A social engineering marketing campaign leveraging occupation-themed lures is weaponizing a several years-old distant code execution flaw in Microsoft Office to deploy Cobalt Strike beacons on compromised hosts.
“The payload learned is a leaked variation of a Cobalt Strike beacon,” Cisco Talos scientists Chetan Raghuprasad and Vanja Svajcer said in a new examination published Wednesday.
“The beacon configuration is made up of commands to accomplish specific course of action injection of arbitrary binaries and has a significant reputation domain configured, exhibiting the redirection strategy to masquerade the beacon’s site visitors.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The destructive action, identified in August 2022, makes an attempt to exploit the vulnerability CVE-2017-0199, a remote code execution issue in Microsoft Office environment, that enables an attacker to get management of an influenced system.
The entry vector for the attack is a phishing email containing a Microsoft Term attachment that employs occupation-themed lures for roles in the U.S. governing administration and General public Services Affiliation, a trade union dependent in New Zealand.
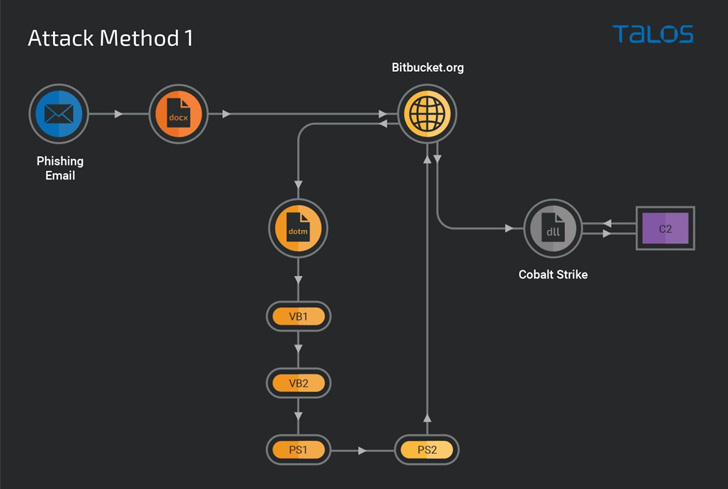
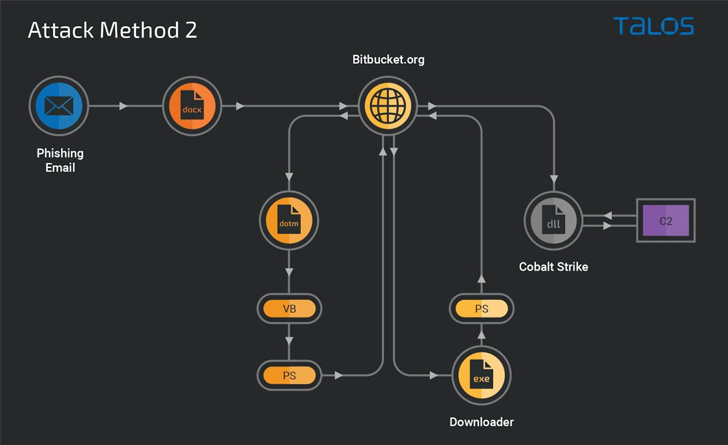
Cobalt Strike beacons are far from the only malware samples deployed, for Cisco Talos stated it has also observed the use of the Redline Stealer and Amadey botnet executables as payloads at the other finish of the attack chain.
Contacting the attack methodology “very modularized,” the cybersecurity corporation said the attack also stands out for its use of Bitbucket repositories to host malicious content material that serves as a beginning issue for downloading a Windows executable liable for deploying the Cobalt Strike DLL beacon.

In an choice attack sequence, the Bitbucket repository functions as a conduit to supply obfuscated VB and PowerShell downloader scripts to set up the beacon hosted on a unique Bitbucket account.
“This campaign is a typical case in point of a risk actor utilizing the system of producing and executing malicious scripts in the victim’s technique memory,” the researchers reported.
“Organizations must be frequently vigilant on the Cobalt Strike beacons and implement layered protection abilities to thwart the attacker’s tries in the before stage of the attack’s infection chain.”
Found this report exciting? Abide by THN on Fb, Twitter and LinkedIn to read through extra distinctive content material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Why Organisations Need Both EDR and NDR for Complete Network Protection
Why Organisations Need Both EDR and NDR for Complete Network Protection