Meta reported it took measures to take down much more than 1,000 destructive URLs from being shared across its companies that were discovered to leverage OpenAI’s ChatGPT as a entice to propagate about 10 malware people considering that March 2023.
The growth comes towards the backdrop of pretend ChatGPT web browser extensions remaining ever more utilized to steal users’ Facebook account credentials with an aim to run unauthorized adverts from hijacked enterprise accounts.
“Threat actors make malicious browser extensions obtainable in formal web merchants that claim to provide ChatGPT-centered equipment,” Meta reported. “They would then promote these destructive extensions on social media and as a result of sponsored search results to trick people into downloading malware.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The social media big claimed it has blocked several iterations of a multi-pronged malware marketing campaign dubbed Ducktail in excess of the decades, introducing it issued a cease and desist letter to people powering the operation who are found in Vietnam.
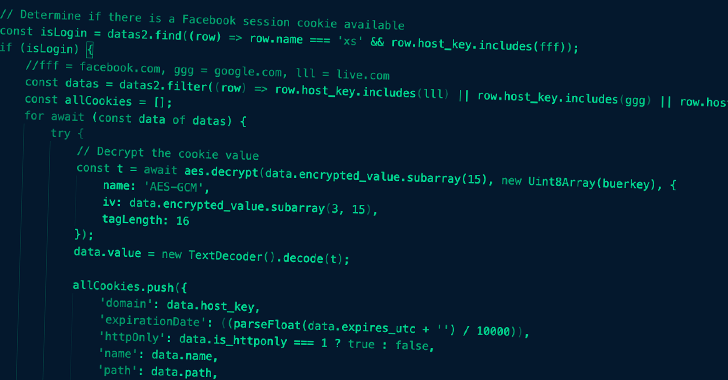
Trend Micro, in a collection of tweets final 7 days, detailed an info stealer which is disguised as a Windows desktop client for ChatGPT to extract passwords, session cookies, and record from Chromium-driven browsers. The company mentioned the malware shares similarities with Ducktail.
Other than ChatGPT, threat actors have also been noticed shifting to other “hot-button issues and well-known topics” like Google Bard, TikTok advertising resources, pirated software and flicks, and Windows utilities to dupe individuals into clicking on bogus backlinks.
“These changes are probable an try by menace actors to be certain that any one company has only minimal visibility into the whole operation,” Guy Rosen, main information security officer at Meta, explained.
The attack chains are principally engineered to concentrate on the own accounts of end users who take care of or are related to small business internet pages and marketing accounts on Fb.
Besides applying social media for propagating the ChatGPT-themed destructive URLs, the malware is hosted on a selection of authentic providers this sort of as Get Me a Coffee, Discord, Dropbox, Google Generate, iCloud, MediaFire, Mega, Microsoft OneDrive, and Trello.
Ducktail isn’t the only stealer malware detected in the wild, for Meta disclosed that it uncovered another novel strain dubbed NodeStealer that is able of plundering cookies and passwords from web browsers to finally compromise Facebook, Gmail, and Outlook accounts.
The malware is assessed to be of Vietnamese origin, with Meta noting that it “took motion to disrupt it and support persons who may perhaps have been qualified to recuperate their accounts” inside of two months of it staying deployed in late January 2023.
Impending WEBINARLearn to Cease Ransomware with Real-Time Defense
Be part of our webinar and study how to cease ransomware attacks in their tracks with true-time MFA and services account security.
Conserve My Seat!
Samples analyzed by the organization clearly show that NodeStealer binary is dispersed by means of Windows executables disguised as PDF and XLSX data files with filenames relating to promoting and regular budgets. The documents, when opened, produce JavaScript code that’s developed to exfiltrate delicate facts from Chromium-dependent browsers.
NodeStealer gets its title from the use of the Node.js cross-platform JavaScript runtime natural environment, which is bundled together with the main payload, to established up persistence and execute the malware. No new artifacts have been identified as of February 27, 2023.
“Just after retrieving the Fb credentials from the target’s browser knowledge, the malware makes use of it to make various unauthorized requests to Facebook URLs to enumerate account information and facts connected to marketing,” Meta claimed. “The stolen information and facts then enables the menace actor to evaluate and then use users’ advertising and marketing accounts to operate unauthorized adverts.”
In an attempt to slip under the radar of the company’s anti-abuse techniques, the rogue requests are created from the focused user’s device to the Facebook APIs, lending a veneer of legitimacy to the exercise.
To counter this kind of threats, Meta claimed it’s launching a new aid instrument that guides consumers to establish and take out malware, allow firms to validate linked Organization Manager accounts, and have to have supplemental authentication when accessing a credit score line or altering business enterprise directors.
Discovered this report attention-grabbing? Abide by us on Twitter and LinkedIn to browse more exclusive information we write-up.
Some parts of this report are sourced from:
thehackernews.com

 US Authorities Dismantle Dark Web “Card Checking” Platform
US Authorities Dismantle Dark Web “Card Checking” Platform