A number of rogue Android applications that have been cumulatively mounted from the formal Google Participate in Keep much more than 50,000 moments are currently being applied to focus on banks and other monetary entities.
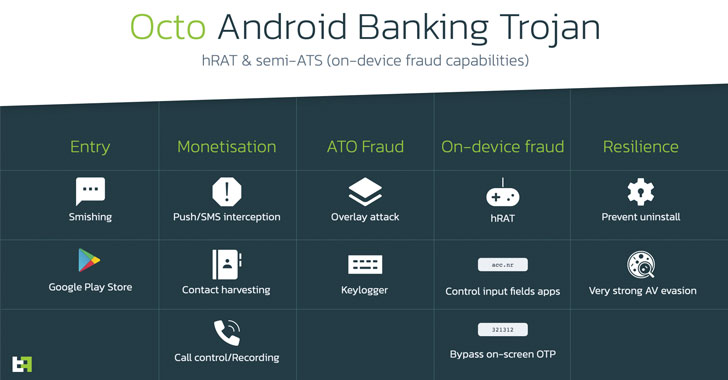
The rental banking trojan, dubbed Octo, is explained to be a rebrand of another Android malware termed ExobotCompact, which, in flip, is a “lite” replacement for its Exobot predecessor, Dutch mobile security agency ThreatFabric mentioned in a report shared with The Hacker Information.
Exobot is also very likely said to have paved the way for a independent descendant referred to as Coper, that was originally identified concentrating on Colombian customers all-around July 2021, with newer bacterial infections targeting Android buyers in various European International locations.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Coper malware apps are modular in design and contain a multi-stage an infection approach and a lot of defensive strategies to endure removing tries,” Cybersecurity firm Cyble pointed out in an evaluation of the malware very last month.

Like other Android banking trojans, the rogue apps are nothing a lot more than droppers, whose primary operate is to deploy the malicious payload embedded in them. The checklist of Octo and Coper droppers used by several menace actors is underneath –
- Pocket Screencaster (com.moh.screen)
- Quickly Cleaner 2021 (vizeeva.rapidly.cleaner)
- Engage in Keep (com.restthe71)
- Postbank Security (com.carbuildz)
- Pocket Screencaster (com.cutthousandjs)
- BAWAG PSK Security (com.frontwonder2), and
- Perform Retail store app install (com.theseeye5)
These apps, which pose as Enjoy Shop application installer, monitor recording, and economic applications, are “powered by ingenious distribution schemes,” distributing them by means of the Google Perform retail store and by means of fraudulent landing web pages that purportedly inform buyers to download a browser update.
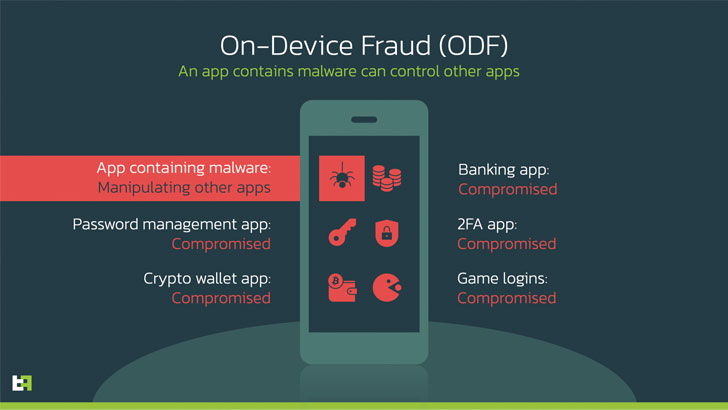
The droppers, when installed, act as a conduit to start the trojans, but not right before requesting users to permit the Accessibility Companies that make it possible for it a broad breadth of capabilities to exfiltrate delicate information from the compromised telephones.
Octo, the revised version of ExobotCompact, is also outfitted to accomplish on-unit fraud by getting distant control above the products by taking advantage of the accessibility permissions as nicely as Android’s MediaProjection API to capture display contents in authentic-time.
The ultimate purpose, ThreatFabric stated, is to bring about the “automated initiation of fraudulent transactions and its authorization without the need of guide endeavours from the operator, thus allowing fraud on a significantly greater scale.”
Other noteworthy features of Octo consist of logging keystrokes, carrying out overlay attacks on banking apps to seize credentials, harvesting speak to information, and persistence actions to avoid uninstallation and evade antivirus engines.
“Rebranding to Octo erases past ties to the Exobot supply code leak, inviting several risk actors looking for option to lease an allegedly new and authentic trojan,” ThreatFabric noted.
“Its capabilities place at risk not only explicitly qualified purposes that are targeted by overlay attack, but any software installed on the infected gadget as ExobotCompact/Octo is capable to examine content of any application displayed on the display and offer the actor with adequate details to remotely interact with it and conduct on-gadget fraud (ODF).”
The conclusions occur near on the heels of the discovery of a different Android bankbot named GodFather — sharing overlaps with the Cereberus and Medusa banking trojans — that has been noticed concentrating on banking consumers in Europe beneath the guise of the default Options app to transfer money and steal SMS messages, amid other people.
On leading of that, a new evaluation revealed by AppCensus identified 11 apps with far more than 46 million installations that ended up implanted with a 3rd-party SDK named Coelib that manufactured it doable to capture clipboard articles, GPS information, email addresses, phone figures, and even the user’s modem router MAC address and network SSID.
Observed this article exciting? Follow THN on Facebook, Twitter and LinkedIn to browse extra exceptional written content we write-up.
Some parts of this report are sourced from:
thehackernews.com


 Bank of Ireland Fined €463,000 Over Data Breaches
Bank of Ireland Fined €463,000 Over Data Breaches