A new phishing-as-a-provider (PhaaS or PaaS) system named Greatness has been leveraged by cybercriminals to focus on business users of the Microsoft 365 cloud services due to the fact at least mid-2022, proficiently decreasing the bar to entry for phishing attacks.
“Greatness, for now, is only focused on Microsoft 365 phishing pages, supplying its affiliates with an attachment and website link builder that results in hugely convincing decoy and login pages,” Cisco Talos researcher Tiago Pereira stated.
“It includes functions these as possessing the victim’s email tackle pre-loaded and exhibiting their proper organization brand and background graphic, extracted from the focus on organization’s actual Microsoft 365 login webpage.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
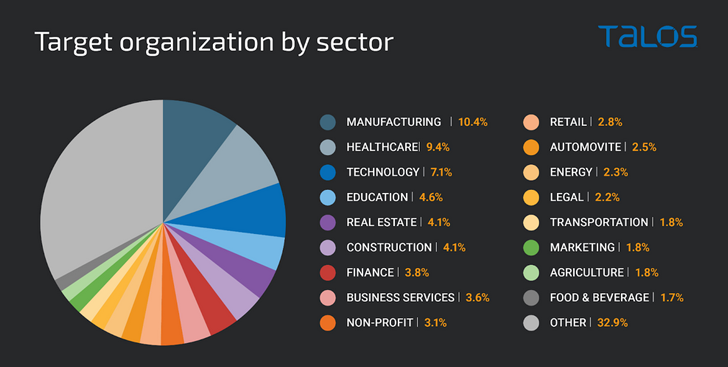
Campaigns involving Greatness have generally producing, health and fitness care, and technology entities situated in the U.S., the U.K., Australia, South Africa, and Canada, with a spike in action detected in December 2022 and March 2023.

Phishing kits like Greatness provide menace actors, rookies or in any other case, a charge-powerful and scalable one-halt store, generating it achievable to layout convincing login webpages associated with different on the web solutions and bypass two-factor authentication (2FA) protections.
Specially, the genuine-wanting decoy webpages function as a reverse proxy to harvest credentials and time-primarily based a single-time passwords (TOTPs) entered by the victims.
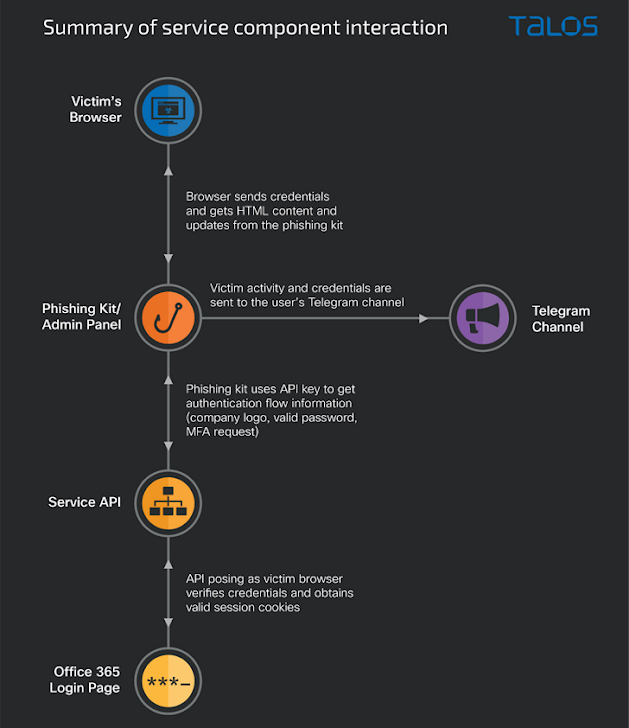
Attack chains start with malicious emails that contains an HTML attachment, which, upon opening, executes obfuscated JavaScript code that redirects the consumer to a landing webpage with the recipient’s email deal with currently pre-stuffed and prompts for their password and MFA code.
The entered qualifications and tokens are subsequently forwarded to the affiliate’s Telegram channel for acquiring unauthorized obtain to the accounts in dilemma.
The AiTM phishing kit also comes with an administration panel that allows the affiliate to configure the Telegram bot, hold track of stolen details, and even develop booby-trapped attachments or one-way links.
Future WEBINARLearn to End Ransomware with Actual-Time Safety
Sign up for our webinar and study how to halt ransomware attacks in their tracks with serious-time MFA and assistance account protection.
Help you save My Seat!
What is actually a lot more, every affiliate is envisioned to have a valid API key in get to be capable to load the phishing page. The API vital also helps prevent undesirable IP addresses from viewing the phishing web site and facilitates driving-the-scenes interaction with the genuine Microsoft 365 login page by posing as the victim.
“Working collectively, the phishing package and the API carry out a ‘man-in-the-middle’ attack, requesting info from the target that the API will then submit to the legitimate login website page in true time,” Pereira stated.
“This enables the PaaS affiliate to steal usernames and passwords, alongside with the authenticated session cookies if the target makes use of MFA.”
The conclusions come as Microsoft has begun enforcing amount matching in Microsoft Authenticator thrust notifications as of May well 8, 2023, to make improvements to 2FA protections and fend off prompt bombing attacks.
Located this post intriguing? Observe us on Twitter and LinkedIn to read far more exclusive content material we post.
Some elements of this short article are sourced from:
thehackernews.com

 XWorm Malware Exploits Follina Vulnerability in New Wave of Attacks
XWorm Malware Exploits Follina Vulnerability in New Wave of Attacks