A software bug introduced in Apple Safari 15’s implementation of the IndexedDB API could be abused by a malicious internet site to monitor users’ on the web activity in the web browser and worse, even expose their id.
The vulnerability, dubbed IndexedDB Leaks, was disclosed by fraud defense application corporation FingerprintJS, which reported the issue to the iPhone maker on November 28, 2021.
IndexedDB is a small-stage JavaScript application programming interface (API) provided by web browsers for managing a NoSQL databases of structured data objects such as documents and blobs.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“Like most web storage solutions, IndexedDB follows a very same-origin coverage,” Mozilla notes in its documentation of the API. “So when you can obtain saved details inside of a area, you can not access information throughout different domains.”
Similar-origin is a elementary security mechanism that guarantees that assets retrieved from distinct origins — i.e., a combination of the plan (protocol), host (area), and port amount of a URL — are isolated from just about every other. This successfully suggests that “https://illustration[.]com/” and “https://case in point[.]com/” are not of the similar origin since they use diverse techniques.
By restricting how a script loaded by just one origin can interact with a useful resource from another origin, the concept is to sequester potentially malicious scripts and cut down potential attack vectors by stopping a rogue site from jogging arbitrary JavaScript code to read through data from a different domain, say, an email provider.
But that is not the circumstance with how Safari handles the IndexedDB API in Safari throughout iOS, iPadOS, and macOS.
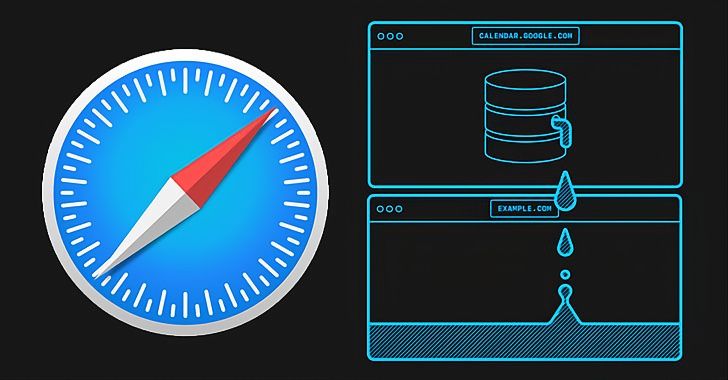
“In Safari 15 on macOS, and in all browsers on iOS and iPadOS 15, the IndexedDB API is violating the similar-origin plan,” Martin Bajanik claimed in a produce-up. “Each individual time a site interacts with a databases, a new (empty) database with the similar identify is created in all other lively frames, tabs, and windows in the similar browser session.”
A consequence of this privacy violation is that it enables web sites to study what other websites a person is checking out in distinctive tabs or windows, not to point out precisely detect people on Google expert services products and services like YouTube and Google Calendar as these internet websites create IndexedDB databases that include things like the authenticated Google Consumer IDs, which is an inside identifier that uniquely identifies a solitary Google account.
“Not only does this imply that untrusted or malicious internet websites can study a user’s identity, but it also enables the linking alongside one another of multiple separate accounts used by the identical consumer,” Bajanik said.
To make issues worse, the leakage also has an effect on Personal Browsing manner in Safari 15 ought to a person go to many unique internet sites from within just the identical tab in the browser window. We have reached out to Apple for even more comment, and we’ll update the tale if we listen to back again.
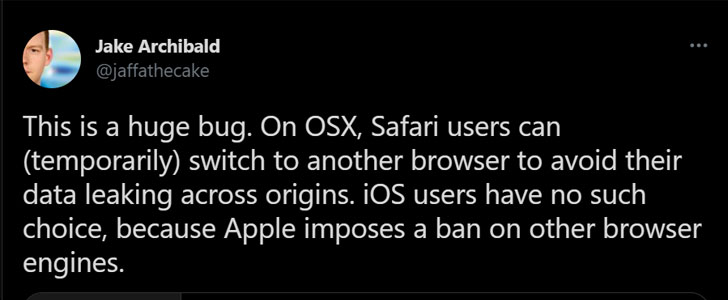
“This is a large bug,” developer advocate for Google Chrome Jake Archibald tweeted. “On OSX, Safari consumers can (briefly) swap to an additional browser to stay clear of their facts leaking throughout origins. iOS people have no this sort of preference, for the reason that Apple imposes a ban on other browser engines.”
Uncovered this post interesting? Follow THN on Facebook, Twitter and LinkedIn to read through a lot more distinctive material we publish.
Some areas of this posting are sourced from:
thehackernews.com


 A New Destructive Malware Targeting Ukrainian Government and Business Entities
A New Destructive Malware Targeting Ukrainian Government and Business Entities