Microsoft on Monday disclosed details of a lately patched security vulnerability in Apple’s macOS running method that could be weaponized by a danger actor to expose users’ own details.
Tracked as CVE-2021-30970, the flaw worries a logic issue in the Transparency, Consent and Management (TCC) security framework, which enables customers to configure the privacy options of their apps and deliver access to shielded documents and app data. The Security & Privacy pane in the macOS Procedure Tastes application serves as the entrance stop of TCC.
Microsoft 365 Defender Research Staff, which claimed the flaw to Apple on July 15, 2021, dubbed the flaw “powerdir.” Apple tackled the issue as aspect of macOS 11.6 and 12.1 updates launched in December 2021 with improved point out management.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

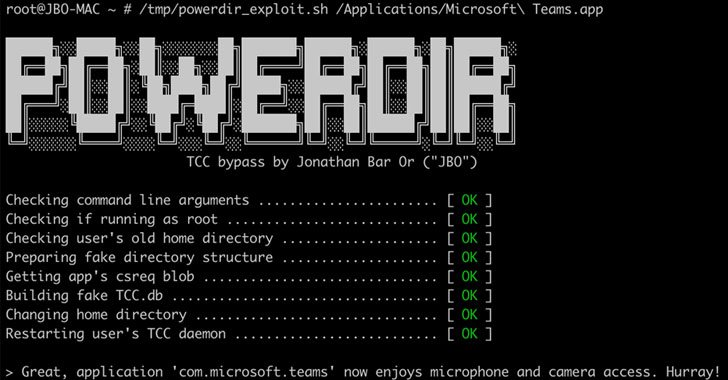
When Apple does implement a coverage that boundaries entry to TCC to only apps with full disk obtain, it truly is doable to orchestrate an attack wherein a malicious application could operate all around its privacy preferences to retrieve delicate info from the machine, possibly letting an adversary to access microphone to file personal conversations or seize screenshots of sensitive information and facts displayed on the user’s screen.
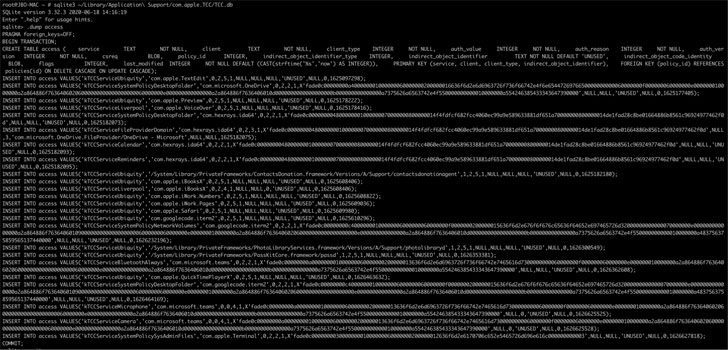
“We found out that it is probable to programmatically modify a goal user’s property listing and plant a faux TCC databases, which merchants the consent record of app requests,” Jonathan Bar Or of Microsoft 365 Defender Investigate Crew stated. “If exploited on unpatched methods, this vulnerability could allow for a destructive actor to probably orchestrate an attack dependent on the user’s safeguarded personalized details.”
In other text, if a lousy actor gains entire disk obtain to the TCC databases, the intruder could edit it to grant arbitrary permissions to any application of their decision, together with their own, effectively permitting the application operate with configurations beforehand not consented to.
CVE-2021-30970 is also the 3rd TCC-associated bypass vulnerability to be discovered just after CVE-2020-9934 and CVE-2020-27937, equally of which have since been remediated by Apple. Then in Might 2021, the business also patched a then zero-working day flaw in the very same ingredient (CVE-2021-30713) that could enable an attacker to gain whole disk obtain, display recording, or other permissions without having users’ specific consent.
“This demonstrates that even as macOS or other working methods and purposes become extra hardened with each individual launch, application vendors like Apple, security scientists, and the more substantial security local community, need to have to continually work with each other to determine and deal with vulnerabilities before attackers can just take gain of them,” Bar Or explained.
Identified this short article intriguing? Comply with THN on Facebook, Twitter and LinkedIn to browse additional exceptional material we submit.
Some elements of this article are sourced from:
thehackernews.com


 Europol Ordered to Delete Data of Individuals With No Proven Links to Crimes
Europol Ordered to Delete Data of Individuals With No Proven Links to Crimes