Microsoft on Thursday warned of a “massive email marketing campaign” that is pushing a Java-based STRRAT malware to steal private knowledge from infected systems while disguising alone as a ransomware infection.
“This RAT is notorious for its ransomware-like behavior of appending the file title extension .crimson to documents with out actually encrypting them,” the Microsoft Security Intelligence team said in a sequence of tweets.
The new wave of attacks, which the organization spotted very last 7 days, commences with spam email messages sent from compromised email accounts with “Outgoing Payments” in the issue line, luring the recipients into opening malicious PDF paperwork that claim to be remittances, but in actuality, join to a rogue domain to obtain the STRRAT malware.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Other than creating connections to a command-and-handle server for the duration of execution, the malware comes with a array of options that permit it to accumulate browser passwords, log keystrokes, and operate distant instructions and PowerShell scripts.
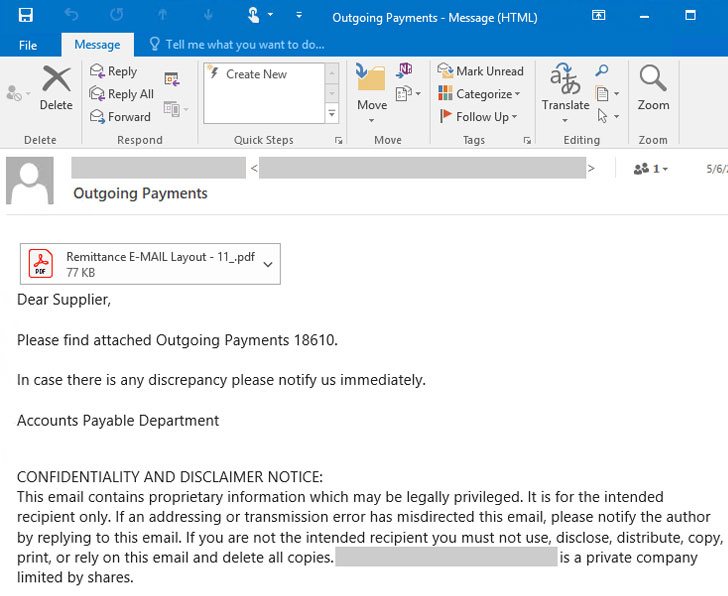
STRRAT 1st emerged in the risk landscape in June 2020, with German cybersecurity organization G Facts observing the Windows malware (version 1.2) in phishing email messages made up of destructive Jar (or Java Archive) attachments.
“The RAT has a concentrate on stealing credentials of browsers and email clientele, and passwords by using keylogging,” G Knowledge malware analyst Karsten Hahn specific. “It supports the adhering to browsers and email customers: Firefox, Internet Explorer, Chrome, Foxmail, Outlook, Thunderbird.”
Its ransomware abilities are at ideal rudimentary in that the “encryption” stage only renames data files by suffixing the “.crimson” extension. “If the extension is eradicated, the documents can be opened as normal,” Kahn additional.
Microsoft also notes that model 1.5 is a lot more obfuscated and modular than preceding variations, suggesting that the attackers powering the procedure are actively performing to improvise their toolset. But the simple fact that the bogus encryption habits continues to be unchanged alerts that the team may be aiming to make speedy funds off unsuspecting end users by indicates of extortion.
The indicators of compromise (IoCs) linked with the campaign can be accessed by using GitHub listed here.
Uncovered this short article fascinating? Comply with THN on Fb, Twitter and LinkedIn to go through a lot more exclusive information we put up.
Some sections of this write-up are sourced from:
thehackernews.com


 Misconfigurations may have exposed data on 100 million Android users
Misconfigurations may have exposed data on 100 million Android users