The operators of the RansomExx ransomware have turn out to be the newest to create a new variant absolutely rewritten in the Rust programming language, subsequent other strains like BlackCat, Hive, and Luna.
The most up-to-date variation, dubbed RansomExx2 by the danger actor recognized as Hive0091 (aka DefrayX), is largely designed to operate on the Linux operating procedure, while it truly is predicted that a Windows version will be unveiled in the potential.
RansomExx, also recognised as Defray777 and Ransom X, is a ransomware family that is known to be energetic due to the fact 2018. It has considering that been joined to a amount of attacks on governing administration companies, brands, and other superior-profile entities like Embraer and GIGABYTE.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Malware penned in Rust often advantages from reduce [antivirus] detection costs (in contrast to those written in more popular languages) and this could have been the key reason to use the language,” IBM Security X-Pressure researcher Charlotte Hammond said in a report revealed this week.
RansomExx2 is functionally identical to its C++ predecessor and it normally takes a checklist of goal directories to encrypt as command line inputs.
As soon as executed, the ransomware recursively goes as a result of every single of the specified directories, adopted by enumerating and encrypting the data files employing the AES-256 algorithm.
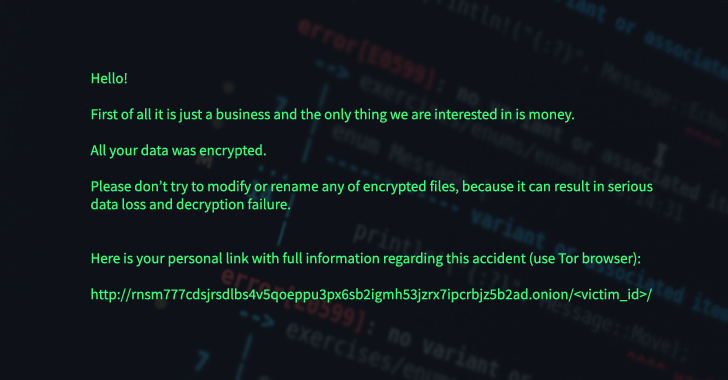
A ransom note containing the demand is in the end dropped in each of the encrypted directory upon completion of the stage.
The growth illustrates a new development where a rising selection of malicious actors are making malware and ransomware with lesser-identified programming languages like Rust and Go, which not only offer you greater cross-platform flexibility but can also evade detection.
“RansomExx is nonetheless another major ransomware family members to switch to Rust in 2022,” Hammond discussed.
“Whilst these latest modifications by RansomExx may well not depict a significant up grade in operation, the swap to Rust implies a ongoing aim on the advancement and innovation of the ransomware by the group, and ongoing makes an attempt to evade detection.”
Observed this write-up appealing? Stick to THN on Fb, Twitter and LinkedIn to go through additional exclusive content we article.
Some areas of this write-up are sourced from:
thehackernews.com

 Japan considers creating new cyber defence agency as attacks ramp up in region
Japan considers creating new cyber defence agency as attacks ramp up in region