An unnamed governing administration entity associated with the United Arab Emirates (U.A.E.) was targeted by a possible Iranian risk actor to breach the victim’s Microsoft Exchange Server with a “uncomplicated nonetheless efficient” backdoor dubbed PowerExchange.
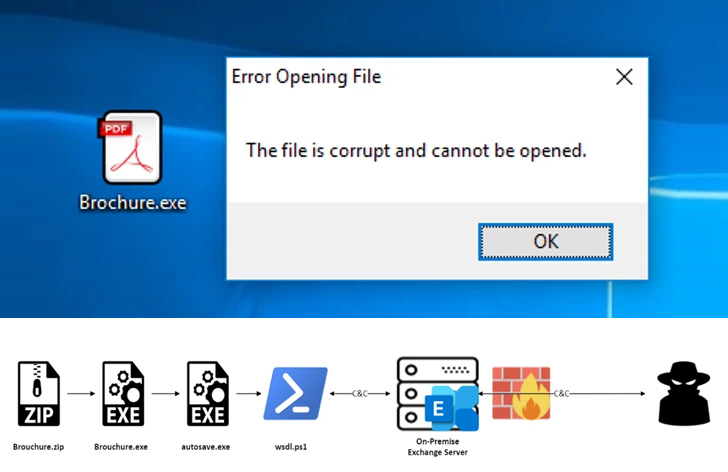
In accordance to a new report from Fortinet FortiGuard Labs, the intrusion relied on email phishing as an original accessibility pathway, primary to the execution of a .NET executable contained with a ZIP file attachment.
The binary, which masquerades as a PDF document, functions as a dropper to execute the closing payload, which then launches the backdoor.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
PowerExchange, penned in PowerShell, employs text files connected to emails for command-and-regulate (C2) communication. It lets the danger actor to run arbitrary payloads and add and obtain documents from and to the technique.
The tailor made implant achieves this by earning use of the Trade Web Services (EWS) API to join to the victim’s Exchange Server and works by using a mailbox on the server to mail and acquire encoded instructions from its operator.
“The Trade Server is available from the internet, conserving C2 conversation to external servers from the equipment in the businesses,” Fortinet researchers claimed. “It also acts as a proxy for the attacker to mask himself.”
That reported, it truly is at the moment not identified how the threat actor managed to get hold of the area credentials to connect to the target Trade Server.
Fortinet’s investigation also uncovered Trade servers that have been backdoored with a number of web shells, 1 of which is known as ExchangeLeech (aka Procedure.Web.ServiceAuthentication.dll), to realize persistent distant entry and steal user credentials.
Forthcoming WEBINARZero Have confidence in + Deception: Study How to Outsmart Attackers!
Learn how Deception can detect sophisticated threats, quit lateral movement, and increase your Zero Have faith in method. Be a part of our insightful webinar!
Preserve My Seat!
PowerExchange is suspected to be an upgraded variation of TriFive, which was previously used by the Iranian nation-phase actor APT34 (aka OilRig) in intrusions targeting governing administration organizations in Kuwait.
Moreover, conversation by using internet-facing Exchange servers is a tried using-and-tested tactic adopted by the OilRig actors, as noticed in the circumstance of Karkoff and MrPerfectionManager.
“Making use of the victim’s Trade server for the C2 channel will allow the backdoor to blend in with benign targeted visitors, thereby making certain that the danger actor can effortlessly avoid just about all network-primarily based detections and remediations inside and outdoors the target organization’s infrastructure,” the scientists explained.
Observed this article attention-grabbing? Observe us on Twitter and LinkedIn to examine a lot more exclusive information we post.
Some components of this post are sourced from:
thehackernews.com


 Alert: Brazilian Hackers Targeting Users of Over 30 Portuguese Banks
Alert: Brazilian Hackers Targeting Users of Over 30 Portuguese Banks