A newly found out suspected espionage threat actor has been focusing on employees focusing on mergers and acquisitions as very well as substantial corporate transactions to facilitate bulk email selection from sufferer environments.
Mandiant is monitoring the activity cluster beneath the uncategorized moniker UNC3524, citing a absence of proof linking it to an present team. Even so, some of the intrusions are claimed to mirror tactics utilized by unique Russia-primarily based hacking crews like APT28 and APT29.
“The substantial stage of operational security, lower malware footprint, adept evasive competencies, and a large Internet of Issues (IoT) gadget botnet established this group apart and emphasize the ‘advanced’ in State-of-the-art Persistent Menace,” the danger intelligence organization claimed in a Monday report.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The original entry route is not known but on gaining a foothold, attack chains involving UNC3524 culminate in the deployment of a novel backdoor called QUIETEXIT for persistent remote entry for as very long as 18 months with out having detected in some conditions.
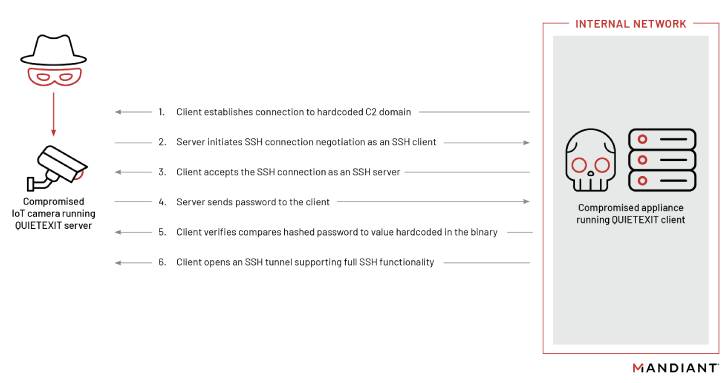
What is actually much more, the command-and-regulate domains — a botnet of internet-uncovered IP digicam units, most likely with default qualifications — are developed to mix in with respectable traffic originating from the infected endpoints, suggesting attempts on the section of the danger actor to stay underneath the radar.
“UNC3524 also usually takes persistence critically,” Mandiant researchers pointed out. “Every time a target atmosphere eliminated their accessibility, the team squandered no time re-compromising the environment with a wide variety of mechanisms, right away restarting their facts theft marketing campaign.”

Also set up by the danger actor is a secondary implant, a web shell, as a signifies of alternate access need to QUIETEXIT halt functioning and for propagating the principal backdoor on another program in the network.
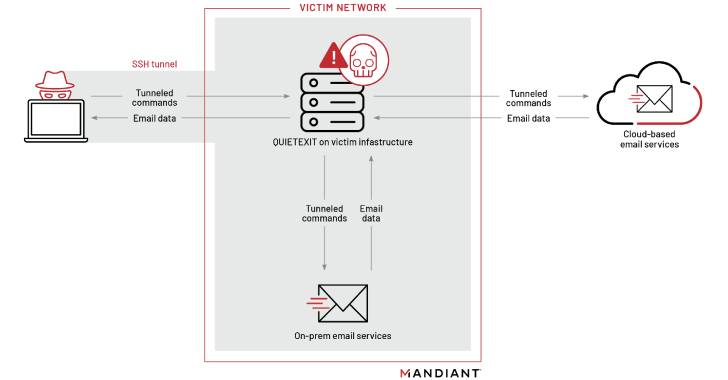
The info-collecting mission, in its ultimate phase, entails acquiring privileged qualifications to the victim’s mail atmosphere, utilizing it to goal the mailboxes of govt groups that function in corporate improvement.
“UNC3524 targets opaque network appliances because they are typically the most unsecure and unmonitored devices in a sufferer atmosphere,” Mandiant mentioned. “Businesses should really choose methods to stock their gadgets that are on the network and do not guidance checking instruments.”
Found this post appealing? Abide by THN on Fb, Twitter and LinkedIn to examine far more exceptional articles we article.
Some areas of this report are sourced from:
thehackernews.com

 GitHub Says Recent Attack Involving Stolen OAuth Tokens Was “Highly Targeted”
GitHub Says Recent Attack Involving Stolen OAuth Tokens Was “Highly Targeted”