A new Android banking trojan with over 50,000 installations has been observed distributed through the formal Google Engage in Retailer with the intention of focusing on 56 European banking companies and carrying out harvesting delicate info from compromised units.
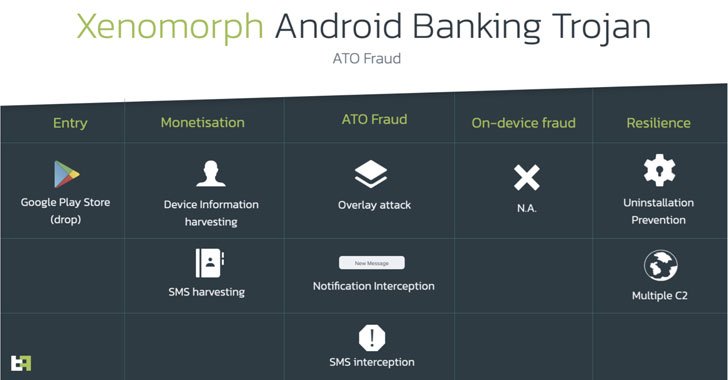
Dubbed Xenomorph by Dutch security agency ThreatFabric, the in-improvement malware is claimed to share overlaps with yet another banking trojan tracked beneath the moniker Alien although also remaining “radically distinct” from its predecessor in conditions of the functionalities available.
“Regardless of remaining a perform-in-development, Xenomorph is currently sporting efficient overlays and remaining actively dispersed on formal application shops,” ThreatFabric’s founder and CEO, Han Sahin, mentioned. “In addition, it features a really detailed and modular engine to abuse accessibility expert services, which in the long run could ability really highly developed abilities, like ATS.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Alien, a distant entry trojan (RAT) with notification sniffing and authenticator-based 2FA theft functions, emerged shortly after the demise of the infamous Cerberus malware in August 2020. Because then, other forks of Cerberus have been noticed in the wild, which includes ERMAC in September 2021.
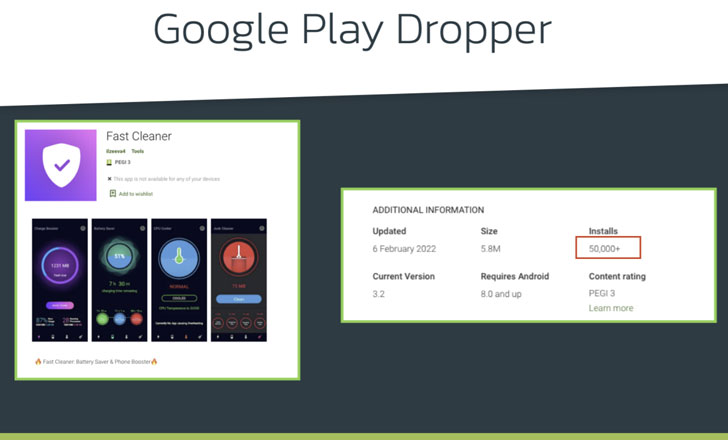
Xenomorph, like Alien and ERMAC, is but yet another case in point of an Android banking trojan which is targeted on circumventing Google Play Store’s security protections by masquerading as productivity applications these kinds of as “Fast Cleaner” to trick unaware victims into putting in the malware.
It is value noting that a conditioning education dropper app with in excess of 10,000 installations — dubbed GymDrop — was discovered providing the Alien banking trojan payload in November by masking it as a “new package of workout workout routines.”
Quick Cleaner, which has the offer name “vizeeva.rapidly.cleaner” and continues to offered on the app retail store, has been most popular in Portugal and Spain, data from cellular app current market intelligence company Sensor Tower reveals, with the application producing its to start with visual appearance in the Perform Retail outlet in the direction of the conclude of January 2022.
What is actually a lot more, assessments for the application from consumers warned that “this app has malware” and that it “question[s] for an update to be verified continually.” Yet another person stated: “It puts malware on the device and apart from that it has a self-protection system so that you are not able to uninstall it.”
Also put to use by Xenomorph is the time-tested tactic of prompting the victims to grant it Accessibility Service privileges and abuse the permissions to carry out overlay attacks, whereby the malware injects rogue overlay screens atop targeted apps from Spain, Portugal, Italy, and Belgium to siphon credentials and other private facts.
Furthermore, it can be geared up with a notification interception function to extract two-factor authentication tokens gained by using SMS, and get the record of put in apps, the success of which are exfiltrated to a remote command-and-manage server.
“The surfacing of Xenomorph reveals, as soon as yet again, that threat actors are focusing their attention on landing applications on formal markets,” the researchers claimed. “Present day Banking malware is evolving at a extremely rapid amount, and criminals are setting up to undertake far more refined development practices to assistance potential updates.”
Found this posting fascinating? Observe THN on Fb, Twitter and LinkedIn to go through far more exceptional content we post.
Some components of this post are sourced from:
thehackernews.com



 Iranian State Broadcaster IRIB Hits by Destructive Wiper Malware
Iranian State Broadcaster IRIB Hits by Destructive Wiper Malware