Threat actors associated with the notorious Emotet malware are regularly shifting their tactics and command-and-manage (C2) infrastructure to escape detection, according to new analysis from VMware.
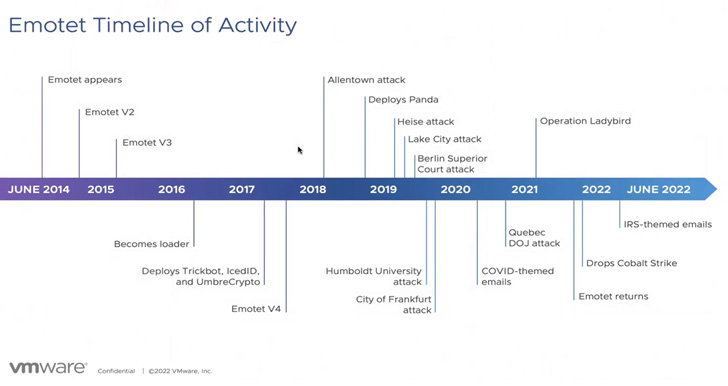
Emotet is the work of a menace actor tracked as Mummy Spider (aka TA542), rising in June 2014 as a banking trojan before morphing into an all-objective loader in 2016 which is able of delivering second-phase payloads such as ransomware.
Though the botnet’s infrastructure was taken down as aspect of a coordinated law enforcement operation in January 2021, Emotet bounced back again in November 2021 by way of another malware known as TrickBot.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Emotet’s resurrection, orchestrated by the now-defunct Conti staff, has considering the fact that paved the way for Cobalt Strike bacterial infections and, additional recently, ransomware attacks involving Quantum and BlackCat.

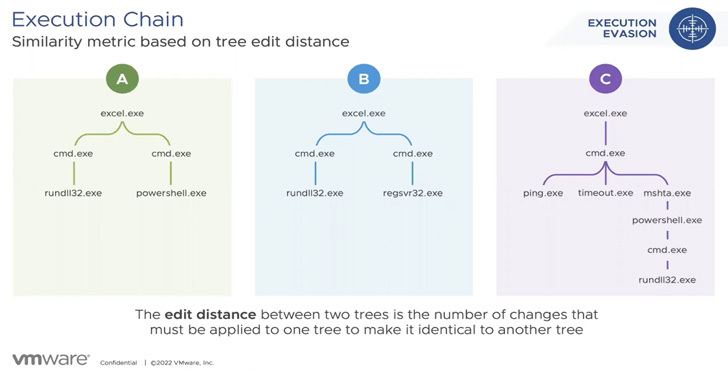
“The ongoing adaptation of Emotet’s execution chain is 1 purpose the malware has been thriving for so prolonged,” researchers from VMware’s Risk Evaluation Device (TAU) said in a report shared with The Hacker News.
Emotet attack flows are also characterised by the use of distinct attack vectors in an endeavor to keep covert for extended durations of time.
These intrusions ordinarily rely on waves of spam messages that produce malware-laced paperwork or embedded URLs, which, when opened or clicked, lead to the deployment of the malware.
In January 2022 on your own, VMware explained it noticed three different sets of attacks in which the Emotet payload was shipped by means of an Excel 4. (XL4) macro, an XL4 macro with PowerShell, and a Visual Simple Software (VBA) macro with PowerShell.
Some of these infection lifecycles had been also noteworthy for the abuse of a legit executable named mshta.exe to start a malicious HTA file and then drop the Emotet malware.
“Equipment these kinds of as mshta and PowerShell, which are at times referred to as living-off-the-land binaries (LOLBINs), are incredibly well known between threat actors due to the fact they are signed by Microsoft and trustworthy by Windows,” the scientists explained.
“This makes it possible for the attacker to execute a puzzled deputy attack, in which genuine applications are fooled into executing destructive actions.”
Further more analysis of virtually 25,000 exclusive Emotet DLL artifacts exhibits that 26.7% of all those were being dropped by Excel documents. As numerous as 139 exclusive program chains have been recognized.
Emotet’s re-emergence has also been marked by a improve in C2 infrastructure, with the menace actor operating two new botnet clusters dubbed Epochs 4 and 5. Prior to the takedown, the Emotet operation ran atop three separate botnets referred to as Epochs 1, 2, and 3.

On leading of that, 10,235 Emotet payloads detected in the wild among March 15, 2022, and June 18, 2022, reused C2 servers belonging to Epoch 5.
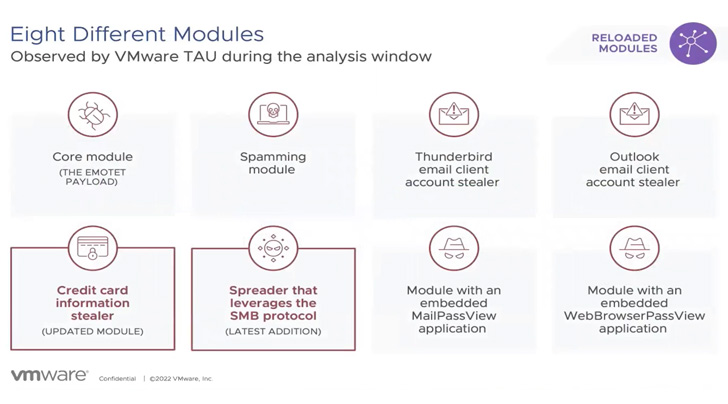
The variations to both of those the execution chains and C2 IP addresses aside, Emotet has also been spotted distributing two new plugins, a person which is intended to capture credit history card details from Google Chrome browser, and a spreader module that employs the SMB protocol for lateral movement.
Other sizeable elements include things like a spamming module and account stealers for Microsoft Outlook and Thunderbird email clientele.
A the vast majority of the IP addresses used to host the servers had been in the U.S., Germany, and France. In distinction, most of the Emotet modules had been hosted in India, Korea, Thailand, Ghana, France, and Singapore.
To shield against threats like Emotet, it is really advisable to carry out network segmentation, enforce a Zero Rely on design, and exchange default authentication mechanisms in favor of more powerful possibilities.
Identified this post interesting? Follow THN on Fb, Twitter and LinkedIn to browse more special content we write-up.
Some parts of this report are sourced from:
thehackernews.com


 Second Singtel subsidiary breach in a month sees customer and client data leaked
Second Singtel subsidiary breach in a month sees customer and client data leaked