Researchers have disclosed what they say is the 1st-at any time Python-centered ransomware strain exclusively created to goal uncovered Jupyter notebooks, a web-based mostly interactive computing platform that lets modifying and running programs through a browser.
“The attackers attained first accessibility by using misconfigured environments, then ran a ransomware script that encrypts every file on a presented path on the server and deletes itself right after execution to conceal the attack,” Assaf Morag, a details analyst at Aqua Security, mentioned in a report.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The new ransomware sample, which the cloud security business detected after it was trapped in 1 of its honeypot servers, is reported to have been executed right after the unnamed adversary acquired entry to the server and downloaded the essential tools essential to carry out the encryption system by opening a terminal.
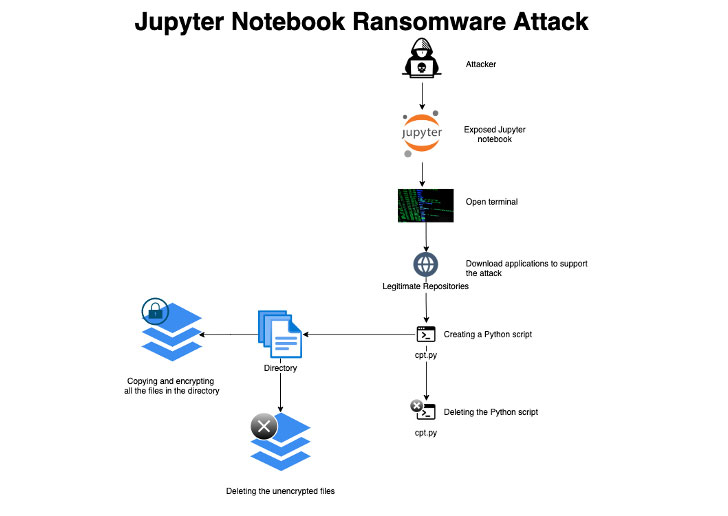
Aqua Security characterised the attack as “easy and uncomplicated,” compared with other common ransomware-as-a-services (RaaS) techniques, incorporating that no ransom observe was introduced on the process, elevating the possibility that the threat actor might have been experimenting with the modus operandi, or that the honeypot timed out right before it could be comprehensive.
The identity of the attacker remains unclear, whilst proof unearthed during the incident investigation factors to an actor of Russian origin, citing similarities with previous cryptomining attacks aimed at Jupyter notebooks.
“Due to the fact Jupyter notebooks are made use of to analyze information and develop information designs, this attack can guide to significant damage to organizations if these environments aren’t thoroughly backed up,” Morag stated.
Identified this post attention-grabbing? Adhere to THN on Fb, Twitter and LinkedIn to read through a lot more unique information we publish.
Some areas of this report are sourced from:
thehackernews.com



 Hackers Increasingly Using ‘Browser in a Browser’ Technique in Ukraine Related Attacks
Hackers Increasingly Using ‘Browser in a Browser’ Technique in Ukraine Related Attacks