Microsoft on Thursday attributed the current spate of ransomware incidents targeting transportation and logistics sectors in Ukraine and Poland to a threat cluster that shares overlaps with the Russian state-sponsored Sandworm team.
The attacks, which have been disclosed by the tech huge previous month, included a pressure of formerly undocumented malware known as Status and is reported to have taken spot within an hour of every single other throughout all victims.
The Microsoft Threat Intelligence Center (MSTIC) is now tracking the threat actor underneath its ingredient-themed moniker Iridium (née DEV-0960), citing overlaps with Sandworm (aka Iron Viking, TeleBots, and Voodoo Bear).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“This attribution evaluation is based mostly on forensic artifacts, as well as overlaps in victimology, tradecraft, abilities, and infrastructure, with recognised Iridium exercise,” MSTIC said in an update.
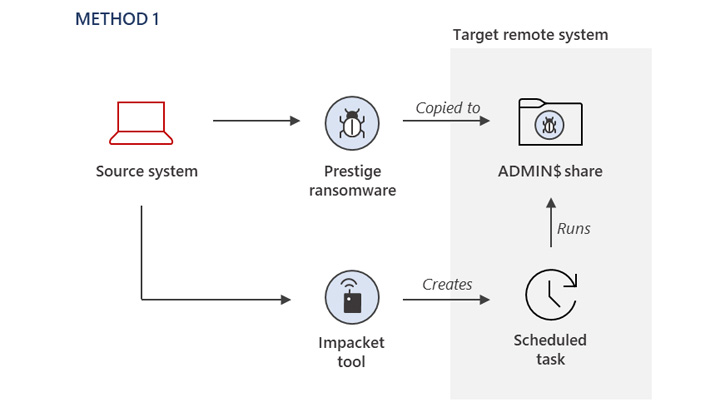
The organization also even more assessed the group to have orchestrated compromise action targeting quite a few of the Prestige victims as considerably back as March 2022, right before culminating in the deployment of the ransomware on October 11.
The process of first compromise nonetheless continues to be unknown, while it is really suspected that it concerned gaining obtain to highly privileged qualifications required to activate the killchain.
“The Status campaign might spotlight a calculated shift in Iridium’s harmful attack calculus, signaling enhanced risk to organizations directly giving or transporting humanitarian or army support to Ukraine,” the enterprise explained.
The conclusions appear in excess of a month immediately after Recorded Upcoming joined another action team (UAC-0113) with ties to the Sandworm actor as obtaining singled out Ukrainian people by masquerading as telecom companies in the region to supply backdoors onto compromised equipment.
Microsoft, in its Electronic Protection Report revealed very last 7 days, further more identified as out Iridium for its pattern of focusing on critical infrastructure and operational technology entities.
“Iridium deployed the Industroyer2 malware in a failed effort to go away tens of millions of persons in Ukraine without the need of electricity,” Redmond mentioned, introducing the threat actor employed “phishing strategies to gain preliminary entry to desired accounts and networks in companies in and outside Ukraine.”
The growth also comes amid sustained ransomware attacks aimed at industrial businesses around the world through the third quarter of 2022, with Dragos reporting 128 these incidents all through the time period in contrast to 125 in the earlier quarter.

“The LockBit ransomware household account for 33% and 35% respectively of the full ransomware incidents that concentrate on industrial businesses and infrastructures in the very last two quarters, as the teams extra new abilities in their new LockBit 3. strain,” the industrial security company explained.
Other distinguished strains observed in Q3 2022 include things like Cl0p, MedusaLocker, Sparta, BianLian, Donuts, Onyx, REvil, and Yanluowang.
Discovered this post exciting? Comply with THN on Facebook, Twitter and LinkedIn to study additional exceptional articles we post.
Some parts of this article are sourced from:
thehackernews.com

 The long road ahead to ransomware preparedness
The long road ahead to ransomware preparedness