A recent Hive ransomware attack carried out by an affiliate involved the exploitation of “ProxyShell” vulnerabilities in the Microsoft Exchange Server that were disclosed last year to encrypt an unnamed customer’s network.
“The actor managed to achieve its malicious goals and encrypt the environment in less than 72 hours from the initial compromise,” Varonis security researcher, Nadav Ovadia, said in a post-mortem analysis of the incident.
Hive, which was first observed in June 2021, follows the lucrative ransomware-as-a-service (RaaS) scheme adopted by other cybercriminal groups in recent years, enabling affiliates to deploy the file-encrypting malware after gaining a foothold into their victims’ networks.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

ProxyShell — tracked as CVE-2021-31207, CVE-2021-34523, and CVE-2021-34473 — involves a combination of security feature bypass, privilege escalation, and remote code execution in the Microsoft Exchange Server, effectively granting the attacker the ability to execute arbitrary code on affected servers.
The issues were addressed by Microsoft as part of its Patch Tuesday updates for April and May 2021.
In this case, successful exploitation of the flaws allowed the adversary to deploy web shells on the compromised server, using them to run malicious PowerShell code with SYSTEM privileges to create a new backdoor administrator user, hijack the domain admin account, and perform lateral movement.
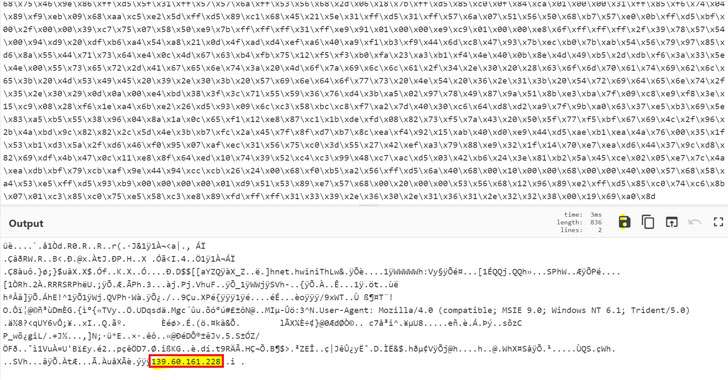
The web shells used in the attack are said to have been sourced from a public git repository and given filenames containing a random mix of characters to evade detection, Ovadia said. Also executed was an additional obfuscated PowerShell script that’s part of the Cobalt Strike framework.

From there, the threat actor moved to scan the network for valuable files, before proceeding to deploy the Golang ransomware executable (named “Windows.exe”) to complete the encryption process and display the ransom note to the victim.
Other operations carried out by the malware include deleting shadow copies, turning off security products, and clearing Windows event logs to avoid detection, prevent recovery, and ensure that the encryption happens without any hiccup.
If anything, the findings are yet another indicator that patching for known vulnerabilities is key to thwarting cyberattacks and other nefarious activities.
“Ransomware attacks have grown significantly over the past years and remain the preferred method of threat actors aiming to maximize profits,” Ovadia said. “It may potentially harm an organization’s reputation, disrupt regular operations and lead to temporary, and possibly permanent, loss of sensitive data.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
Some parts of this article are sourced from:
thehackernews.com

 REvil ransomware group’s infrastructure comes back online hinting at fresh campaign
REvil ransomware group’s infrastructure comes back online hinting at fresh campaign