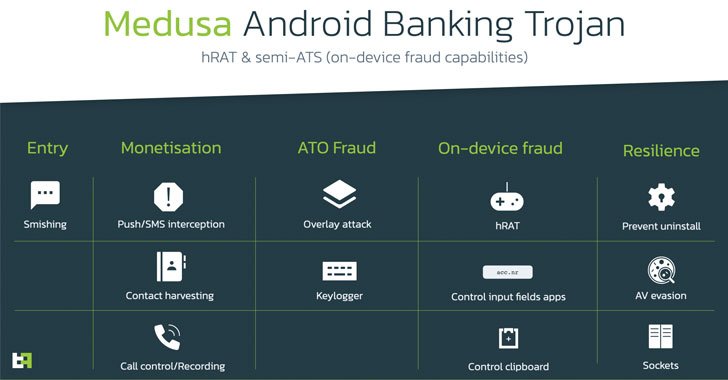
Medusa, initially uncovered concentrating on Turkish money businesses in July 2020, has undergone several iterations, main between which is the capacity to abuse accessibility permissions in Android to siphon resources from banking apps to an account managed by the attacker.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Medusa athletics other dangerous options like keylogging, accessibility event logging, and audio and video streaming — all these capabilities offer actors with practically comprehensive obtain to [a] victim’s system,” the scientists stated.

The malware-ridden apps utilized in conjunction with FluBot masquerade as DHL and Flash Participant apps to infect the gadgets. In addition, new attacks involving Medusa have expanded their target further than Turkey to involve Canada and the U.S., with the operators maintaining several botnets for just about every of its strategies.

FluBot (aka Cabassous), for its part, has gained a novel upgrade of its very own: the capacity to intercept and most likely manipulate notifications from specific purposes on a victim’s Android machine by leveraging the immediate reply action, together with auto-replying to messages from applications like WhatsApp to unfold phishing one-way links in a worm-like fashion.
“With this functionality, this malware is in a position to provide [command-and-control server] equipped responses to notifications of focused programs on the victim’s device,” the scientists claimed, incorporating the operation “can be utilized by actors to signal fraudulent transactions on victim’s behalf.”
This is not the very first time Android malware has been discovered to propagate by generating auto-replies to messages in WhatsApp. Final yr, ESET and Check Issue Investigate uncovered rogue apps posing as Huawei Cellular and Netflix that utilized the exact same modus operandi to conduct the wormable attacks.
“Much more and additional actors comply with Cabassous’ achievements in distribution tactics, appropriating masquerading techniques, and applying the same distribution assistance,” the scientists mentioned. “At the very same time, Cabassous keeps evolving, introducing new capabilities and building yet another move in the direction of being able to execute on-unit fraud.”
Discovered this report appealing? Follow THN on Facebook, Twitter and LinkedIn to read much more exceptional content we publish.
Some areas of this write-up are sourced from:
thehackernews.com


 How Attack Surface Management Preempts Cyberattacks
How Attack Surface Management Preempts Cyberattacks