Scientists have disclosed a novel strategy by which malware on iOS can attain persistence on an contaminated device by faking its shutdown approach, making it extremely hard to physically figure out if an iPhone is off or in any other case.
The discovery — dubbed “NoReboot” — arrives courtesy of cell security company ZecOps, which discovered that it truly is attainable to block and then simulate an iOS rebooting procedure, deceiving the consumer into believing that the phone has been run off when, in truth, it truly is nevertheless running.
The San Francisco-headquartered enterprise referred to as it the “supreme persistence bug […] that simply cannot be patched mainly because it is really not exploiting any persistence bugs at all — only playing tips with the human intellect.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
NoReboot performs by interfering with the routines utilized in iOS to shutdown and restart the machine, effectively avoiding them from ever going on in the very first position and permitting a trojan to obtain persistence with no persistence as the product is never basically turned off.

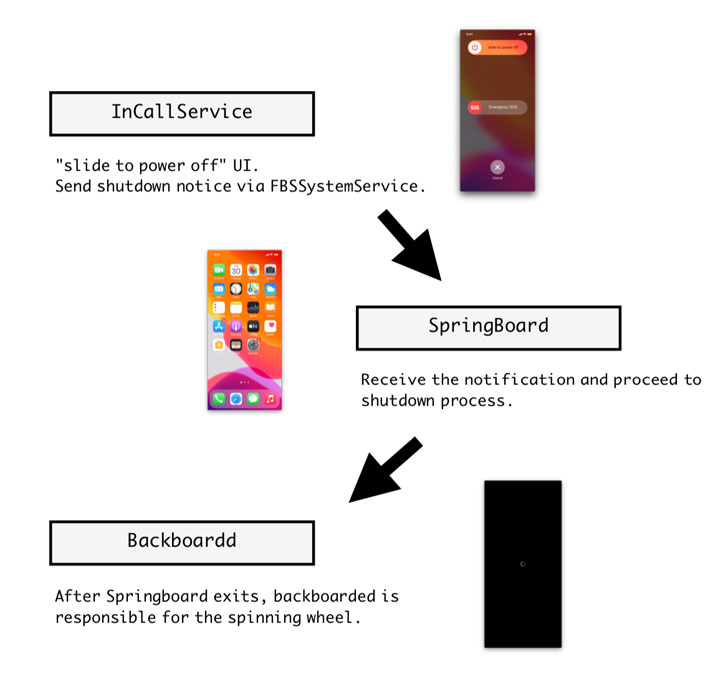
This is completed by injecting specifically crafted code onto a few iOS daemons, specifically the InCallService, SpringBoard, and Backboardd, to feign a shut down by disabling all audio-visual cues involved with a driven-on gadget, which include the monitor, seems, vibration, the camera indicator, and touch suggestions.
Put otherwise, the notion is to give the impact that the system has been shut down without really shutting it down by hijacking the function that’s activated when the consumer concurrently presses and holds the side button and a single of the volume buttons, and drags the “slide to electric power off” slider.
“Regardless of that we disabled all bodily comments, the phone continue to continues to be completely useful and is capable of protecting an energetic internet link,” the scientists explained. “The destructive actor could remotely manipulate the phone in a blatant way without stressing about staying caught simply because the consumer is tricked into wondering that the phone is off, either remaining turned off by the sufferer or by malicious actors applying ‘low battery’ as an excuse.”
The malware pressure then forces the SpingBoard, which refers to iOS’s graphical person interface, to exit (as opposed to the full OS), adopted by commanding the BackBoardd, the daemon that handles all contact and actual physical button simply click functions, to exhibit the Apple symbol result should really the person choose to change the managing phone back on, though the destructive code continues to persist.
What is far more, this method could be theoretically extended to manipulate a drive restart related with an iPhone by intentionally resulting in the Apple logo to appear a couple seconds previously when these an celebration is recorded through the Backboardd, fooling the target into releasing the aspect button without the need of truly triggering a force restart.
Despite the fact that no malware to day has been detected or publicly documented making use of a system resembling NoReboot, the results highlight that even the iOS restart procedure isn’t really immune to becoming hijacked when an adversary has received accessibility to a goal product, anything which is effectively inside the access of country-point out teams and cyber mercenaries alike.
“Non-persistent threats obtained ‘persistency’ without the need of persistence exploits,” the scientists concluded. A evidence-of-strategy (PoC) exploit demonstrating NoReboot can be accessed by means of GitHub listed here.
Uncovered this report appealing? Adhere to THN on Facebook, Twitter and LinkedIn to go through extra unique material we write-up.
Some parts of this post are sourced from:
thehackernews.com



 Crypto Firm Pulls the Rug from Under Investors with $10m Scam
Crypto Firm Pulls the Rug from Under Investors with $10m Scam