Hardware security keys—such as all those from Google and Yubico—are considered the most secure indicates to defend accounts from phishing and takeover attacks.
But a new analysis printed on Thursday demonstrates how an adversary in possession of these kinds of a two-factor authentication (2FA) system can clone it by exploiting an electromagnetic facet-channel in the chip embedded in it.
The vulnerability (tracked as CVE-2021-3011) will allow the undesirable actor to extract the encryption important or the ECDSA non-public key joined to a victim’s account from a FIDO Common 2nd Factor (U2F) unit like Google Titan Key or YubiKey, hence completely undermining the 2FA protections.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The adversary can indication in to the victim’s application account without the U2F system, and without the need of the target noticing,” NinjaLab scientists Victor Lomne and Thomas Roche said in a 60-website page investigation.
“In other words the adversary developed a clone of the U2F product for the victim’s software account. This clone will give obtain to the application account as lengthy as the legit person does not revoke its next factor authentication qualifications.”
The complete list of products and solutions impacted by the flaw incorporates all versions of Google Titan Security Vital (all versions), Yubico Yubikey Neo, Feitian FIDO NFC USB-A / K9, Feitian MultiPass FIDO / K13, Feitian ePass FIDO USB-C / K21, and Feitian FIDO NFC USB-C / K40.
Moreover the security keys, the attack can also be carried out on NXP JavaCard chips, like NXP J3D081_M59_DF, NXP J3A081, NXP J2E081_M64, NXP J3D145_M59, NXP J3D081_M59, NXP J3E145_M64, and NXP J3E081_M64_DF, and their respective variants.
The vital-restoration attack, although doubtless severe, needs to satisfy a selection of prerequisites in buy to be thriving.
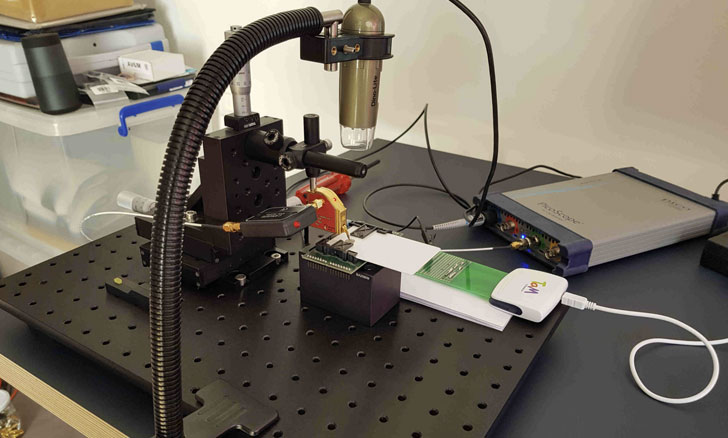
An actor will have 1st to steal the target’s login and password of an account secured by the actual physical essential, then stealthily get access to Titan Security Essential in issue, not to mention receive costly machines costing north of $12,000, and have ample knowledge to build custom application to extract the essential linked to the account.
“It is however safer to use your Google Titan Security Crucial or other impacted goods as a FIDO U2F two-factor authentication token to indicator in to purposes instead than not applying one particular,” the researchers reported.
To clone the U2F vital, the scientists set about the endeavor by tearing the unit down utilizing a warm air gun to take away the plastic casing and expose the two microcontrollers soldered in it — a safe enclave (NXP A700X chip) that is made use of to complete the cryptographic operations and standard-purpose chip that acts as a router concerning the USB/NFC interfaces and the authentication microcontroller.
At the time this is accomplished, the scientists say it is feasible to glean the ECDSA encryption essential via a facet-channel attack by observing the electromagnetic radiations coming off the NXP chip throughout ECDSA signatures, the main cryptographic operation of the FIDO U2F protocol that is performed when a U2F crucial is registered for the first time to function with a new account.
A aspect-channel attack normally will work primarily based on facts obtained from the implementation of a personal computer procedure, alternatively than exploiting a weak spot in the software package. Typically, such attacks leverage timing information, electrical power usage, electromagnetic leaks, and acoustic indicators as a supply of details leakage.
By acquiring 6,000 this kind of aspect-channel traces of the U2F authentication request instructions around a 6-hour period of time, the researchers mentioned they ended up ready to get better the ECDSA non-public vital linked to a FIDO U2F account established for the experiment utilizing an unsupervised device understanding model.
Whilst the security of a components security important is just not diminished by the earlier mentioned attack owing to the restrictions involved, exploitation in the wild is not inconceivable.
“However, this operate demonstrates that the Google Titan Security Vital (or other impacted goods) would not avoid [an] unnoticed security breach by attackers eager to set plenty of effort into it,” the scientists concluded. “Customers that experience these a threat need to in all probability swap to other FIDO U2F components security keys, in which no vulnerability has however been uncovered.”
Found this short article fascinating? Stick to THN on Fb, Twitter and LinkedIn to browse much more special material we post.
Some pieces of this post are sourced from:
thehackernews.com


 FBI Warns of Egregor Attacks on Businesses Worldwide
FBI Warns of Egregor Attacks on Businesses Worldwide