Cybersecurity researchers have elaborated a novel attack technique that weaponizes programmable logic controllers (PLCs) to achieve an initial foothold in engineering workstations and subsequently invade the operational technology (OT) networks.
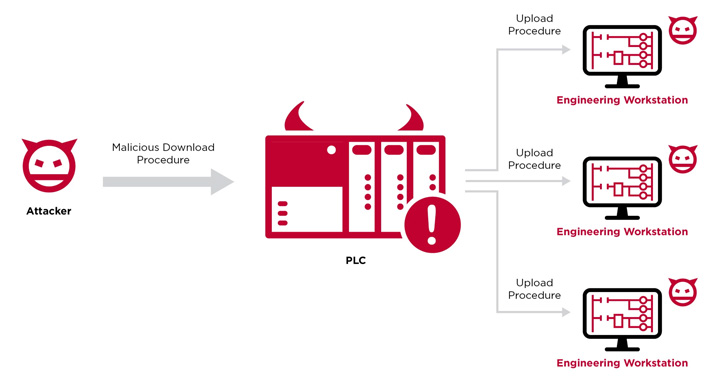
Dubbed “Evil PLC” attack by industrial security agency Claroty, the issue impacts engineering workstation software package from Rockwell Automation, Schneider Electric powered, GE, B&R, Xinje, OVARRO, and Emerson.
Programmable logic controllers (PLCs) are a essential component of industrial units that control manufacturing procedures in critical infrastructure sectors. PLCs, moreover orchestrating the automation responsibilities, are also configured to start off and halt procedures and generate alarms.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
It is really consequently not surprising that the entrenched accessibility offered by PLCs have built the machines a aim of refined attacks for extra than a decade, beginning from Stuxnet to PIPEDREAM (aka INCONTROLLER), with the objective of causing physical disruptions.

“These workstation purposes are usually a bridge concerning operational technology networks and company networks,” Claroty stated. “An attacker who is in a position to compromise and exploit vulnerabilities in an engineering workstation could simply shift on to the inside network, go laterally in between methods, and obtain more access to other PLCs and delicate techniques.”
With the Evil PLC attack, the controller acts as a indicates to an end, allowing the risk actor to breach a workstation, access to all the other PLCs on the network, and even tamper with the controller logic.
Place in different ways, the concept is to “use the PLC as a pivot place to attack the engineers who application and diagnose it and get deeper access to the OT network,” the scientists explained.
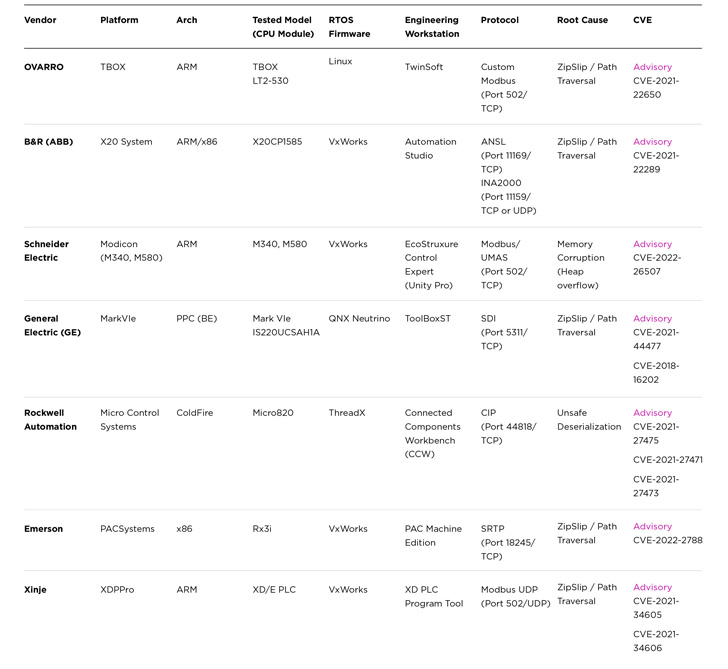
The full sequence performs out as follows: An opportunistic adversary intentionally induces a malfunction on an internet-exposed PLC, an motion that prompts an unsuspecting engineer to connect to the infected PLC employing the engineering workstation software package as a troubleshooting software.
In the next period, the undesirable actor leverages the beforehand undiscovered flaws identified in the platforms to execute destructive code on the workstation when an add operation is executed by the engineer to retrieve a functioning duplicate of the existing PLC logic.
“The simple fact that the PLC merchants more varieties of data that are used by the engineering application and not the PLC alone” produces a circumstance wherein the unused knowledge saved on the PLC can be modified to manipulate the engineering computer software, the scientists pointed out.

“In most conditions, the vulnerabilities exist since the computer software completely reliable details coming from the PLC with out doing in depth security checks.”
In an choice theoretical attack scenario, the Evil PLC method can also be used as honeypots to lure threat actors into connecting to a decoy PLC, top to a compromise of the attacker’s machine.
Claroty further identified as out the absence of security protections in the general public-experiencing industrial manage technique (ICS) products, thus building it simpler for risk actors to alter their logic by means of rogue obtain processes.
To mitigate this kind of attacks, it really is suggested to restrict actual physical and network obtain to PLCs to approved engineers and operators, enforce authentication mechanisms to validate the engineering station, monitor OT network traffic for anomalous activity, and use patches in a well timed vogue.
Identified this post attention-grabbing? Stick to THN on Fb, Twitter and LinkedIn to study far more exceptional material we post.
Some pieces of this write-up are sourced from:
thehackernews.com

 Zoom patches privilege escalation flaw for MacOS users
Zoom patches privilege escalation flaw for MacOS users