An unbiased security researcher has shared what’s a in-depth timeline of gatherings that transpired as the notorious LAPSUS$ extortion gang broke into a third-party supplier linked to the cyber incident at Okta in late January 2022.
In a set of screenshots posted on Twitter, Monthly bill Demirkapi released a two-site “intrusion timeline” allegedly well prepared by Mandiant, the cybersecurity business hired by Sitel to investigate the security breach. Sitel, as a result of its acquisition of Sykes Enterprises in September 2021, is the 3rd-party service supplier that offers client support on behalf of Okta.
The authentication providers company revealed last 7 days that on January 20, it was alerted to a new factor that was extra to a Sitel client assist engineer’s Okta account, an endeavor that it stated was productive and blocked.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The incident only arrived to light-weight two months afterwards soon after LAPSUS$ posted screenshots on their Telegram channel as evidence of the breach on March 22.
The incident, which gave the menace actor accessibility to practically 366 Okta customers, transpired over a 5-working day window amongst January 16 and 21, during which the hackers carried out diverse phases of the attack, together with privilege escalation after getting an preliminary foothold, preserving persistence, lateral motion, and inner reconnaissance of the network.
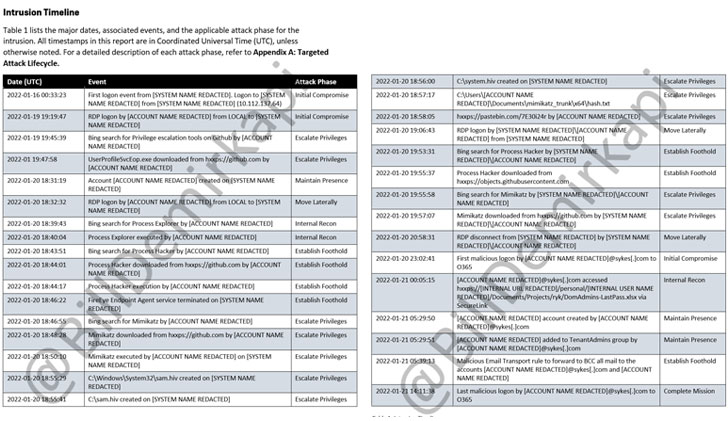
Okta claimed that it experienced shared indicators of compromise with Sitel on January 21 and that it been given a summary report about the incident from Sitel only on March 17.
Subsequently, on March 22, the same working day the felony team shared the screenshots, it obtained a duplicate of the complete investigation report.
“Even when Okta gained the Mandiant report in March explicitly detailing the attack, they ongoing to dismiss the evident signals that their environment was breached until eventually LAPSUS$ shined a highlight on their inaction,” Demirkapi wrote in a tweet thread.
The San Francisco-based organization, in a detailed FAQ posted on March 25, acknowledged that its failure to notify its people about the breach in January was a “oversight.”
“In light of the proof that we have collected in the very last week, it is clear that we would have built a distinctive decision if we experienced been in possession of all of the information that we have today,” Okta reported, introducing it “need to have extra actively and forcefully compelled data from Sitel.”
The improvement will come as the City of London Police instructed The Hacker News previous 7 days that 7 folks related to the LAPSUS$ gang have been arrested and subsequently produced under investigation. “Our enquiries keep on being ongoing,” the company included.
Uncovered this posting interesting? Adhere to THN on Facebook, Twitter and LinkedIn to examine more exceptional material we article.
Some pieces of this post are sourced from:
thehackernews.com




 The ten biggest threats to your Windows PC in 2022
The ten biggest threats to your Windows PC in 2022