Microsoft on Tuesday disclosed a established of two privilege escalation vulnerabilities in the Linux working method that could probably enable danger actors to have out an array of nefarious things to do.
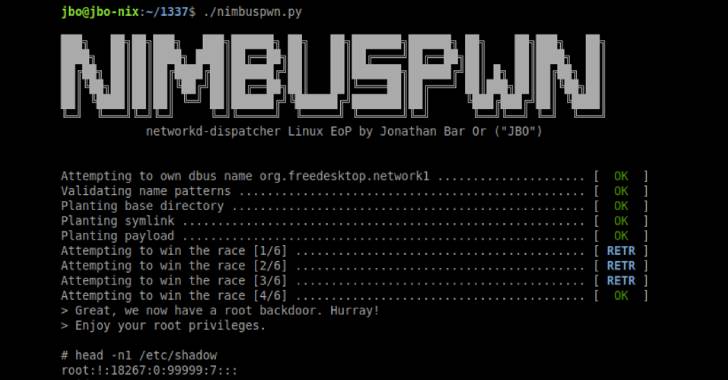
Collectively called “Nimbuspwn,” the flaws “can be chained alongside one another to gain root privileges on Linux programs, making it possible for attackers to deploy payloads, like a root backdoor, and accomplish other destructive steps via arbitrary root code execution,” Jonathan Bar Or of the Microsoft 365 Defender Investigation Team mentioned in a report.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
On top rated of that, the flaws — tracked as CVE-2022-29799 and CVE-2022-29800 — could also be weaponized as a vector for root entry to deploy additional sophisticated threats this kind of as ransomware.
The vulnerabilities are rooted in a systemd component termed networkd-dispatcher, a daemon software for the network manager process company which is developed to dispatch network standing adjustments.
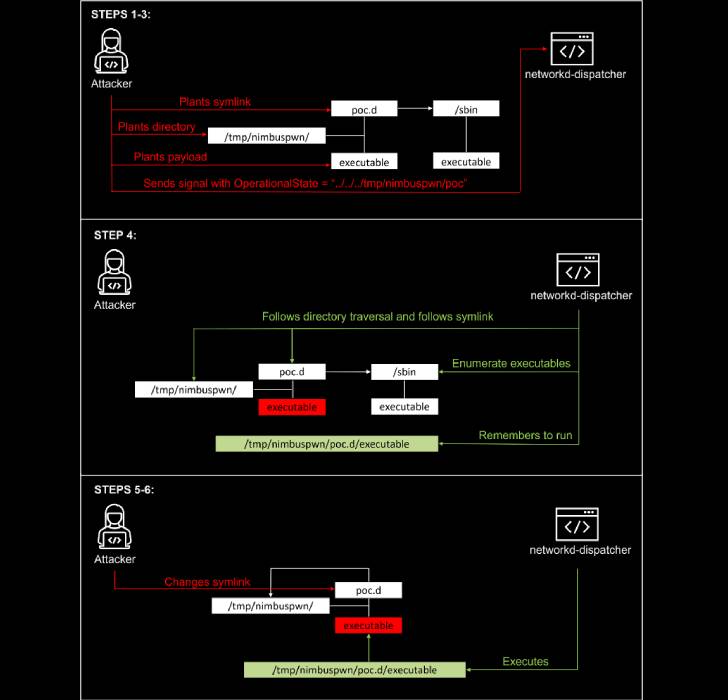
Particularly, they relate to a blend of directory traversal (CVE-2022-29799), symbolic connection (aka symlink) race, and time-of-look at to time-of-use (CVE-2022-29800) flaws, leading to a state of affairs where by an adversary in manage of a rogue D-Bus support can plant and execute malicious backdoors on the compromised endpoints.

Consumers of networkd-dispatcher are hugely advisable to update their situations to the most current variation to mitigate probable arising out of exploiting the flaws.
“The developing amount of vulnerabilities on Linux environments emphasize the want for solid checking of the platform’s working program and its factors,” Bar Or claimed.
“This constant bombardment of attacks spanning a huge range of platforms, devices, and other domains emphasizes the need for a extensive and proactive vulnerability administration tactic that can additional discover and mitigate even earlier unfamiliar exploits and issues.”
Discovered this posting attention-grabbing? Follow THN on Facebook, Twitter and LinkedIn to read through extra unique content material we publish.
Some sections of this short article are sourced from:
thehackernews.com


 Data Breach Disrupts UK Army Recruitment
Data Breach Disrupts UK Army Recruitment