The investigation into how the attackers managed to compromise SolarWinds’ interior network and poison the firm’s software package updates are still underway, but we could one action close to comprehending what seems to be a extremely meticulously planned and remarkably-sophisticated offer chain attack.
A new report posted by ReversingLabs these days and shared in advance with The Hacker News has unveiled that the operators behind the espionage marketing campaign probably managed to compromise the computer software establish and code signing infrastructure of SolarWinds Orion system as early as Oct 2019 to supply the destructive backdoor by its program release method.
“The resource code of the impacted library was immediately modified to consist of destructive backdoor code, which was compiled, signed, and sent by means of the current software program patch launch management technique,” ReversingLabs’ Tomislav Pericin reported.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Cybersecurity firm FireEye previously this 7 days comprehensive how a number of SolarWinds Orion software updates, launched involving March and June 2020, were being injected with backdoor code (“SolarWinds.Orion.Core.BusinessLayer.dll” or SUNBURST) to carry out surveillance and execute arbitrary commands on goal devices.
FireEye has not so considerably publicly attributed the attack to any specific country-condition actor, but several media reports have pinned the intrusion campaign on APT29 (aka Cozy Bear), a hacker group connected with Russia’s foreign intelligence company.
Sneaky Injection of Malicious Code
While the very first model containing the tainted Orion program was traced to 2019.4.5200.9083, ReversingLabs has found that an previously version 2019.4.5200.8890, unveiled in Oct 2019, also incorporated seemingly harmless modifications that acted as the stepping stone for delivering the genuine attack payload down the line.
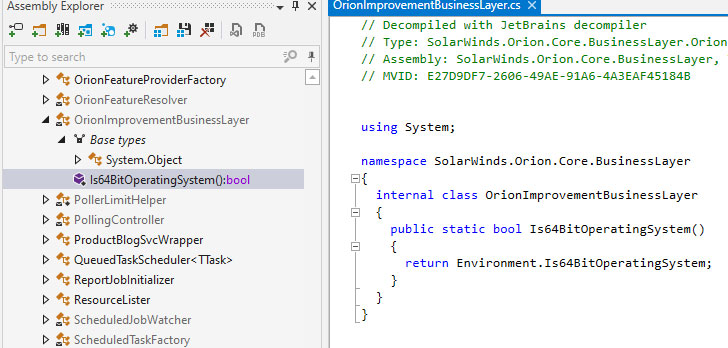 Empty .NET course prior to backdoor code addition [ver. 2019.4.5200.8890]
Empty .NET course prior to backdoor code addition [ver. 2019.4.5200.8890]
The notion, according to Pericin, was to compromise the build technique, quietly inject their possess code in the resource code of the program, hold out for the organization to compile, indicator packages and at final, verify if their modifications display up in the recently unveiled updates as predicted.
At the time verified, the adversary then took actions to mix the SUNBURST malware with the rest of the codebase by mimicking existing features (GetOrCreateUserID) but introducing their own implementations so as to remain stealthy and invoking them by modifying a different course called “InventoryManager” to generate a new thread that operates the backdoor.
What is actually far more, malicious strings were obscured using a blend of compression and Foundation64 encoding in hopes that undertaking so would thwart YARA policies from recognizing anomalies in the code as properly as a slip by means of undetected during a software program developer assessment.
“The attackers went by way of a ton of hassle to guarantee that their code seems like it belongs within just the code foundation,” Pericin said. “That was unquestionably completed to disguise the code from the audit by the software builders.”
How did the Compromise Come about?
This implies that not only did the attackers have a significant diploma of familiarity with the application, but also the simple fact that its current program launch management procedure by itself was compromised — as the course in question was modified at the resource code degree to construct a new application update containing the backdoored library, then signed, and ultimately unveiled to the customers.
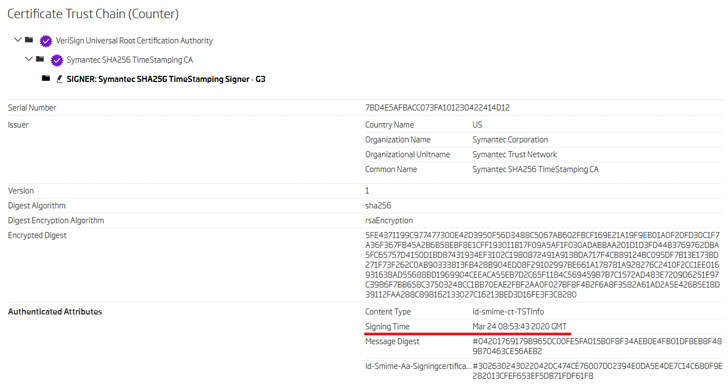
This also raises additional issues than it answers in that a adjust of this magnitude could only have been doable if both the edition command method was compromised or the tainted software was put immediately on the create device.
Though it truly is not promptly clear how the attackers obtained entry to the code base, security researcher Vinoth Kumar’s disclosure about SolarWinds’ update server getting available with the password “solarwinds123” assumes new importance offered the overlap in timelines.
Kumar, in a tweet on December 14, stated he notified the firm of a publicly obtainable GitHub repository that was leaking the firm’s download website’s FTP qualifications in plaintext, including a hacker could use the qualifications to add a destructive executable and increase it to a SolarWinds update.
“That Github repo was open up to the general public considering the fact that June 17 2018,” Kumar explained, ahead of the misconfiguration was tackled on November 22, 2019.
“SUNBURST illustrates the future generation of compromises that thrive on obtain, sophistication and persistence,” Pericin concluded. “For organizations that operate valuable organizations or generate software critical to their clients, inspecting software program and checking updates for symptoms of tampering, destructive or unwelcome additions must be component of the risk management system.”
“Hiding in plain sight behind a globally recognized program model or a trusted enterprise-critical process, provides this method accessibility that a phishing marketing campaign could only dream to realize,” he included.
More than 4,000 Sub-domains Compromised by SUNBURST
SolarWinds explained up to 18,000 of its buyers may have been impacted by the provide chain attack though urging Orion platform consumers to update the software to edition 2020.2.1 HF 2 as before long as feasible to safe their environments.
According to security researcher R. Bansal (@0xrb), more than 4,000 sub-domains belonging to prominent companies and educational institutions ended up infected with the SUNBURST backdoor, which include those of Intel, NVIDIA, Kent Point out University, and Iowa Condition University.
“Prolific actors are constantly going soon after substantial-income customers like SolarWinds mainly because they see an elevated likelihood of earning much larger earnings by advertising access to ransomware companions and other purchasers,” cybersecurity firm Intel 471 reported, responding to the risk that criminals ended up advertising obtain to the firm’s networks on underground community forums.
“No matter whether it’s by exploiting vulnerabilities, launching spam strategies or leveraging credential abuse, access is commonly marketed and auctioned to the best bidder for a gain. Whether or not this was the enthusiasm for the present-day SolarWinds incident continues to be to be noticed.”
Located this article attention-grabbing? Adhere to THN on Fb, Twitter and LinkedIn to study more exceptional material we publish.
Some sections of this write-up are sourced from:
thehackernews.com


 The SolarWinds Perfect Storm: Default Password, Access Sales and More
The SolarWinds Perfect Storm: Default Password, Access Sales and More