A Middle Japanese superior persistent risk (APT) team has resurfaced right after a two-thirty day period hiatus to focus on govt institutions in the Center East and world-wide government entities associated with geopolitics in the region in a rash of new strategies observed previously this month.
Sunnyvale-based company security organization Proofpoint attributed the action to a politically motivated danger actor it tracks as TA402, and identified by other monikers this sort of as Molerats and GazaHackerTeam.
The risk actor is thought to be lively for a 10 years, with a heritage of hanging organizations largely found in Israel and Palestine, and spanning various verticals these as technology, telecommunications, finance, academia, navy, media, and governments.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The most up-to-date wave of attacks commenced with spear-phishing e-mails created in Arabic and containing PDF attachments that come embedded with a malicious geofenced URL to selectively immediate victims to a password-secured archive only if the source IP tackle belongs to the targeted nations around the world in the Middle East.
Recipients who drop outside of the target group are diverted to a benign decoy web page, usually Arabic language news web-sites like Al Akhbar (www.al-akhbar.com) and Al Jazeera (www.aljazeera.net).
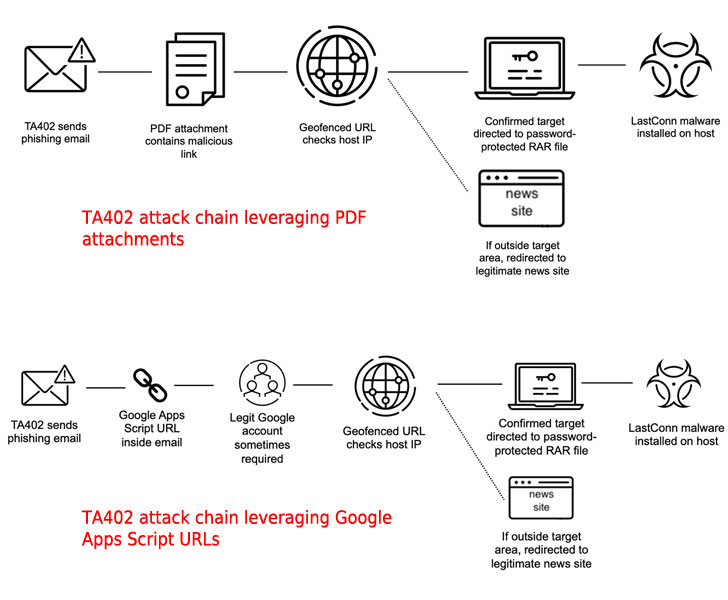
“The password protection of the destructive archive and the geofenced delivery technique are two quick anti-detection mechanisms menace actors can use to bypass computerized investigation merchandise,” the researchers mentioned.
The very last phase in the an infection chain associated extracting the archive to fall a tailor made implant called LastConn, which Proofpoint stated is an upgraded or new model of a backdoor known as SharpStage that was disclosed by Cybereason scientists in December 2020 as part of a Molerats espionage campaign focusing on the Middle East.

Moreover exhibiting a decoy document when LastConn is operate for the initial time, the malware depends seriously on Dropbox API to down load and execute information hosted on the cloud services, in addition to operating arbitrary commands and capturing screenshots, the outcomes of which are subsequently exfiltrated again to Dropbox.
If just about anything, the at any time-evolving toolset of TA402 underscores the group’s ongoing concentrate on producing and modifying custom made malware implants in an try to sneak past defenses and thwart detection.
“TA402 is a hugely productive and capable risk actor that remains a significant danger, primarily to entities operating in and doing work with government or other geopolitical entities in the Middle East,” the researchers concluded. “It is probable TA402 proceeds its concentrating on mostly concentrated on the Center East area.”
Discovered this post appealing? Follow THN on Facebook, Twitter and LinkedIn to go through much more exceptional content we article.
Some elements of this post are sourced from:
thehackernews.com


 UK government to consider gutting GDPR rules
UK government to consider gutting GDPR rules