A variant of the Mirai botnet acknowledged as MooBot is co-opting vulnerable D-Link units into an military of denial-of-support bots by using gain of a number of exploits.
“If the gadgets are compromised, they will be fully managed by attackers, who could use people devices to carry out additional attacks these kinds of as distributed denial-of-company (DDoS) attacks,” Palo Alto Networks Device 42 reported in a Tuesday report.
MooBot, initial disclosed by Qihoo 360’s Netlab group in September 2019, has beforehand qualified LILIN digital video clip recorders and Hikvision video surveillance products to grow its network.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

In the hottest wave of attacks found out by Device 42 in early August 2022, as lots of as four different flaws in D-Url equipment, equally previous and new, have paved the way for the deployment of MooBot samples. These include things like –
- CVE-2015-2051 (CVSS rating: 10.) – D-Url HNAP SOAPAction Header Command Execution Vulnerability
- CVE-2018-6530 (CVSS rating: 9.8) – D-Hyperlink Soap Interface Distant Code Execution Vulnerability
- CVE-2022-26258 (CVSS score: 9.8) – D-Backlink Remote Command Execution Vulnerability, and
- CVE-2022-28958 (CVSS rating: 9.8) – D-Url Remote Command Execution Vulnerability
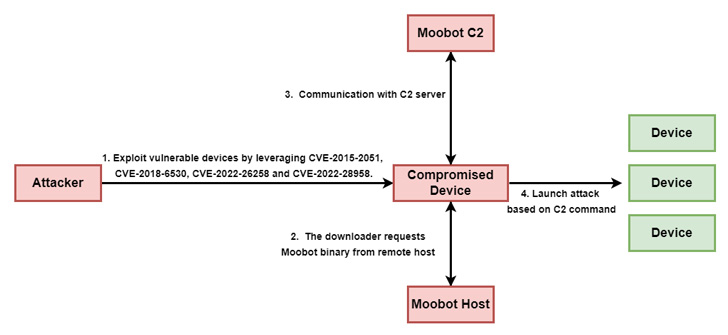
Thriving exploitation of the aforementioned flaws could guide to remote code execution and the retrieval of a MooBot payload from a remote host, which then parses recommendations from a command-and-management (C2) server to start a DDoS attack on a precise IP address and port variety.

Prospects of D-Url appliances are really encouraged to apply patches and updates launched by the organization to mitigate probable threats.
“The vulnerabilities […] have low attack complexity but critical security affect that can direct to remote code execution,” the scientists claimed. “Once the attacker gains handle in this fashion, they could acquire benefit by which includes the recently compromised equipment into their botnet to conduct additional attacks these types of as DDoS.”
Observed this article attention-grabbing? Follow THN on Facebook, Twitter and LinkedIn to read a lot more distinctive material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Critical RCE Vulnerability Affects Zyxel NAS Devices — Firmware Patch Released
Critical RCE Vulnerability Affects Zyxel NAS Devices — Firmware Patch Released