A beforehand undocumented backdoor has been noticed concentrating on Linux programs with the purpose of corralling the machines into a botnet and acting as a conduit for downloading and putting in rootkits.
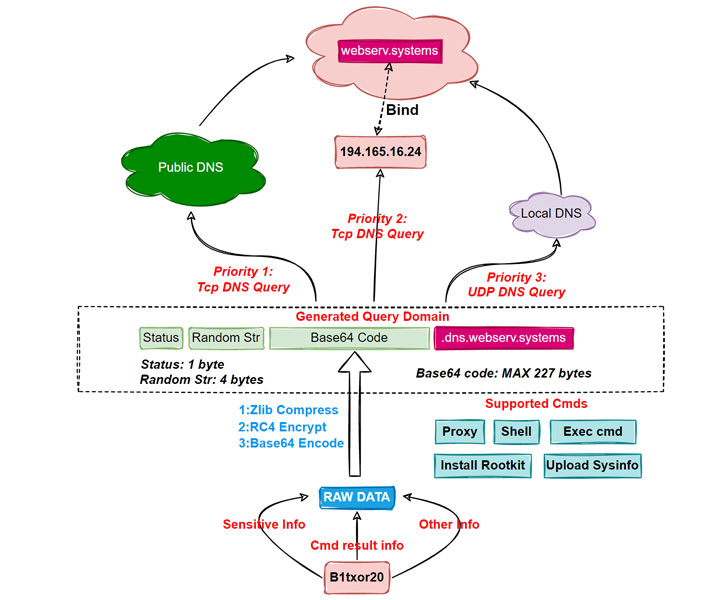
Qihoo 360’s Netlab security workforce named it B1txor20 “based on its propagation applying the file title ‘b1t,’ the XOR encryption algorithm, and the RC4 algorithm important length of 20 bytes.”


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Initial noticed propagating by means of the Log4j vulnerability on February 9, 2022, the malware leverages a strategy known as DNS tunneling to construct interaction channels with command-and-control (C2) servers by encoding knowledge in DNS queries and responses.
B1txor20, when also buggy in some strategies, now supports the ability to get hold of a shell, execute arbitrary commands, set up a rootkit, open a SOCKS5 proxy, and capabilities to add delicate details back to the C2 server.
After a equipment is properly compromised, the malware utilizes the DNS tunnel to retrieve and execute commands sent by the server.
“Bot sends the stolen sensitive details, command execution success, and any other details that wants to be delivered, soon after hiding it employing distinct encoding tactics, to C2 as a DNS ask for,” the scientists elaborated.
“Soon after receiving the ask for, C2 sends the payload to the Bot side as a response to the DNS ask for. In this way, Bot and C2 accomplish conversation with the help of DNS protocol.”
A whole of 15 instructions are applied, chief amid them currently being uploading technique information, executing arbitrary process instructions, looking at and composing information, starting off and stopping proxy solutions, and generating reverse shells.
Uncovered this posting intriguing? Stick to THN on Fb, Twitter and LinkedIn to read through much more distinctive content material we write-up.
Some pieces of this write-up are sourced from:
thehackernews.com



 New Infinite Loop Bug in OpenSSL Could Let Attackers Crash Remote Servers
New Infinite Loop Bug in OpenSSL Could Let Attackers Crash Remote Servers