Cybersecurity researchers have disclosed details of an evasive malware campaign that tends to make use of valid code signing certificates to sneak past security defenses and keep underneath the radar with the target of deploying Cobalt Strike and BitRAT payloads on compromised units.
The binary, a loader, has been dubbed “Blister” by researchers from Elastic Security, with the malware samples having negligible to zero detections on VirusTotal. As of creating, the infection vector used to stage the attack, as very well as the greatest goals of the intrusion, continues to be not known.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
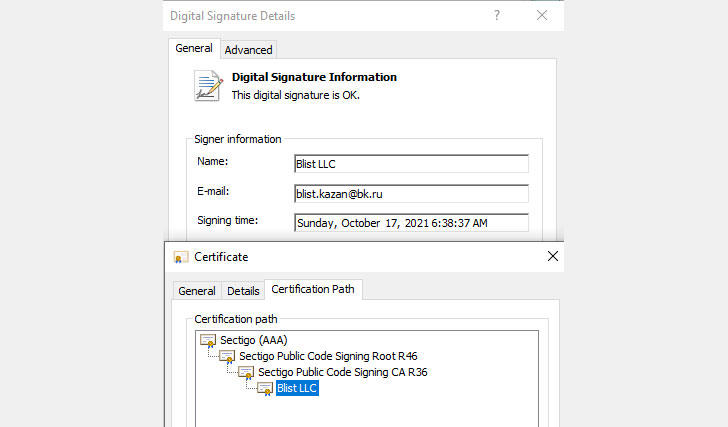
A notable component of the attacks is that they leverage a valid code signing certification issued by Sectigo. The malware has been observed signed with the certification in dilemma courting back to September 15, 2021. Elastic stated it arrived at out to the corporation to assure that the abused certificates are revoked.
“Executables with legitimate code signing certificates are normally scrutinized to a lesser diploma than unsigned executables,” scientists Joe Desimone and Samir Bousseaden explained. “Their use will allow attackers to continue being below the radar and evade detection for a for a longer period period of time.”
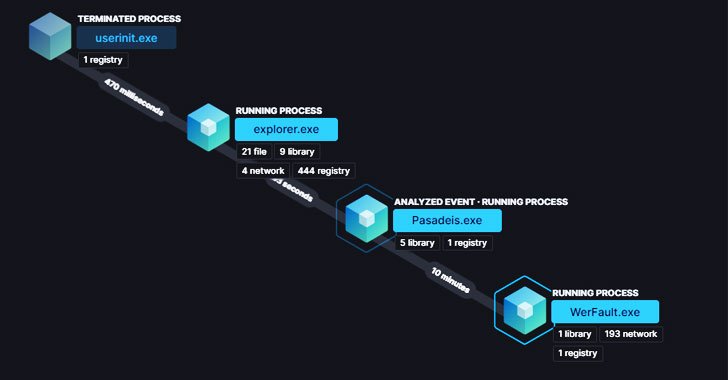
Blister masquerades as a respectable library identified as “colorui.dll” and is shipped by way of a dropper named “dxpo8umrzrr1w6gm.exe.” Put up execution, the loader is intended to slumber for 10 minutes, likely in an attempt to evade sandbox assessment, only to observe it up by developing persistence and decrypting an embedded malware payload these as Cobalt Strike or BitRAT.
“After decrypted, the embedded payload is loaded into the latest method or injected into a newly spawned WerFault.exe [Windows Error Reporting] procedure,” the scientists observed. Extra indicators of compromise (IoCs) associated with the campaign can be accessed here.
Discovered this article fascinating? Follow THN on Fb, Twitter and LinkedIn to browse more exceptional articles we article.
Some pieces of this posting are sourced from:
thehackernews.com


 Russian Hacker’s $1.7M Restitution Order Overturned
Russian Hacker’s $1.7M Restitution Order Overturned