Cybersecurity researchers on Thursday took the wraps off a new cyberespionage group that has been guiding a sequence of targeted attacks towards diplomatic entities and telecommunication providers in Africa and the Center East considering that at least 2017.
Dubbed “BackdoorDiplomacy,” the marketing campaign will involve concentrating on weak points in internet-exposed units such as web servers to accomplish a panoply of cyber hacking pursuits, like laterally shifting throughout the network to deploy a tailor made implant identified as Turian that is able of exfiltrating delicate information stored in removable media.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“BackdoorDiplomacy shares tactics, procedures, and procedures with other Asia-dependent groups. Turian most likely signifies a future phase evolution of Quarian, the backdoor very last observed in use in 2013 in opposition to diplomatic targets in Syria and the U.S,” explained Jean-Ian Boutin, head of danger investigation at Slovak cybersecurity agency ESET.
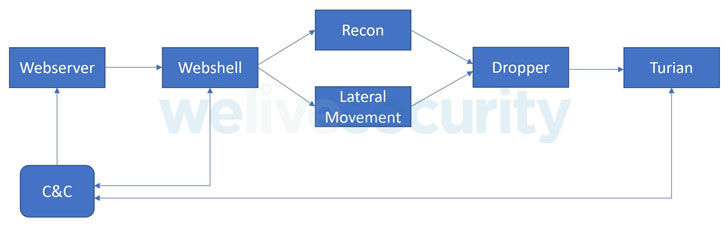
Engineered to concentrate on the two Windows and Linux operating techniques, the cross-system team singles out management interfaces for networking machines and servers with internet-uncovered ports, probable exploiting unpatched vulnerabilities to deploy the China Chopper web shell for original entry, applying it to conduct reconnaissance and install the backdoor.
Qualified systems incorporate F5 Massive-IP gadgets (CVE-2020-5902), Microsoft Exchange servers, and Plesk web hosting regulate panels. Victims have been recognized in the Ministries of Foreign Affairs of multiple African nations, as nicely as in Europe, the Middle East, and Asia. Furthermore, telecom vendors in Africa and at least just one Center Japanese charity have also been strike.

“In each case, operators used related tactics, methods, and processes (TTPs), but modified the tools made use of, even within shut geographic areas, likely to make tracking the team additional difficult,” the researchers mentioned. BackdoorDiplomacy is also believed to overlap with formerly documented campaigns operated by a Chinese-speaking team Kaspersky tracks as “CloudComputating.”
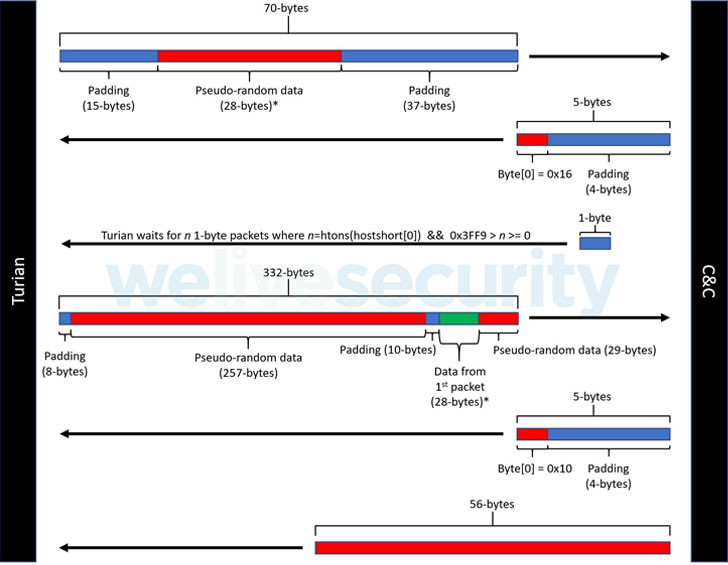
Moreover its capabilities to obtain technique details, choose screenshots, and have out file operations, ESET researchers explained Turian’s network encryption protocol is nearly identical to that utilized by WhiteBird, a C++ backdoor operated by an Asia-based mostly threat actor named Calypso, that was installed within just diplomatic corporations in Kazakhstan and Kyrgyzstan, and throughout the very same timeframe as BackdoorDiplomacy.
Identified this article fascinating? Abide by THN on Fb, Twitter and LinkedIn to study far more exceptional content we write-up.
Some sections of this write-up are sourced from:
thehackernews.com


 U.S. Authorities Shut Down Slilpp—Largest Marketplace for Stolen Logins
U.S. Authorities Shut Down Slilpp—Largest Marketplace for Stolen Logins