At the very least 6 various Russia-aligned actors launched no considerably less than 237 cyberattacks against Ukraine from February 23 to April 8, which includes 38 discrete damaging attacks that irrevocably destroyed data files in hundreds of devices throughout dozens of businesses in the nation.
“Collectively, the cyber and kinetic actions work to disrupt or degrade Ukrainian govt and military services capabilities and undermine the public’s rely on in individuals very same institutions,” the company’s Electronic Security Unit (DSU) said in a special report.
The significant malware households that have been leveraged for harmful action as part of Russia’s relentless digital assaults incorporate: WhisperGate, HermeticWiper (FoxBlade aka KillDisk), HermeticRansom (SonicVote), IssacWiper (Lasainraw), CaddyWiper, DesertBlade, DoubleZero (FiberLake), and Industroyer2.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
WhisperGate, HermeticWiper, IssacWiper, and CaddyWiper are all data wipers designed to overwrite facts and render devices unbootable, even though DoubleZero is a .NET malware capable of knowledge deletion. DesertBlade, also a knowledge wiper, is claimed to have been launched against an unnamed broadcasting business in Ukraine on March 1.
SonicVote, on the other hand, is a file encryptor detected in conjunction with HermeticWiper to disguise the intrusions as a ransomware attack, although Industroyer2 particularly targets operational technology to sabotage critical industrial manufacturing and procedures.
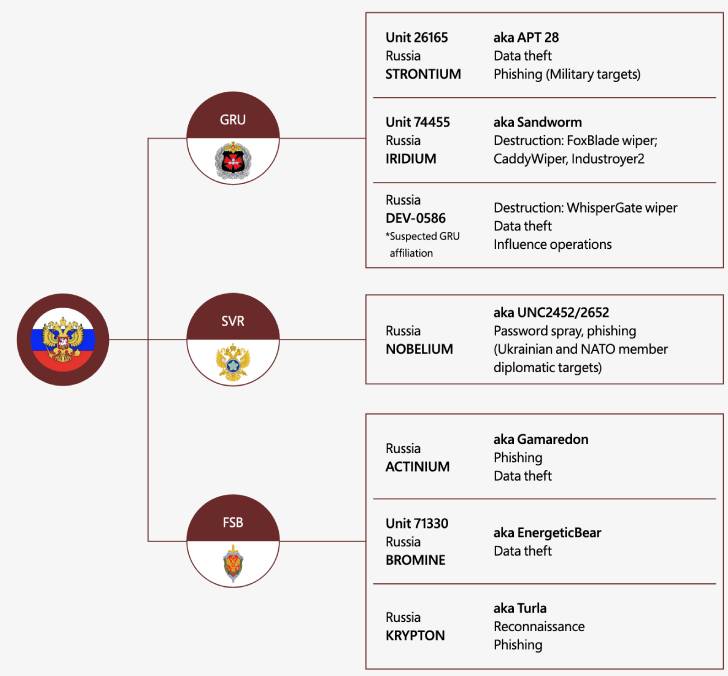
Microsoft attributed HermeticWiper, CaddyWiper, and Industroyer2 with average self-assurance to a Russian state-sponsored actor named Sandworm (aka Iridium). The WhisperGate attacks have been tied to a previously not known cluster dubbed DEV-0586, which is believed to be affiliated to Russia’s GRU armed forces intelligence.
32% of the total 38 destructive attacks are believed to have singled out Ukrainian federal government businesses at the national, regional and metropolis stages, with above 40% of the attacks aimed at organizations in critical infrastructure sectors in the nations.

In addition, Microsoft reported it noticed Nobelium, the menace actor blamed for the 2020 SolarWinds provide chain attack, attempting to breach IT companies serving governing administration customers in NATO member states, using the accessibility to siphon details from Western international policy companies.

Other malicious attacks involve phishing strategies focusing on armed service entities (Fancy Bear aka Strontium) and govt officers (Primitive Bear aka Actinium) as perfectly as knowledge theft (Energetic Bear aka Bromine) and reconnaissance (Venomous Bear aka Krypton) operations.
“Russia’s use of cyberattacks appears to be strongly correlated and from time to time specifically timed with its kinetic military functions targeting companies and institutions essential for civilians,” Tom Burt, corporate vice president of shopper security and belief, stated.
“Given Russian danger actors have been mirroring and augmenting military services actions, we feel cyberattacks will continue on to escalate as the conflict rages. It is really very likely the attacks we’ve noticed are only a portion of activity targeting Ukraine.”
Observed this article intriguing? Follow THN on Fb, Twitter and LinkedIn to read additional exceptional content we post.
Some elements of this write-up are sourced from:
thehackernews.com



 EU rules against Meta in data privacy row
EU rules against Meta in data privacy row