Aspects have emerged about a substantial-severity security vulnerability impacting Service Location Protocol (SLP) that could be weaponized to launch volumetric denial-of-assistance attacks versus targets.
“Attackers exploiting this vulnerability could leverage vulnerable instances to start substantial Denial-of-Assistance (DoS) amplification attacks with a factor as substantial as 2200 moments, possibly earning it 1 of the premier amplification attacks at any time described,” Bitsight and Curesec researchers Pedro Umbelino and Marco Lux said in a report shared with The Hacker Information.
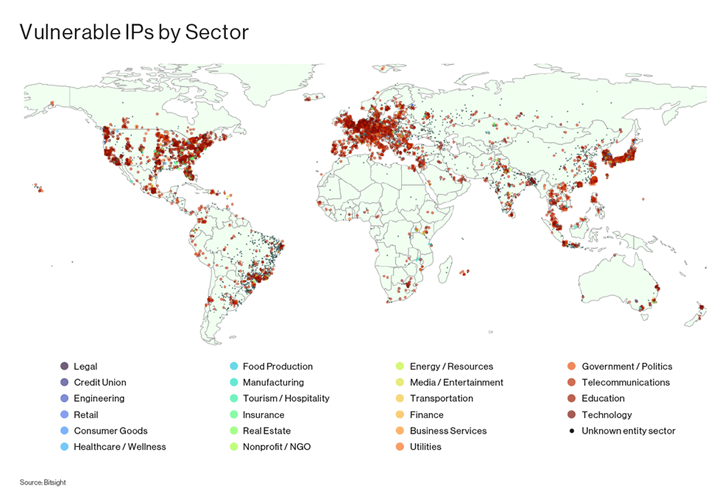
The vulnerability, which has been assigned the identifier CVE-2023-29552 (CVSS score: 8.6), is mentioned to affect additional than 2,000 international corporations and over 54,000 SLP situations that are obtainable in excess of the internet.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This involves VMWare ESXi Hypervisor, Konica Minolta printers, Planex Routers, IBM Integrated Administration Module (IMM), SMC IPMI, and 665 other merchandise sorts.
The prime 10 nations around the world with the most corporations possessing vulnerable SLP circumstances are the U.S., the U.K., Japan, Germany, Canada, France, Italy, Brazil, the Netherlands, and Spain.
SLP is a company discovery protocol that tends to make it attainable for computers and other equipment to discover providers in a regional region network this sort of as printers, file servers, and other network assets.
Effective exploitation of CVE-2023-29552 could make it possible for allow an attacker to take edge of inclined SLP situations to start a reflection amplification attack and overwhelm a concentrate on server with bogus targeted traffic.
To do so, all an attacker desires to do is find an SLP server on UDP port 427 and sign-up “products and services right up until SLP denies extra entries,” adopted by consistently spoofing a ask for to that assistance with a victim’s IP as the source deal with.
Forthcoming WEBINARZero Trust + Deception: Find out How to Outsmart Attackers!
Find out how Deception can detect advanced threats, stop lateral motion, and enhance your Zero Trust method. Join our insightful webinar!
Save My Seat!
An attack of this sort can make an amplification factor of up to 2,200, resulting in large-scale DoS attacks. To mitigate towards the danger, users are suggested to disable SLP on units immediately related to the internet, or alternatively filter visitors on UDP and TCP port 427.
“It is equally critical to implement solid authentication and access controls, allowing for only licensed users to accessibility the suitable network sources, with entry remaining closely monitored and audited,” the researchers stated.
Web security business Cloudflare, in an advisory, reported it “expects the prevalence of SLP-based DDoS attacks to increase considerably in the coming weeks” as menace actors experiment with the new DDoS amplification vector.
The conclusions appear as a now-patched two-year-aged flaw in VMware’s SLP implementation was exploited by actors involved with the ESXiArgs ransomware in prevalent attacks earlier this 12 months.
Discovered this article appealing? Observe us on Twitter and LinkedIn to browse far more exclusive articles we post.
Some pieces of this short article are sourced from:
thehackernews.com

 Iranian Hackers Launch Sophisticated Attacks Targeting Israel with PowerLess Backdoor
Iranian Hackers Launch Sophisticated Attacks Targeting Israel with PowerLess Backdoor