A new variant of an IoT botnet named BotenaGo has emerged in the wild, precisely singling out Lilin security digicam DVR gadgets to infect them with Mirai malware.
Dubbed “Lilin Scanner” by Nozomi Networks, the latest variation is designed to exploit a two-calendar year-previous critical command injection vulnerability in the DVR firmware that was patched by the Taiwanese firm in February 2020.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
BotenaGo, to start with documented in November 2021 by AT&T Alien Labs, is created in Golang and options over 30 exploits for recognised vulnerabilities in web servers, routers and other sorts of IoT devices.
The botnet’s supply code has given that been uploaded to GitHub, making it ripe for abuse by other prison actors. “With only 2,891 lines of code, BotenaGo has the likely to be the starting position for many new variants and new malware family members working with its resource code,” the scientists said this yr.
The new BotenaGo malware is the most recent to exploit vulnerabilities in Lilin DVR equipment following Chalubo, Fbot, and Moobot. Previously this thirty day period, Qihoo 360’s Network Security Investigation Lab (360 Netlab) in depth a rapidly spreading DDoS botnet known as Fodcha that has spread as a result of distinct N-Day flaws and weak Telnet/SSH passwords.
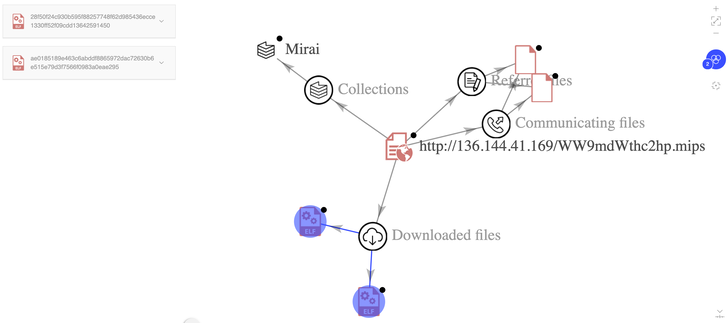
Just one essential facet sets Lillin Scanner apart from BotenaGo is its reliance on an exterior plan to develop an IP deal with checklist of vulnerable Lilin gadgets, subsequently exploiting the aforementioned flaw to execute arbitrary code remotely on the focus on and deploy Mirai payloads.

It is really truly worth noting that the malware can’t propagate itself in a worm-like trend, and can only be employed to strike the IP addresses provided as input with the Mirai binaries.
“One more conduct connected with the Mirai botnet is the exclusion of IP ranges belonging to the interior networks of the U.S. Department of Defense (DoD), U.S. Postal Assistance (USPS), Common Electrical (GE), Hewlett-Packard (HP), and other individuals,” the researchers explained.
Like Mirai, the emergence of Lilin Scanner details to the reuse of easily available resource code to spawn new malware offshoots.
“Its authors removed almost all of the 30+ exploits existing in BotenaGo’s initial source code,” the scientists reported, incorporating, “it looks that this resource has been rapidly constructed applying the code foundation of the BotenaGo malware.”
Uncovered this write-up attention-grabbing? Abide by THN on Fb, Twitter and LinkedIn to read far more exceptional content we submit.
Some areas of this short article are sourced from:
thehackernews.com

 Ransomware Attacks Cost Universities Over £2m
Ransomware Attacks Cost Universities Over £2m