The Android malware tracked as BRATA has been up to date with new functions that grants it the capability to monitor unit places and even accomplish a manufacturing facility reset in an obvious bid to include up fraudulent wire transfers.
The newest variants, detected late past yr, are explained to be distributed as a result of a downloader to avoid getting detected by security application, Italian cybersecurity company Cleafy stated in a complex publish-up. Targets involve banking companies and money institutions in the U.K., Poland, Italy, and Latin The usa.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
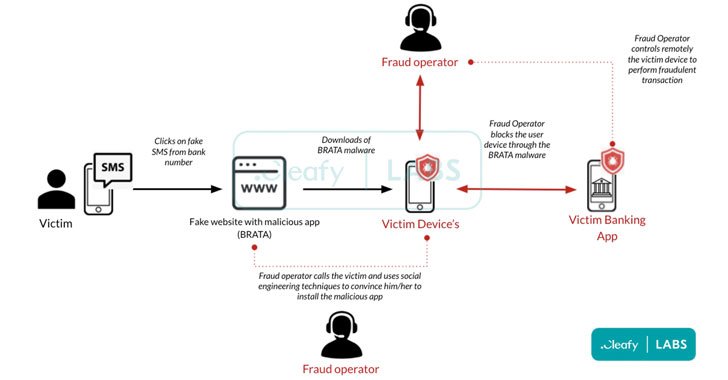
“What tends to make Android RAT so interesting for attackers is its ability to function instantly on the victim equipment rather of making use of a new product,” Cleafy scientists mentioned in December 2021. “By doing so, Danger Actors (TAs) can drastically decrease the likelihood of being flagged “as suspicious”, given that the device’s fingerprinting is previously known to the financial institution.”
Initially seen in the wild at the close of 2018 and small for “Brazilian Distant Access Instrument Android,” BRATA to begin with targeted consumers in Brazil and then quickly progressed into a characteristic-packed banking trojan. Considering that then, the malware has received many updates and adjustments, though also posing as security scanner applications to elude detection.
The latest “tailored” samples of BRATA set purpose at various nations around the world and constitute an initial dropper — a security application dubbed “iSecurity” — that stays undetected by virtually all malware scanning engines and is applied to down load and execute the actual destructive software.
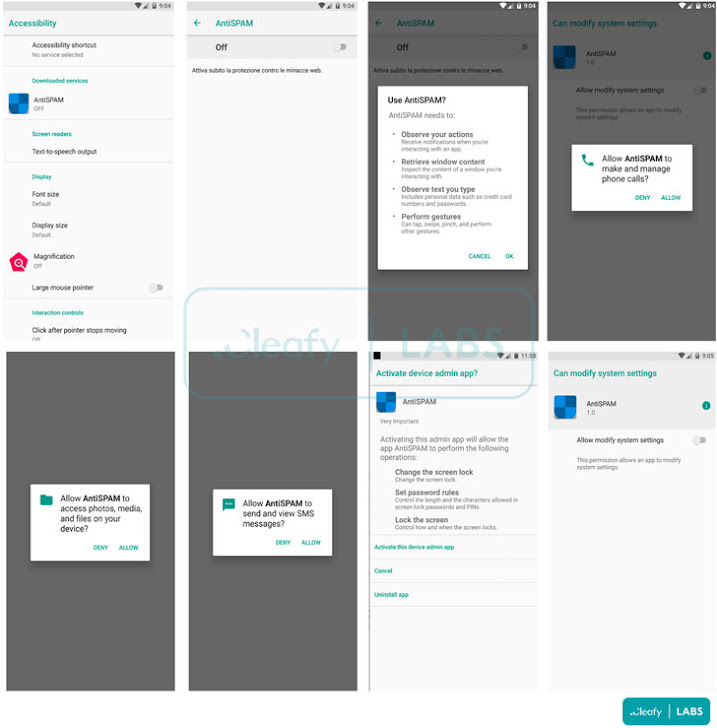
“Right after the target installs the downloader app, it calls for accepting just just one authorization to down load and put in the destructive software from an untrusted supply,” the researchers said. “When the sufferer clicks on the install button, the downloader application sends a GET ask for to the C2 server to down load the malicious .APK.”
BRATA, like other banking trojans noticed in the wild, is known to abuse its Accessibility Company permissions acquired during the set up phase to watch the user’s activity on the compromised machine stealthily.
In addition, the new versions have integrated a eliminate change system that lets the operators to restore the Android phone to its manufacturing unit configurations upon efficiently completing a fraudulent wire transfer or in situations wherever the software is mounted in a virtual setting.
“BRATA is hoping to access out to new targets and to develop new features,” the scientists mentioned, including danger actors are “leveraging this banking trojan for carrying out frauds, generally through unauthorized wire transfer (e.g., SEPA) or through Immediate Payments, making use of a huge network of money mules accounts in a number of European nations around the world.”
Found this posting exciting? Follow THN on Fb, Twitter and LinkedIn to read much more unique information we submit.
Some components of this article are sourced from:
thehackernews.com


 Hackers Using New Malware Packer DTPacker to Avoid Analysis, Detection
Hackers Using New Malware Packer DTPacker to Avoid Analysis, Detection