A banking trojan dubbed Mispadu has been linked to numerous spam strategies concentrating on nations around the world like Bolivia, Chile, Mexico, Peru, and Portugal with the target of thieving credentials and offering other payloads.
The exercise, which commenced in August 2022, is currently ongoing, Ocelot Group from Latin American cybersecurity organization Metabase Q mentioned in a report shared with The Hacker News.
Mispadu (aka URSA) was very first documented by ESET in November 2019, describing its capability to perpetrate monetary and credential theft and act as a backdoor by getting screenshots and capturing keystrokes.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“A single of their primary tactics is to compromise reputable sites, looking for vulnerable versions of WordPress, to transform them into their command-and-management server to distribute malware from there, filtering out nations they do not wish to infect, dropping different type of malware centered on the state remaining infected,” scientists Fernando García and Dan Regalado mentioned.
It can be also explained to share similarities with other banking trojans targeting the region, like Grandoreiro, Javali, and Lampion. Attack chains involving the Delphi malware leverage email messages urging recipients to open up faux overdue invoices, thus triggering a multi-phase infection system.
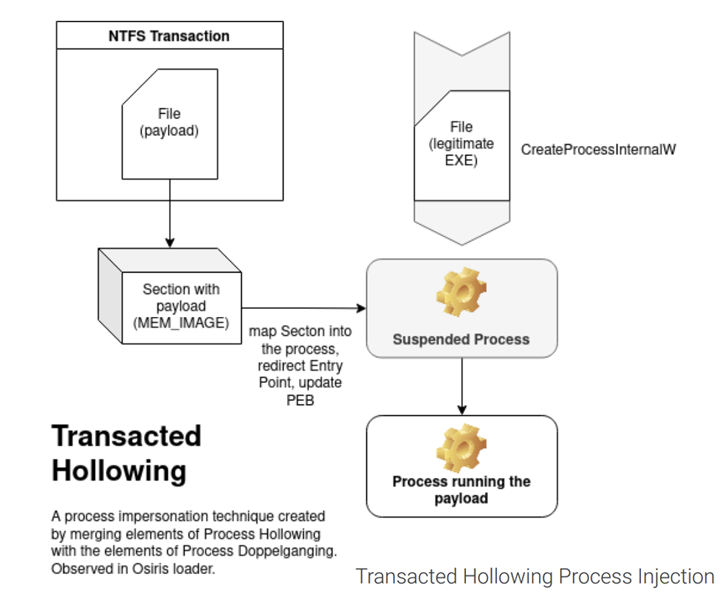
Need to a target open the HTML attachment sent via the spam email, it verifies that the file was opened from a desktop gadget and then redirects to a remote server to fetch the first-phase malware.
The RAR or ZIP archive, when released, is made to make use of rogue electronic certificates – just one which is the Mispadu malware and the other, an AutoIT installer – to decode and execute the trojan by abusing the reputable certutil command-line utility.
Mispadu is equipped to acquire the checklist of antivirus alternatives put in on the compromised host, siphon credentials from Google Chrome and Microsoft Outlook, and aid the retrieval of supplemental malware.
WEBINARDiscover the Concealed Dangers of Third-Party SaaS Applications
Are you knowledgeable of the hazards connected with third-party app accessibility to your firm’s SaaS applications? Be a part of our webinar to study about the kinds of permissions being granted and how to decrease risk.
RESERVE YOUR SEAT
This features an obfuscated Visible Basic Script dropper that serves to down load a further payload from a really hard-coded domain, a .NET-based mostly remote entry resource that can operate commands issued by an actor-controlled server, and a loader penned in Rust that, in change, executes a PowerShell loader to operate documents right from memory.
What is much more, the malware makes use of destructive overlay screens to receive qualifications linked with on line banking portals and other sensitive facts.
Metabase Q observed that the certutil approach has allowed Mispadu to bypass detection by a large variety of security software package and harvest about 90,000 financial institution account credentials from more than 17,500 one of a kind internet sites.
Uncovered this report fascinating? Stick to us on Twitter and LinkedIn to browse additional special content material we submit.
Some parts of this article are sourced from:
thehackernews.com

 Latitude hack now under state investigation as customers struggle to protect their accounts
Latitude hack now under state investigation as customers struggle to protect their accounts