Telecommunication company suppliers in the Center East are staying focused by a previously undocumented danger actor as portion of a suspected espionage-connected campaign.
Cybersecurity corporations SentinelOne and QGroup are monitoring the action cluster beneath the former’s do the job-in-progress moniker WIP26.
“WIP26 depends closely on general public cloud infrastructure in an endeavor to evade detection by generating destructive targeted traffic look legit,” scientists Aleksandar Milenkoski, Collin Farr, and Joey Chen claimed in a report shared with The Hacker Information.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This features the misuse of Microsoft 365 Mail, Azure, Google Firebase, and Dropbox for malware delivery, information exfiltration, and command-and-management (C2) needs.
The preliminary intrusion vector used in the attacks entails “precision targeting” of personnel by means of WhatsApp messages that comprise hyperlinks to Dropbox backlinks to supposedly benign archive information.
The data files, in fact, harbor a malware loader whose core feature is to deploy custom made .NET-centered backdoors these as CMD365 or CMDEmber that leverage Microsoft 365 Mail and Google Firebase for C2.
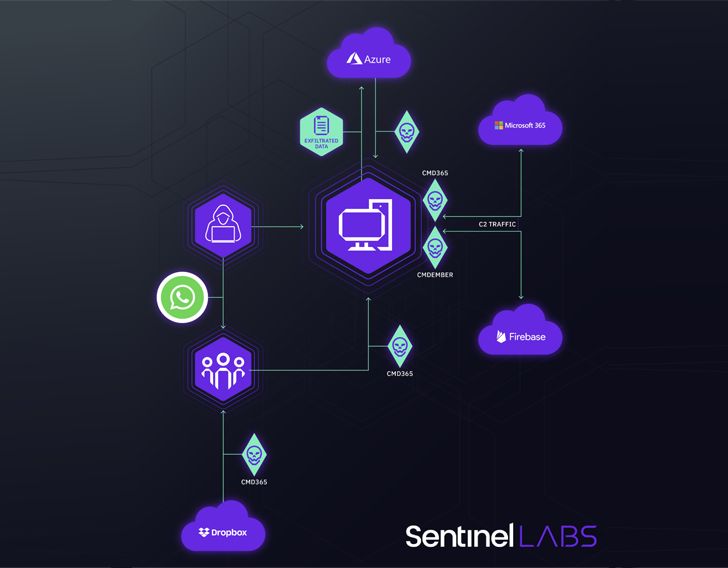
“The key operation of CMD365 and CMDEmber is to execute attacker-supplied system commands using the Windows command interpreter,” the scientists explained. “This ability was used to conduct a wide variety of routines, this kind of as reconnaissance, privilege escalation, staging of added malware, and details exfiltration.”
CMD365, for its portion, will work by scanning the inbox folder for specific e-mail that start out with the issue line “input” to extract the C2 commands for execution on the infected hosts. CMDEmber, on the other hand, sends and receives knowledge from the C2 server by issuing HTTP requests.
Transmitting the facts – which comprises users’ non-public web browser information and facts and details about higher-value hosts in the victim’s network – to actor-managed Azure scenarios is orchestrated by suggests of PowerShell instructions.
The abuse of cloud companies for nefarious ends is not unheard of, and the hottest marketing campaign from WIP26 implies ongoing tries on the portion of menace actors to evade detection.
This is also not the initially time telecom vendors in the Center East have appear below the radar of espionage teams. In December 2022, Bitdefender disclosed specifics of an operation dubbed BackdoorDiplomacy aimed at a telecom corporation in the area to siphon beneficial facts.
Identified this article intriguing? Stick to us on Twitter and LinkedIn to browse extra special information we article.
Some pieces of this write-up are sourced from:
thehackernews.com

 ESXiArgs Ransomware Hits Over 500 New Targets in European Countries
ESXiArgs Ransomware Hits Over 500 New Targets in European Countries