Unknown risk actors have deployed a new backdoor that borrows its attributes from the U.S. Central Intelligence Company (CIA)’s Hive multi-system malware suite, the resource code of which was introduced by WikiLeaks in November 2017.
“This is the 1st time we caught a variant of the CIA Hive attack package in the wild, and we named it xdr33 based on its embedded Bot-side certification CN=xdr33,” Qihoo Netlab 360’s Alex Turing and Hui Wang explained in a specialized compose-up published very last week.
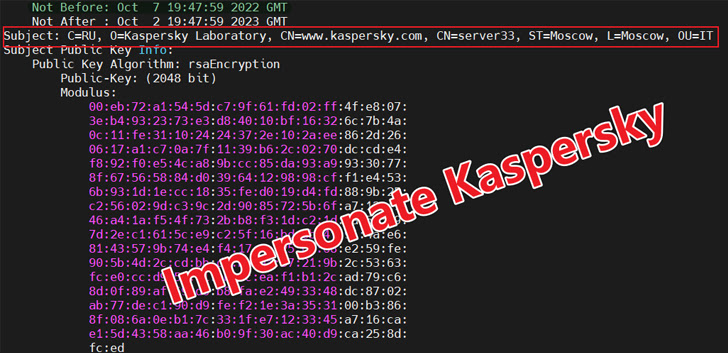
xdr33 is reported to be propagated by exploiting a security vulnerability in the F5 appliance and speaking with a command-and-command (C2) server using SSL with forged Kaspersky certificates.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The intent of the backdoor, for each the Chinese cybersecurity organization, is to harvest sensitive info and act as a launchpad for subsequent intrusions. It improves upon Hive by introducing new C2 instructions and functionalities, amongst other implementation modifications.
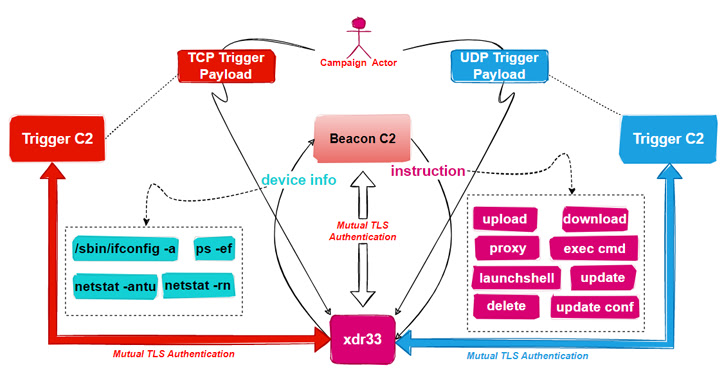
The ELF sample further more operates as a Beacon by periodically exfiltrating system metadata to the distant server and executing commands issued by the C2.
This incorporates the capability to obtain and add arbitrary data files, operate instructions utilizing cmd, and start shell, in addition to updating and erasing traces of by itself from the compromised host.
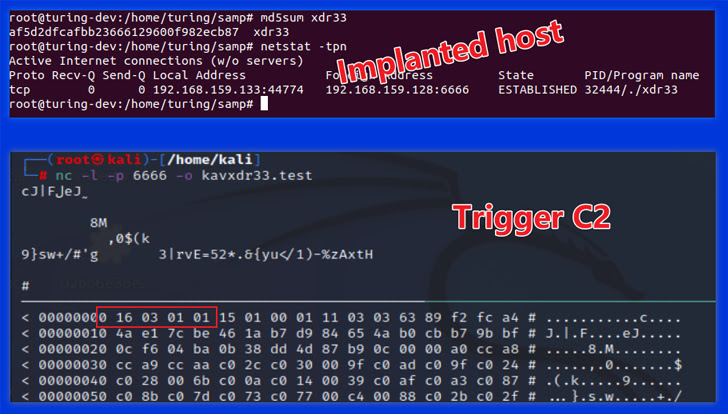
The malware also incorporates a Set off module that is created to eavesdrop on network visitors for a unique “bring about” packet in buy to extract the C2 server stated in the IP packet’s payload, set up connection, and hold out for the execution of commands issued by the C2.
“It is really worth noting that Induce C2 differs from Beacon C2 in the specifics of interaction soon after setting up an SSL tunnel, [the] bot and Cause C2 use a Diffie-Helllman essential exchange to establish a shared crucial, which is utilised in the AES algorithm to generate a second layer of encryption,” the researchers explained.
Found this post intriguing? Comply with us on Twitter and LinkedIn to study extra distinctive content we submit.
Some components of this post are sourced from:
thehackernews.com

 US Court Orders $17m Be Given to BitConnect Victims
US Court Orders $17m Be Given to BitConnect Victims