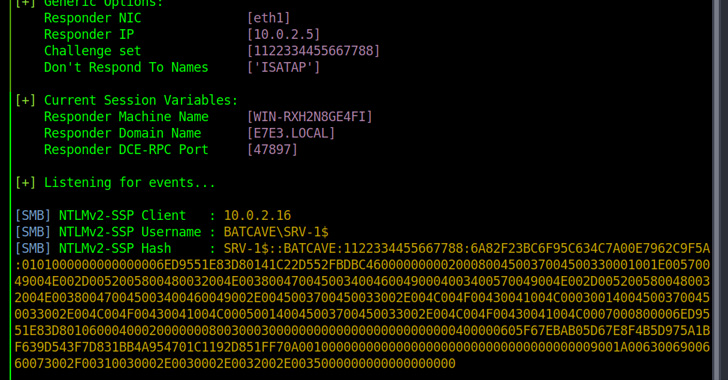
A new form of Windows NTLM relay attack dubbed DFSCoerce has been uncovered that leverages the Dispersed File Process (DFS): Namespace Administration Protocol (MS-DFSNM) to seize command of a area.
“Spooler support disabled, RPC filters installed to avoid PetitPotam and File Server VSS Agent Provider not installed but you nevertheless want to relay [Domain Controller authentication to [Active Directory Certificate Services]? Really don’t worry MS-DFSNM have (sic) your again,” security researcher Filip Dragovic said in a tweet.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
MS-DFSNM provides a distant procedure phone (RPC) interface for administering dispersed file process configurations.
The NTLM (NT Lan Manager) relay attack is a properly-acknowledged method that exploits the obstacle-reaction system. It will allow malicious functions to sit involving shoppers and servers and intercept and relay validated authentication requests in order to gain unauthorized access to network resources, correctly gaining an first foothold in Active Directory environments.
The discovery of DFSCoerce follows a related strategy known as PetitPotam that abuses Microsoft’s Encrypting File Method Distant Protocol (MS-EFSRPC) to coerce
Windows servers, which include domain controllers, into authenticating with a relay beneath an attacker’s command, allowing threat actors most likely choose above an full domain.

“By relaying an NTLM authentication request from a domain controller to the Certification Authority Web Enrollment or the Certificate Enrollment Web Support on an Ad CS method, an attacker can attain a certification that can be utilised to get a Ticket Granting Ticket (TGT) from the domain controller,” the CERT Coordination Heart (CERT/CC) mentioned, detailing the attack chain.
To mitigate NTLM relay attacks, Microsoft recommends enabling protections like Prolonged Protection for Authentication (EPA), SMB signing, and turning off HTTP on Advert CS servers.
Located this short article appealing? Comply with THN on Fb, Twitter and LinkedIn to read extra exclusive information we submit.
Some components of this short article are sourced from:
thehackernews.com

 Former Amazon Worker Convicted of Capital One Data Breach
Former Amazon Worker Convicted of Capital One Data Breach