A danger actor of probable Pakistani origin has been attributed to however yet another marketing campaign created to backdoor targets of desire with a Windows-dependent distant accessibility trojan named CrimsonRAT since at least June 2021.
“Transparent Tribe has been a highly energetic APT team in the Indian subcontinent,” Cisco Talos scientists stated in an analysis shared with The Hacker Information. “Their main targets have been federal government and military personnel in Afghanistan and India. This campaign furthers this concentrating on and their central aim of developing lengthy expression entry for espionage.”


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Very last thirty day period, the state-of-the-art persistent danger expanded its malware toolset to compromise Android devices with a backdoor named CapraRAT that reveals a significant “diploma of crossover” with CrimsonRAT.
The newest established of attacks detailed by Cisco Talos consists of earning use of faux domains that mimic genuine authorities and similar businesses to deliver the malicious payloads, together with a Python-primarily based stager used to put in .NET-dependent reconnaissance instruments and RATs as perfectly as a barebones .NET-based mostly implant to operate arbitrary code on the infected technique.
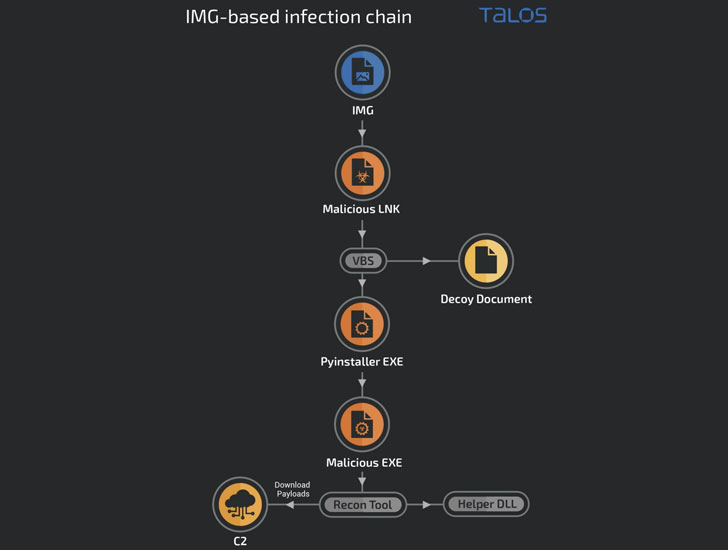
Other than regularly evolving their deployment ways and destructive functionalities, Transparent Tribe is acknowledged to depend on a wide variety of shipping procedures, these as executables impersonating installers of respectable purposes, archive information, and weaponized files to concentrate on Indian entities and people.
One of the downloader executables masquerades as Kavach (which means “armor” in Hindi), an Indian authorities-mandated two-factor authentication resolution demanded for accessing email solutions, in buy to provide the malicious artifacts.
Also set to use are COVID-19-themed decoy photos and virtual really hard disk files (aka VHDX documents) that are employed as a launchpad for retrieving more payloads from a distant command-and-manage server, these kinds of as the CrimsonRAT, which is utilized to get delicate data and create extensive-term obtain into target networks.
“The use of various forms of supply cars and new bespoke malware that can be easily modified for agile operations indicates that the team is intense and persistent, nimble, and regularly evolving their strategies to infect targets,” the scientists claimed.
Uncovered this article interesting? Stick to THN on Facebook, Twitter and LinkedIn to read through extra exceptional content we put up.
Some parts of this posting are sourced from:
thehackernews.com



 Cyber incidents targeting UK financial services providers surged in 2021
Cyber incidents targeting UK financial services providers surged in 2021